Calls made over the LTE network can still be monitored, even though they are encrypted. With a new system, researchers from the Ruhr University of Bochum were able to access the content of the phone call using a fault in the base stations.

A vulnerability in VoLTE technology, which provides HD + quality voice and video calls using LTE infrastructure, allows access to phone calls between users with a system called ReVoLTE, which can be installed for about $ 7,000.
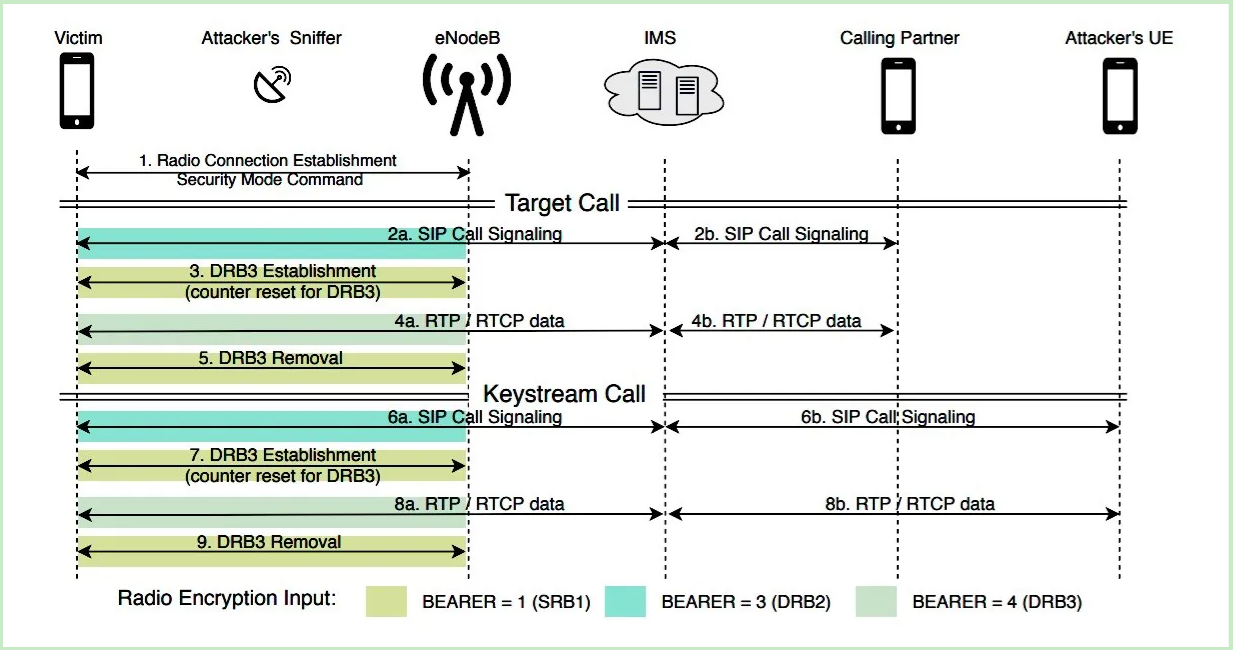
In a post where the researchers describe how the vulnerability occurred; “ReVoLTE attacks exploit the reuse of the same keystream for two consecutive calls in a radio link. This vulnerability is caused by an application error in the base station (eNodeB).” gave his statements.
How does the ReVoLTE attack happen?
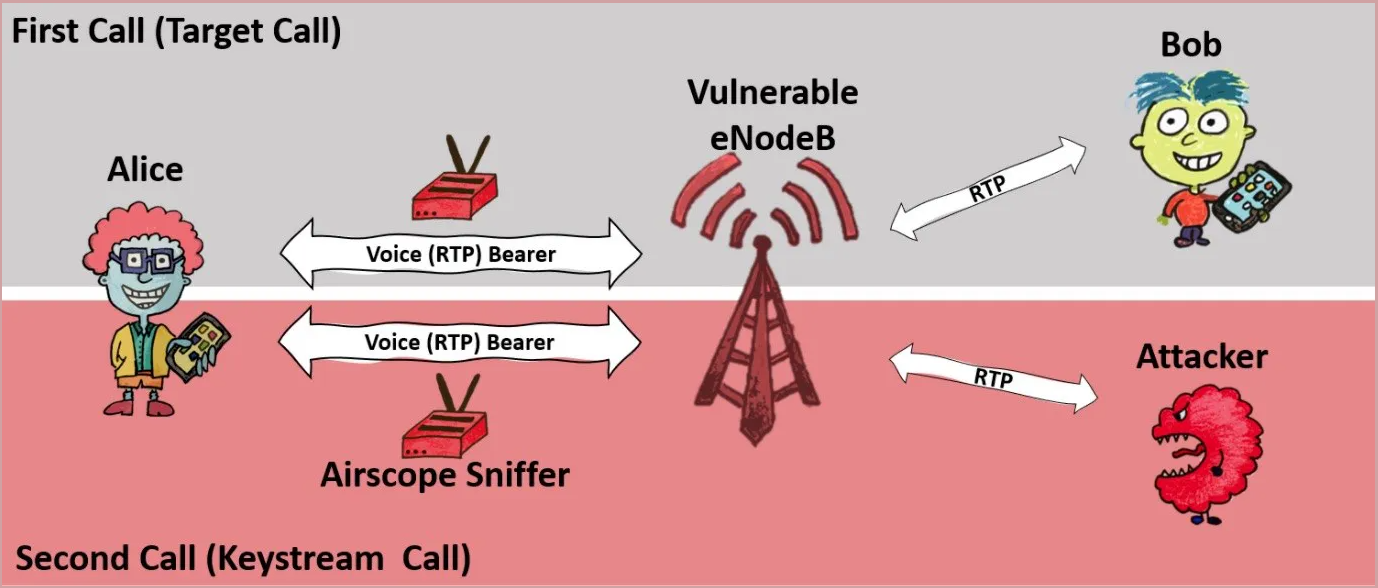
The researchers wrote that the attack exploited the use of encryption in the mobile cell tower by monitoring the encrypted radio traffic of a call made by someone on the cell of a base station using vulnerable encryption methods. Shortly after this attack, the attacker can call and chat with the person making the intercepted call. This allows the attack to monitor the encrypted radio traffic of the phone call in question and record unencrypted audio. The researchers noted that the call should be made using the same base station that has vulnerable encryption.
The attacker can then compare the two calls and crack the encryption, allowing it to recover the previous conversation between the victim and another person. However, the researchers say, if the entire conversation is to be decrypted, the attacker must keep the victim on the phone for the length of a targeted call.
“The longer he talks to the victim, the more he can decipher the content of the previous communication. For example, if the attacker and the victim talk for five minutes, the attacker can then decode the five minutes of the previous conversation,” the researchers said.
David Rupprecht from the research team: “VoLTE technology has been used for six years. We cannot check whether attackers have exploited the vulnerability in the past. The new cellular standard needs to be changed so that the same problem cannot occur again when 5G base stations are installed.” made statements.
Should we be worried?
German researchers tested this technique on large numbers of randomly selected 4G LTE cells across the country. Almost 80% of them were found to be vulnerable to this attack, called “ReVoLTE“. Since 4G LTE is widely used, the number of potential targets seems alarming. For this reason, the researchers state that they warn telecommunications operators as well as smartphone manufacturers before publishing the results of their research.
The vulnerability has already been largely fixed, but it is still stated that conversations from all users are not secure. The risk of piracy still continues with the ReVoLTE method. Previously, a four-person research team from the Korea Institute of Science and Technology (KAIST) conducted a security study for LTE. In the study, 36 different vulnerabilities were discovered. In LTE, where 15 security vulnerabilities were previously detected, a total of 51 vulnerabilities were detected. The researchers passed security tests using fuzzing.
Although LTE provides many advantages in speed, the resulting security vulnerabilities can cause hesitation in communication.





