Due to the fact that personal data belonging to previous phone owners are not completely cleared from the phone during the second-hand phone purchases made in the world, it can be brought back by the new owner of the phone data with a few transactions on the phone.
As a result of the researches, it was proved that the data in 1 of the 6 second-hand SD cards sold were not deleted or returned after a few transactions. In order to understand the importance of the situation, some of the data obtained after the studies on SD cards are given below:
- Directory Information
- Credentials and Social Security Numbers
- Received-Sent Emails
- Photos
- Internet Browser Histories
- Passport Photos, Copies
- Bank account information
- And many other qualified data files
When users delete a file or photo from the phone and then clean the trash, they think the data has been completely erased from digital media. But technically, this is not the case. Each photo, email, or file on our phones actually consists of 0 and 1 bits, which we call binary. For example; When we delete a photo on our phone, the reference records that enable the deleted photo to be found and opened by the processor are deleted. However, the 0’s and 1’s that make up the photo still seem to be somewhere in the phone memory. It continues to remain on the phone until another data is written instead of the 0 and 1 bits of the deleted photo on the memory.

How is Data Retrieved?
How can I get back the remaining 0 and 1 bits after deleting photos or files of high size? You might think, “This should be quite difficult,” but the procedures are not that challenging. It is possible to easily restore data on Android devices with 3rd party software written by developers. All that is needed to run many simple and easy-to-use software that performs data recovery and retrieval operations; The device is rooted, that is, access to the root directories of the phone. But this process can also be done easily.
Unfortunately, not using Android does not save you. It is quite easy to do the same with phones with IOS operating system. In other words, you do not need to have good technical knowledge in order to retrieve the data deleted from your phone. With a few videos to watch and internet calls made, a Script Kiddie can also reveal your sensitive data.

So what kind of precaution should we take?
Shouldn’t we sell our phones? Of course, you can sell it if you wish. But first, you need to make sure that you have taken the following steps:
- With the developing technology, even if no SD cards are used in many phones, be sure to check if there is an SD card in the phone you will sell. If there is, you can destroy the SD card (instead of dealing with old 0 and 1 bits), instead of resetting the SD card (if you are not going to use the SD card again). Because it will not make much sense to hand over a memory card that contains a lot of data to you with your hands.

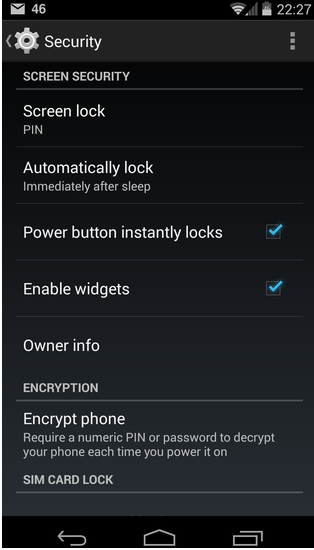
- If you are an Android user, you can encrypt your phone under the “Settings> Security” tab. Deleting your data after encrypting it for the first time will provide another step for you due to the change of 0 and 1 bits. Of course, you should never forget to return your phone to “Factory Settings” after these processes.
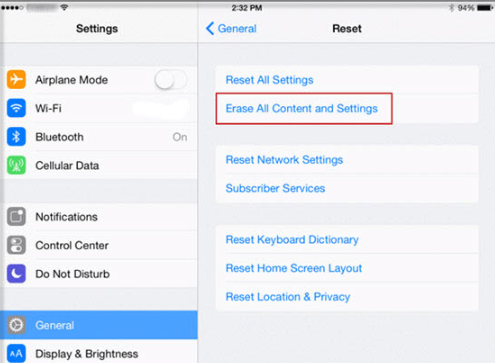
- If you are an iOS user, you can reset your phone to factory settings by clicking the “Erase All Content and Settings” button, not the “Reset All Settings” button while resetting your phone.
- Finally, for the 0 and 1 bits stored in your phone’s memory, you can also use tools that allow overwriting operations to replace all bits in the device memory.
It is not possible for you to say “I have definitely cleared my data from digital media” after performing the steps mentioned. Although it is used as a classic term, it knows that there is no 100% security, and acting accordingly will make you more secure against potential cyber-attacks.




