Let’s start by applying some tests on the target; Let’s scan the target network using Nmap. With IPs, we determined which ports are working on the services (our attractive ports: 80,443) Waffit (Wafw00f) or which services are protected by the firewall by running the impervadetect script. Applying exploit to unprotected IPs looks great for us.
Let’s go to bypass method immediately:
However, most WAF can understand this method, giving the error “Forbidden”.
Let’s try the previous method by writing some letters of the commands in lower case. However, this method can be captured by some WAFs.
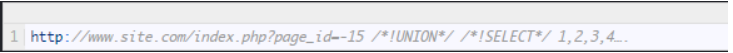
Let’s combine the commands in the previous method and try. This method is not detected by most WAFs.
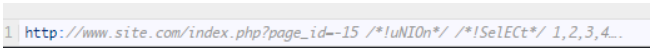
Let’s change the locations of keywords. Most WAF deletes “UNION SELECT” statements as soon as they detect them in the URL, we can use this function to exploit.
http://www.site.com/index.php?page_id=-15 UNIunionON SELselectECT 1,2,3,4…. (“Union” and “select” will be deleted, the result will be “UNION SELECT”)
This method does not work in all firewalls, it deletes “UNION” and “SELECT” commands as soon as they detect them.
There is an SQLmap tool that contains the bypass script in the tamper folder that sends the manual changes we made so far to the opposite system by arranging the “union” and “select” commands in random capital letters.

Most firewalls are developed in C / C ++ language and we can crash the firewall using buffer overflow.
We can crash the WAF when we apply the following commit. If we get 500 answers, we can exploit the buffer overflow method.
Let’s replace the characters with the hex values in the next method. In the example here, we replaced some characters with the hex (url-encoded) values in the “union and select” commands.
You can reach the site that gives the hex values of the characters from the link. http://www.swingnote.com/tools/texttohex.php
It replaces the whitespace with the “*” sign below. If the firewall deletes the “*” sign, the result will be: 15 + union + select…, we can find similar functions and exploit them.