Ping / ICMP requests are the most common tools used to determine whether a device is active in the network. When installing the Windows Server system, the firewall is turned on for security reasons and does not respond to ping requests. Although the easiest way to respond to ping requests is to turn off the firewall entirely, this situation is never recommended and leaves the system completely vulnerable if done.
The following steps can be followed to answer only ping/ICMP requests through the firewall.
Open the firewall settings by following Start> Windows Administrative Tools> Windows Firewall with Advanced Security.

The screen that opens with the “Inbound Rules” button is displayed on the screen that opens.

In the “Inbound Rules” screen, we switch to the new rule creation screen on the firewall with the “New Rule …” button.

On the “New Inbound Rule Wizard” screen, we select the “Custom” option and move on to the next screen.

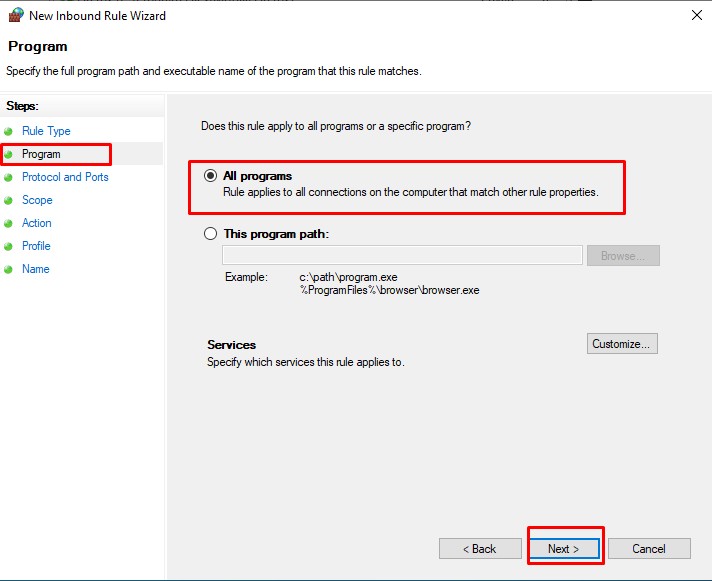
We move to the next screen with the option “All programs” in the “Program” tab of the “New Inbound Rule Wizard” screen.
On the “New Inbound Rule Wizard” screen, we switch to the screen where we will select the “Protocol type” option “ICMPv4” in the “Protocol and Ports” tab and select which of the ICMP requests will be answered with the “Customize …” button.
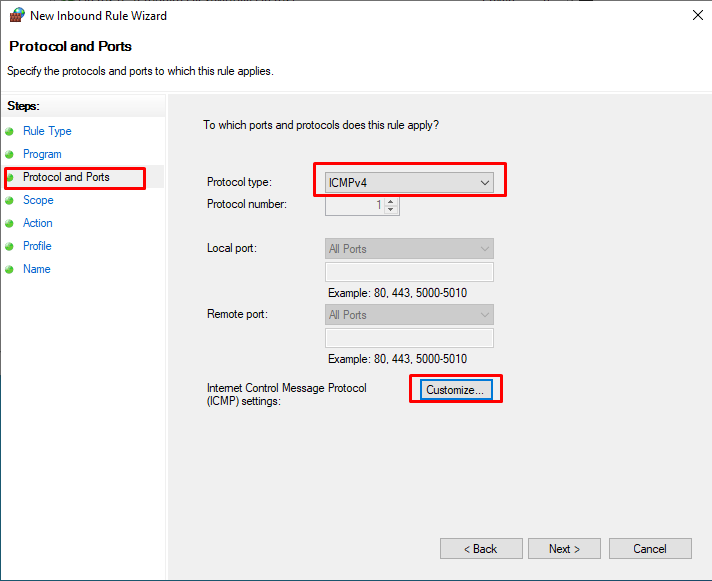
On the “Customize ICMP Settings” screen, select “Echo Request” on the “Specific ICMP types” tab and click the “OK” button.

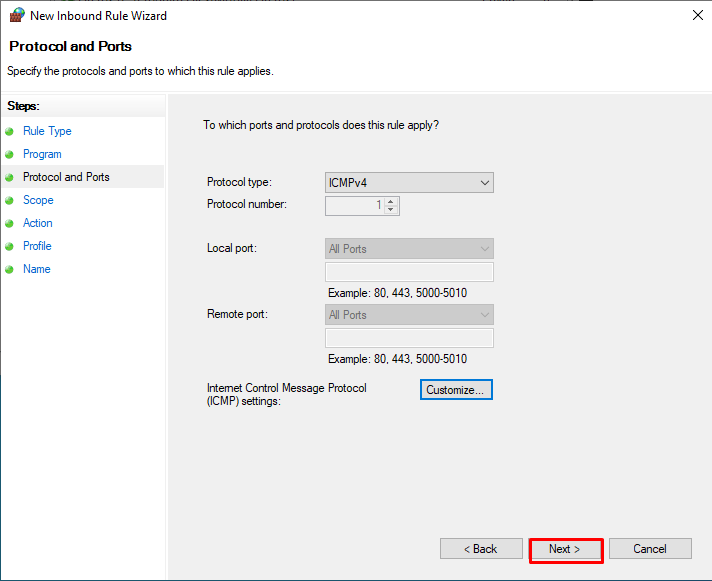
After making the settings on the “Protocol and Ports” tab of the “New Inbound Rule Wizard” screen, we click the “Next” button.
On the “New Inbound Rule Wizard” screen, we leave the settings in the “Scope” tab and click the “Next” button.

In the “Action” tab, we leave the settings in the same way and click the “Next” button.

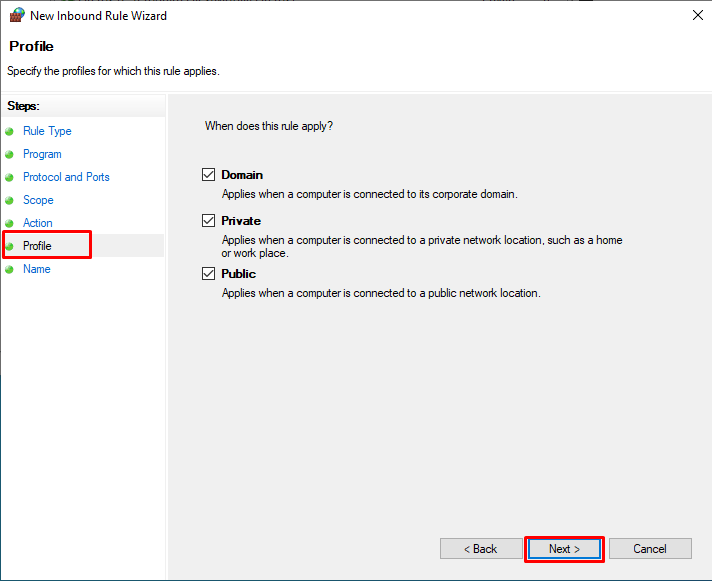
In the “Profile” tab, we leave the settings in the same way and click the “Next” button.
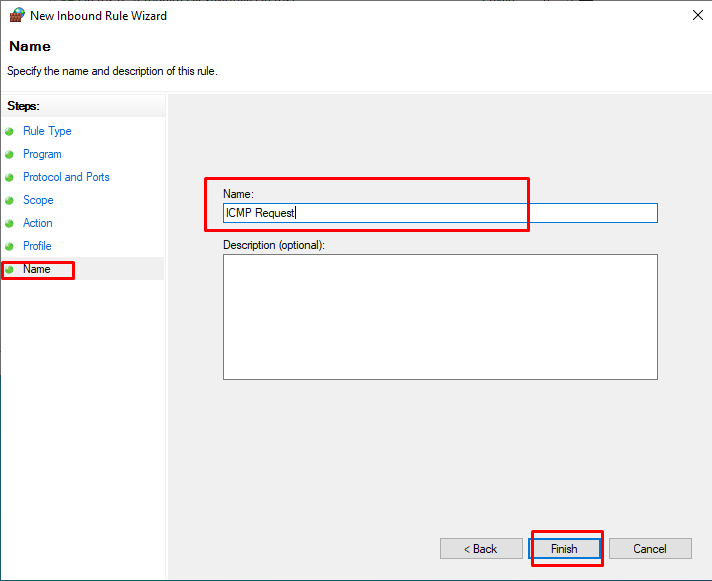
After giving a suitable name and explanation to the rule to be created on the “Profile” screen, we have completed the process with the “Finish” button.
Note: The point to be taken into consideration when performing security-related operations; Rather than allowing the entire system to be stuck, it is only necessary to define sufficient authority.




