First of all, knowing what you understand and expect from the concept of “pentest” will help you in this process. Because this was afterwards by buying a service you didn’t know what it was? You may have to ask questions such as whether I have paid so much money for this job or why I did not have these systems checked. Different expressions such as pentest, penetration test and penetration test mean the same thing.
What is Penetration Test?
Penetration testing (Pentest) is carried out to find out whether the systems of companies and institutions are safe by testing or having their systems aggressive point of view. During penetration testing, it performs an infiltration simulation by companies skilled in the field. During the penetration test, various attack methods are tried and infiltrated into the system like a real attacker.
The person or persons who perform the penetration test are informed about the openings of the company before the real attackers by reporting the openings they find. In this way, companies become aware of the parts that are open in their systems and close the security gaps in these parts.

What are Pentest Types?
Pentest is divided into three depending on the target, the vector, the attack to be simulated, and the system.
Internal Network (Internal) Penetration Test: In this type of penetration test, an answer is sought to the question of which data and/or systems can be accessed through the open systems of the relevant institution.
External Network (External) Penetration Test: In this type of penetration test, an answer is sought to the question of which data and/or internal systems can be accessed through the open systems of the relevant institution.
Web Application Penetration Test: The answer to the same question is sought with External Network Penetration Tests, but our focus is on web applications.
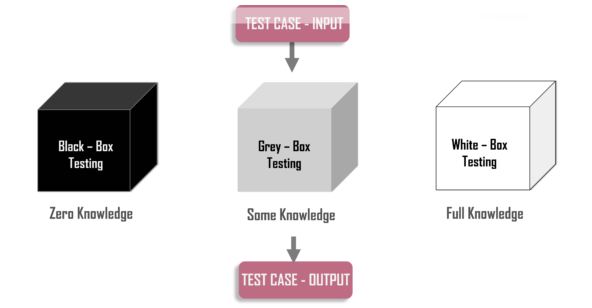
Penetration Test Methods
Black Box Pentest: In this type of test, the penetration tester is not given any information about the systems. Like a real hacker, a penetration test is carried out with information accessible only to everyone.
White Box Pentest: In this test, the penetration tester is given full information about the operating systems in the company. The aim here is to identify the damage that the person working in the firm or the attacker who has realized the infiltration and has been waiting in the system for a while and grasps the structure, can cause damage to the firm.
Gray Box Pentest: The grey box penetration test is in the middle of both the white box and the black box test. Penetration testing specialist is informed about the system by an unauthorized user.
Types of Penetration Test:
- Network Penetration Tests
Internal Network Penetration Test
External Network Penetration Test - Web Application Penetration Tests
- Mobile Application Penetration Tests
- Critical Infrastructure Systems Penetration Tests
- DDoS and Load Test
- Wireless Network Penetration Test
- VoIP Infrastructure Penetration Test
- Social Engineering Penetration Test
Penetration Test Methodologies
There are ways to be followed by some institutions and organizations when performing penetration testing. These methodologies are widely used by pentest specialists.
- OWASP (Open Web Application Security Project)
Web Security Test Methodology
Mobile Application Security Testing Methodology
IoT Safety Test Methodology - OSSTM (The Open Source Security Testing Methodology)
- ISSAF (Information Systems Security Assessment Framework)
- NIST SP800-115
- PTES (Penetration Testing Execution Standard)
- Fedramp
What is Vulnerability Assessment?
Vulnerability scanning is a test designed to identify all possible gaps in a system. Automated tools (Nessus, Nmap, Qualys etc.) are generally used for this method. The main purpose in the vulnerability scanning is to take the general security image of the system being scanned instantly. Not all of the findings resulting from this method, which warns us against all possible security threats, may indicate a serious threat. However, this does not mean that it should not be taken seriously. The important thing for us is to decide which findings are a real threat to our system.
Another thing that is controlled in this method is the compliance processes. Companies’ HIPAA, PCI, SOX etc. It examines its status according to many compatibility standards accepted worldwide.
Penetration Test Steps
There is a basic roadmap to follow when performing the pentest. We can handle the penetration test process in 7 steps. These steps are as follows.
1. Scoping
The scope of the pentest is determined by the agreement between the company that will perform the penetration test and the company. The type and number of systems to be tested are determined by the authority of the institution where the test will be carried out.
2. Gathering Information
This section collects information about the target. Pentest experts often try to gather as much information as possible about target systems. At this stage, certain methods are mainly used. In this section, information about the systems is collected using tools such as Social Media, Shodan, Nmap, Nessus, Dig, and information about the company employees and the organization can be collected using OSINT methods.
3. Vulnerability Scan
In order to ensure information security, it is an important step to identify risks effectively and identify vulnerabilities that may arise from these risks. Vulnerability scanning is the part of detecting deficits on the system. In this section, misconfiguration of running services or weaknesses on unsafe applications can be given as examples. In this section, Nmap, Sqlmap, Nikto style tools are used.
4. Abuse
In this section, it is tried to obtain authority on the system by using the information we gathered before the pentest and the weaknesses found. The aim is to bypass measures such as firewall, intrusion detection and blocking systems on the systems and to access the resources on the system.
5. Upgrade Authority
The purpose of the delegation phase is to seize a more authorized user account from the user obtained on a system seized. In this step, many methods such as applications running on the target system, kernel version or detecting user password hash are applied.
6. Infiltration into Other Networks
At this stage, after accessing one user, the accounts of other users on the network are tried to be compromised. In this process, tests are made to listen to the network and reading is done on certain databases where users’ session information is kept and other users are tried to be captured.
7. Reporting
Reporting is the last and most important stage of the pentest in. At this stage, details such as openings and solution suggestions, possible effects of openings, how the openness can be captured, distribution graphics of openings, and attack methods applied are presented to the institution receiving service.
Why Should We Have A Penetration Test?
Checking and reporting security vulnerabilities in the information systems you have is the first step in proactive security. Because no matter how much security you pay attention, there is no limit to the techniques that attackers will use to exploit the system.
The possibilities vary according to the imagination and knowledge levels. There is a possibility that something might be overlooked. For these reasons, it would be beneficial for you to get your hackers tested with your own security without hacking. In addition, standards such as PCI and HIPAA require Pentest.
How Should the Plan of the Penetration Test Project Be?
In order to get as much efficiency as possible from the penetration test work to be carried out, a plan should be made here, as in every job. Preparing your pentest plan by at least answering the following questions will ensure you get a high level of efficiency.
- What will be the scope of the Penetration Test? (White Box, Gray Box, Black Box).
- What kind of penetration test do I want? (Internal Pentest, External Pentest, Web Application Pentest).
- Who do I take the tests to?
- How often will I have it done?
- Should risky systems and services be out of scope or would I like to accept the risk and see the result?
- Will DDOS tests be carried out within the scope of Pentest?
What Should I Pay Attention Regarding Pentest Company Selection?
No matter how much you trust the company you will be making pentest – you must definitely have a signed and clear NDA among you – you will still be able to log all the actions that the company will take in terms of securing your business. So how do you do that? By requesting the IP address information to be pentest by the company, all traffic coming from these IP addresses can be tracked by Snort, Tcpdump etc. you can log it using software that can record traffic. In particular, the most critical information on web traffic will appear here. With Snort, traffic can be recorded in such a way that it can be easily understood afterwards. Apart from this, the issues you need to pay attention to are;
- Ask for CVs of employees who will be testing at the company.
- If there are any, choose the employees who will perform the test to have technical certifications (CEH, OSCP etc.).
- Make sure that the employees who will perform the test are employees of the company.
- Contact the firm’s previous references and ask a few of them for their satisfaction.
- If possible, ask the companies to attack these systems and find the openness you know by installing trap systems to determine the technical capacity before choosing the firm.
- Ask the company for sample reports on the tests it has done before.
- Request that tests be run from specific IP addresses and that these IP addresses are notified to you.
- Ask the firm about the standards they use for testing.
- Ask the company to write down all the tools used in the test report.
- Make sure that the pentest offer is not too low compared to others.
- Is the penetration test job the company’s private business or is it just doing it? This query will give you tips on the company’s competence on the subject.
What Should I Expect from a Pentest Firm?
- Two different reports are specific to managers and technical workers.
- The reports are readable and understandable.
- Instant reporting of critical level vulnerabilities discovered during tests.
- Encrypted transmission of the pentest report.
- Providing solutions for how to close the discovered vulnerabilities.
What Way Should I Follow After Pentest?
The more important it is to have a pentest, the more important it is to take action and evaluate its results. Unfortunately, the common mistake is just doing Pentest / having it done, examining the report and closing very urgent deficits. It is frequently encountered that the openings are not closed after the pentest and the same openings reappear in the next pentest study. In order for the added value of the work carried out to be high, at least the following items are recommended:
- Sharing Pentest reports with senior management and getting management support.
- Presenting the results to management within the scope of a risk map, not as simple explanations.
- Examine the report in detail and determine who is interested in each opening.
- Meeting with system administrators and software developers and sharing the results.
- Tracking the closure of openings.
- Determination of the date of the next pentest.
What should be the road map I should follow in order to improve myself about Pentest?
In order to improve yourself on Pentest, you must first have a curious structure in this field. Having a serious curiosity about informatics issues and having a mindset that has tampered with breaking the systems will lead you to the front row at the beginning of the road. Otherwise, your job is a little difficult. Because being “Pentester” means thinking what others can’t think, doing what they can’t and being different.
The easiest learning of this job is individual studies, trying to learn by experimenting on your own, to be wrong, to be wrong again and to learn the correct way. Training can be supportive in this regard. It can transfer you the path you will travel in 5-6 months to you in a week or two, but it will never fully train you, it will only “guide” you. Membership to security lists where Pentest topics are discussed is also a method that will bring you directly to ready-made information sources and allows you to follow the agenda.
Besides, having knowledge about the use of the Linux operating system and knowledge of basic network security will make you 1 step forward in Pentest. If you want to do this job seriously, the more knowledge and experience you have on these two issues, the more difference you can make against your competitors.
What software is used for Pentest?
Two types are used, open code and commercial software.
Open Code Pentest Software:
- Nmap, Nessus, Metasploit, Inguma, Hping, Webscarab, John the Ripper, W3af. Are some of them. Most Pentest software, known as open code, comes installed with the Kali Linux distribution.
Commercial Pentest Software:
- Immunity Canvas, Core Impact, HP Web Inspect, Saint Security Scanner
Besides these tools, there are “Pentest Methodologies” as important as tools. These should be known and used as well as tools. These; OWASP Guide, NIST, ISSAF, OSTTM