Metasploit is an open-source exploit framework. Metasploit; It can run in Linux, Windows and Mac-OS environments. With Metasploit, not only a direct attack is made. You can make various backdoor files and attack the target system with them. For this, you may need to install services such as “IIS” or “apache” to your operating system. Abuse codes written for vulnerabilities can be found at https://www.exploit-db.com/. Metasploit is a framework that includes scanning modules, antivirus circumvention models and currently exploits. Kali Linux or Backtrack Linux distributions come with Metasploit installed. There are also auxiliary tools required for reverse engineering in Metasploit. Metasploit 2.0 version was developed in “Perl” language, while Metasploit 3.0 and later versions were developed in “Ruby” language. Apart from Metasploit, exploit codes can also be downloaded from sites such as https://packetstormsecurity.com/ and https://www.securityfocus.com/. However, the codes to be downloaded should be used after careful examination, as they may contain backdoor or codes that will leak information. Otherwise, you may encounter severe damages.
Exploit Database
Metasploit has a practical interface and the current version includes more than 2600 exploits, more than 1090 auxiliary, more than 560 payloads, 45 encoders, 10 nops and 7 evasions. We will explain these concepts more clearly below.
Metasploit Framework
Exploit: These are vulnerabilities used to achieve the goals by using the weaknesses of the service or applications running on the target system.
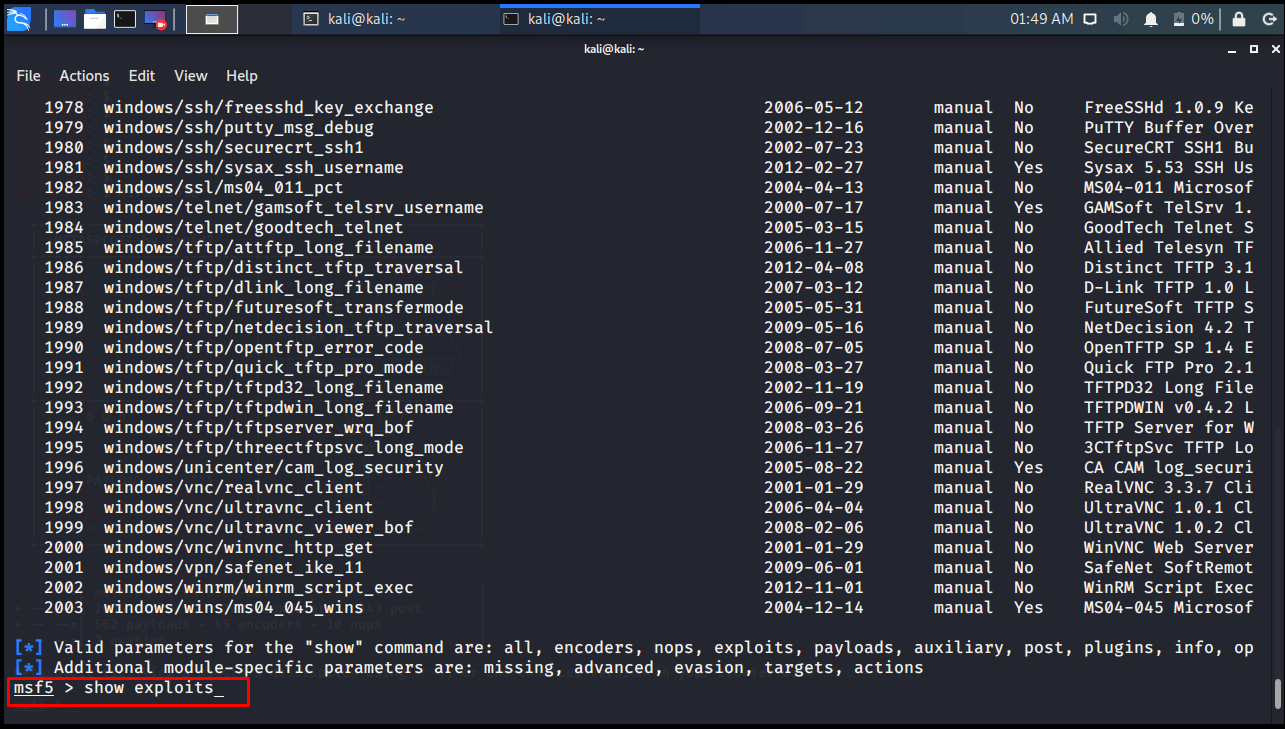
msf5 > show exploits
Payload: While accessing the target system, it is loaded into the memory of the target machine and enables the hacker to perform the actions he/she wants. For example, the code set that allows you to take a webcam image, get a hashdump, turn on a microphone, open a keylogger, take a screenshot and lock the keyboard, and so on, is called payload. Examples of these payloads are meterpreter, DLL injection and passivex.
msf5 > show payloads
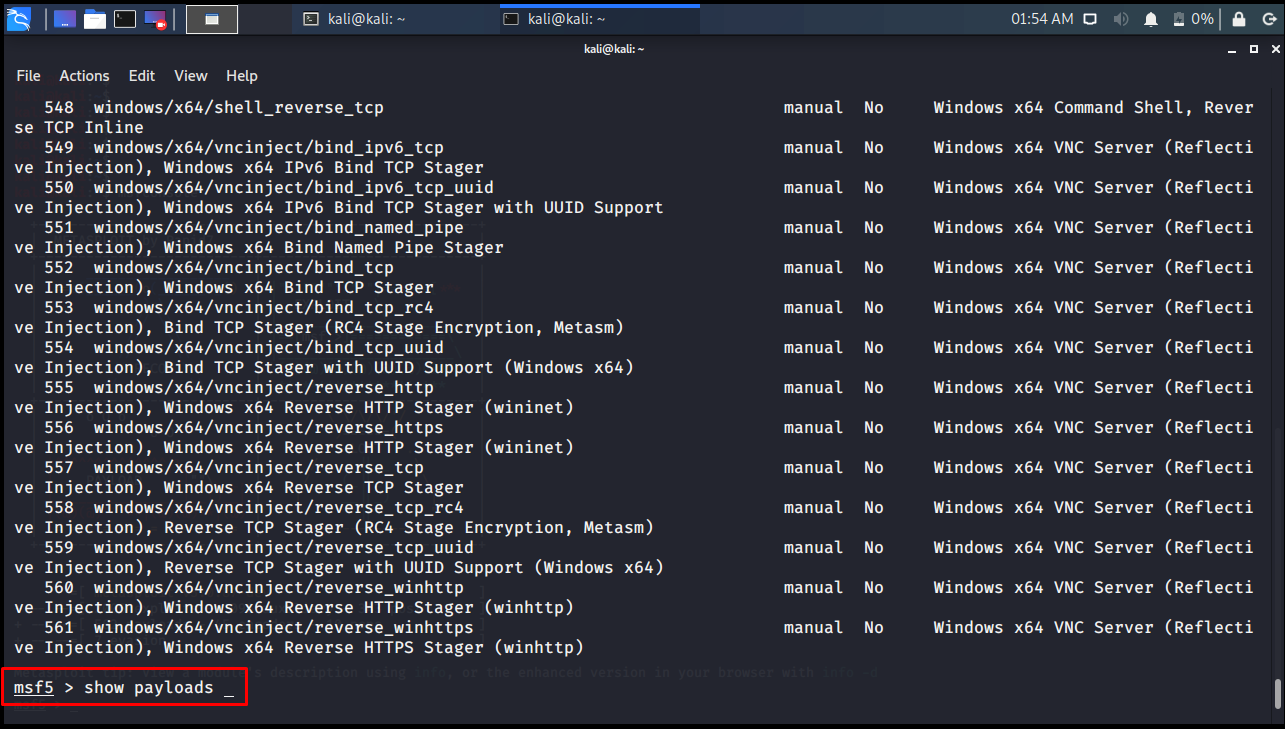
Auxiliary: Additional program lets developed for modules are auxiliary tools. Collecting pre-exploit information is used to advance the target system after exploit. One of the most used tools in Metasploit is Aux modules.
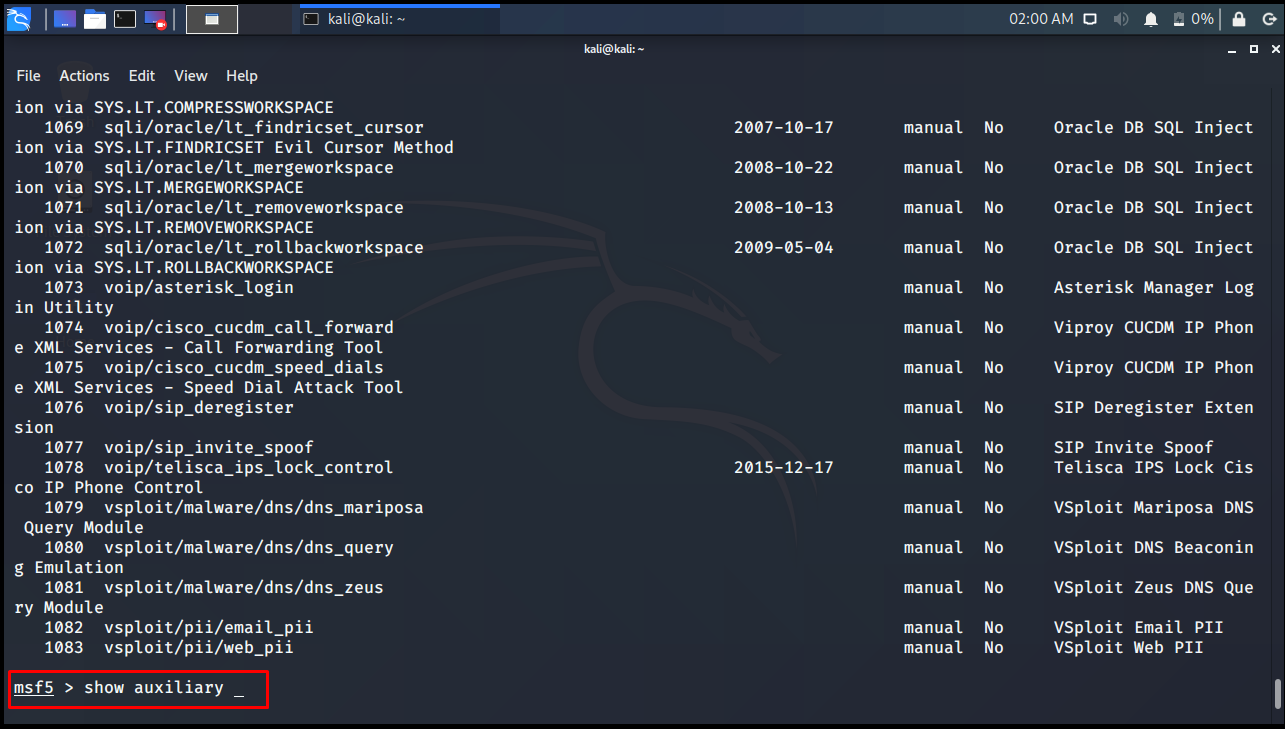
msf5 > show auxiliary
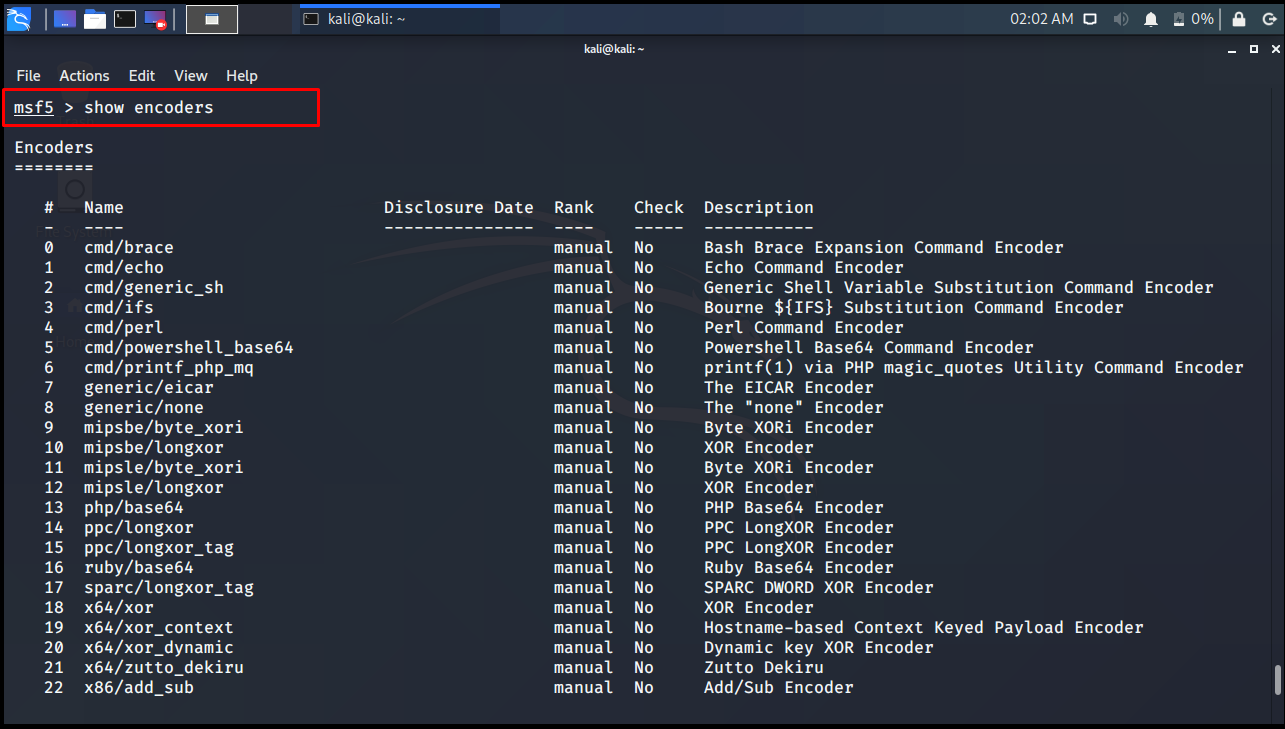
Encoders: Used to bypass antivirus and security devices. IPS is used to bypass security devices such as IDS. It is an additional module that can be used to render a malware unrecognizable.
msf5 > show encoders
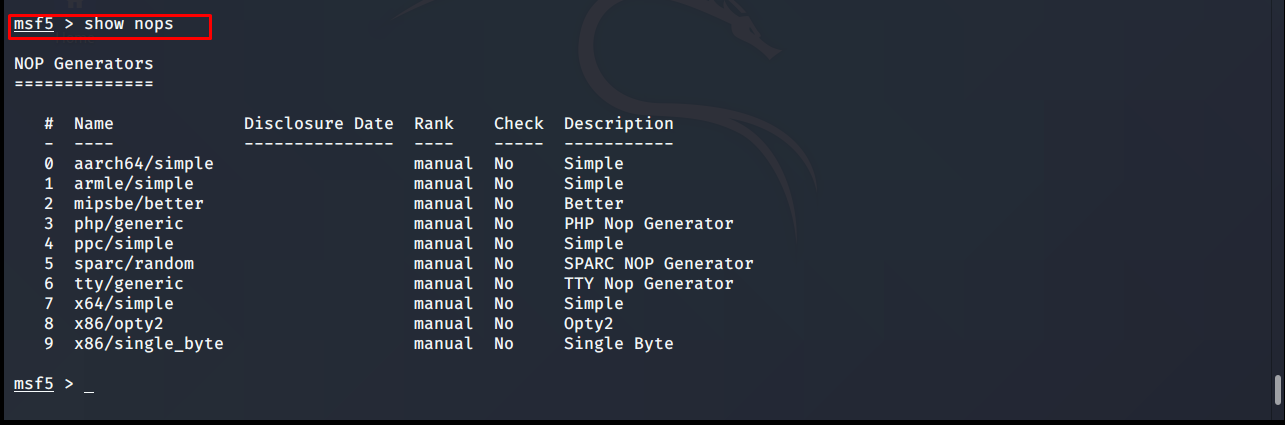
Nop: ”Not Operation” memory location bits filling the memory for learning purposes. It is often used to mislead intrusion detection and prevention systems.
msf5 > show nops
Metasploit’s unique friend system and features are given below.
Data: Data is used and changed by Metasploit.
Lib: The main structure of the system that creates the framework is its library.
Plugins: These are plugins that can run automatically and function using all the features of the Framework. They work during the process.
Tools: These are the tools that handle the processes according to the location and operation and work on the command lines.
External: External sources are 3rd party software and source codes.
Documentation: Documents used to inform the framework.
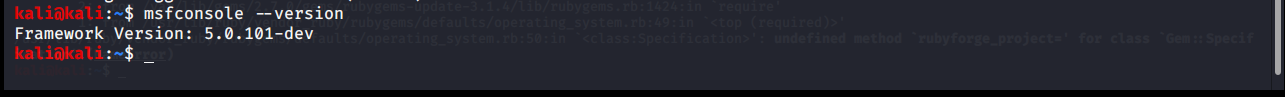
Metasploit version
At first, we can find out which version of Metasploit is with the msfconsole –version command.
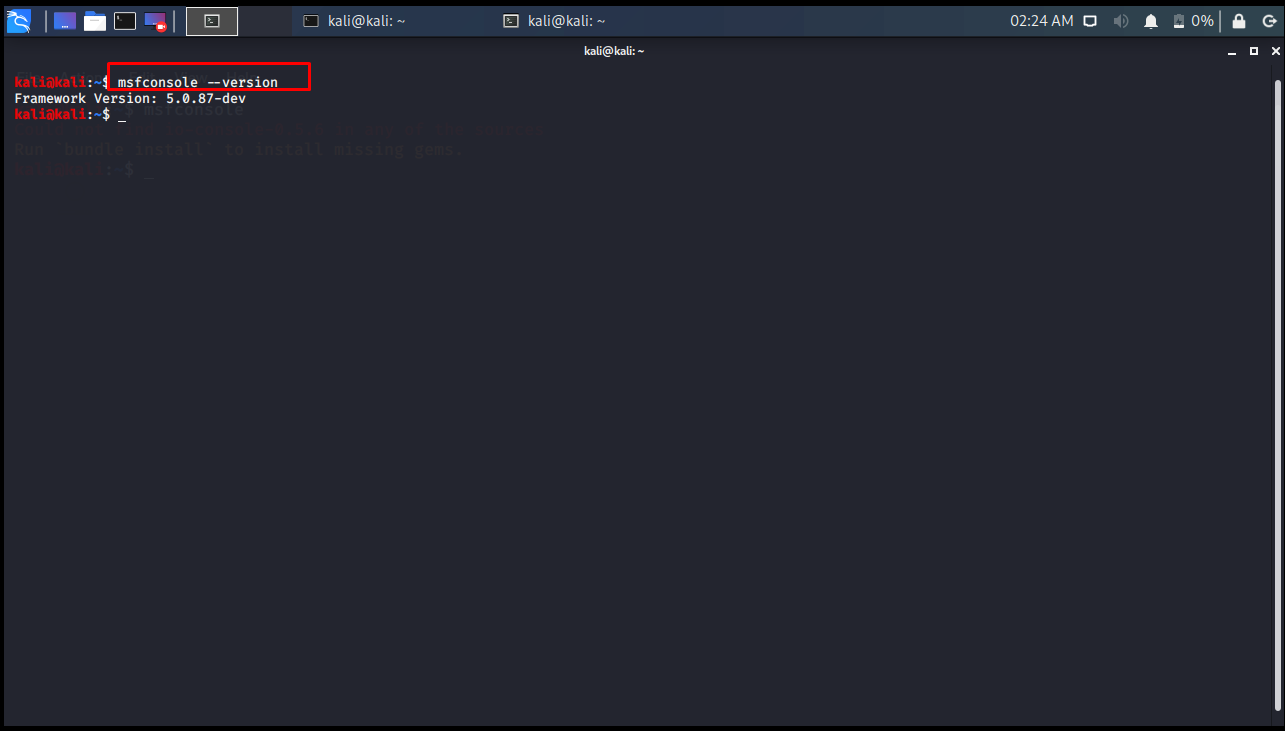
Metasploit update
Metasploit can be updated using the “sudo apt install metasploit-framework” command.
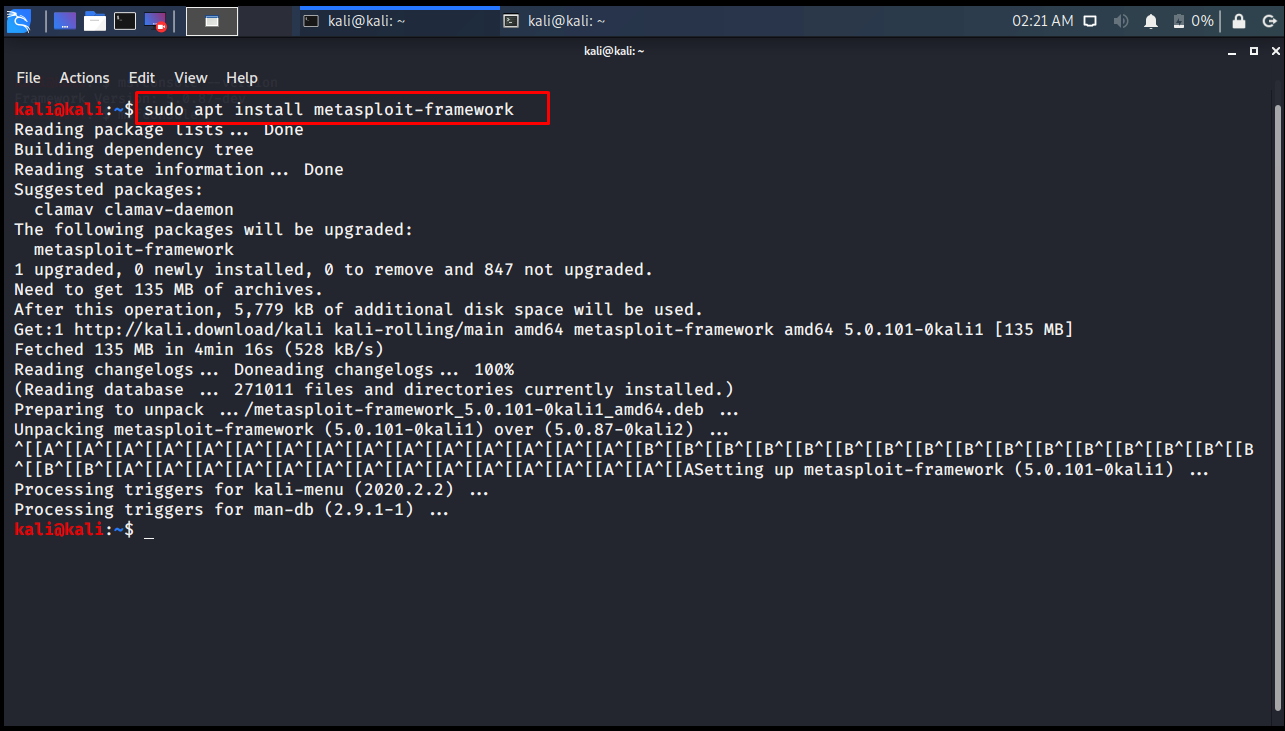
Metasploit Update Error – “Could not find io-console-0.5.6 in any of the sources”
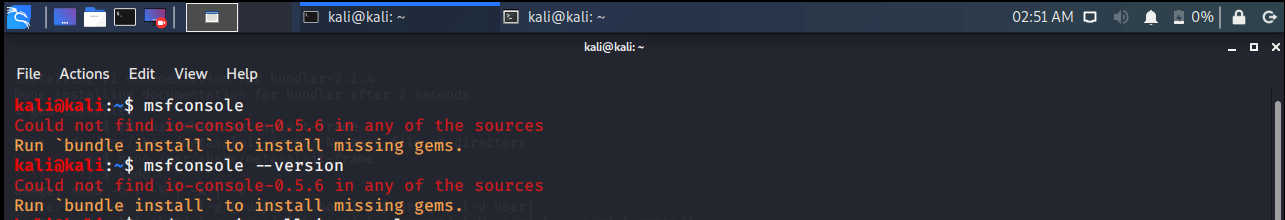
After updating, you may get the following error. We saw that we could not access msfconsole.
kali@kali:~$ msfconsole Could not find io-console-0.5.6 in any of the sources Run `bundle install` to install missing gems.
To fix this error, download rubylib in the metasploit-framework directory and run it. To do this, run the sudo apt-get install libruby2.7 command.
sudo apt-get install libruby2.7
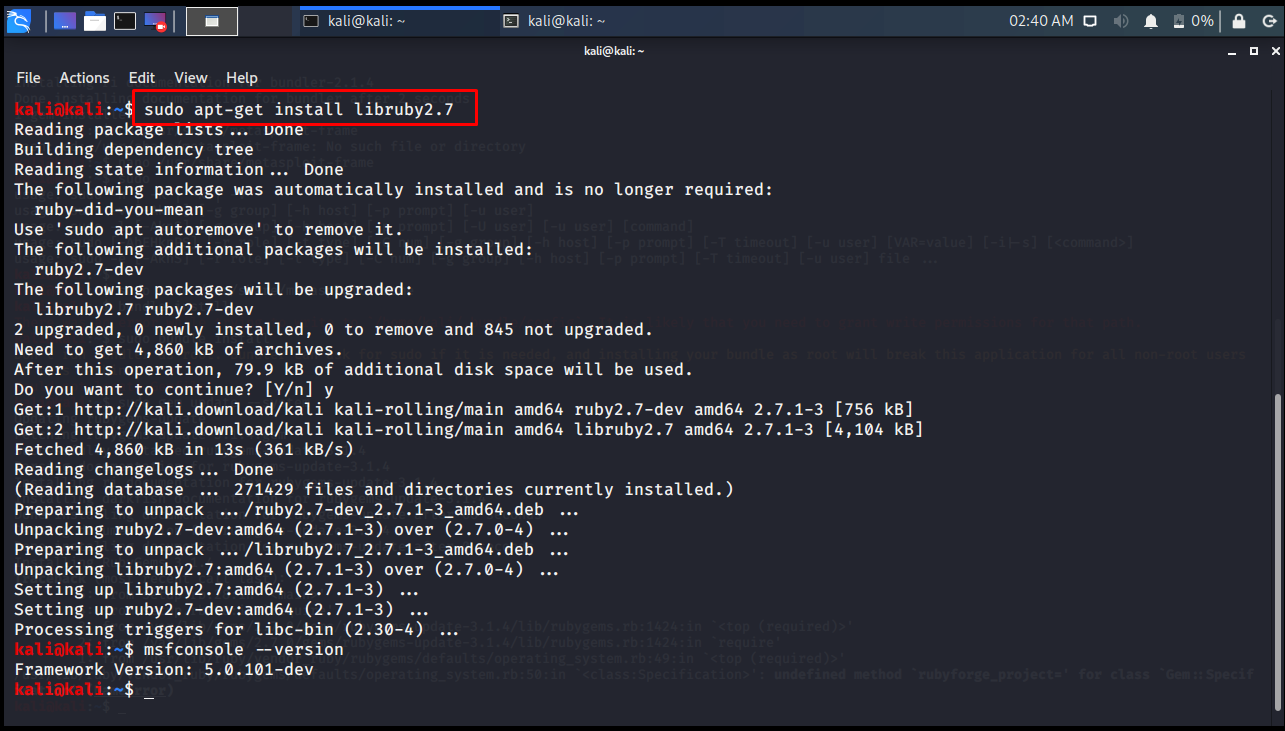
Before updating Metasploit, its version was 5.0.87-dev. After updating Metasploit, its version became 5.0.101-dev.
After updating the Metasploit, there are 2049 exploits, 1108 auxiliary, 344 posts, 562 payloads, 45 encoders, 10 nops and 7 evasions.