Log files are the records that Linux stores for administrators to monitor important events about the server, kernel, services and applications running on it. Log files are a set of logs that Linux administrators allow them to track important events. Logs; They contain messages about the server, including the kernel, services, and applications running on it. Linux provides a centralized repository of Log files that can be found under the /var/log directory. Log files created in a Linux environment are classified in four different categories. These;
Application Logs
Event Logs
Service Logs
System Logs
Monitoring Linux Log Files
Log management is one of the most important responsibilities of a Server administrator.
You can get detailed information about server performance, security, error messages by watching the Linux Log files. If you want to do server management, regular log file analysis is 100% required. Log files allow you to anticipate problems that may arise before they occur and allow you to find the cause of problems that have arisen.
Linux Log Files to Watch
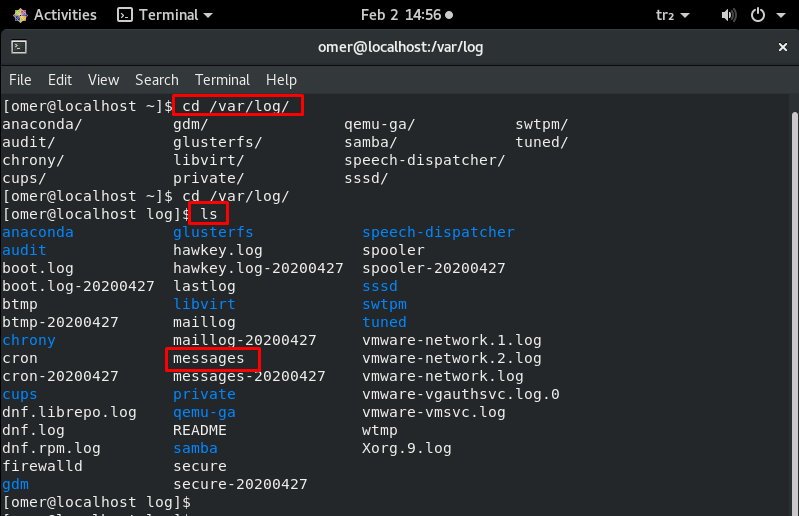
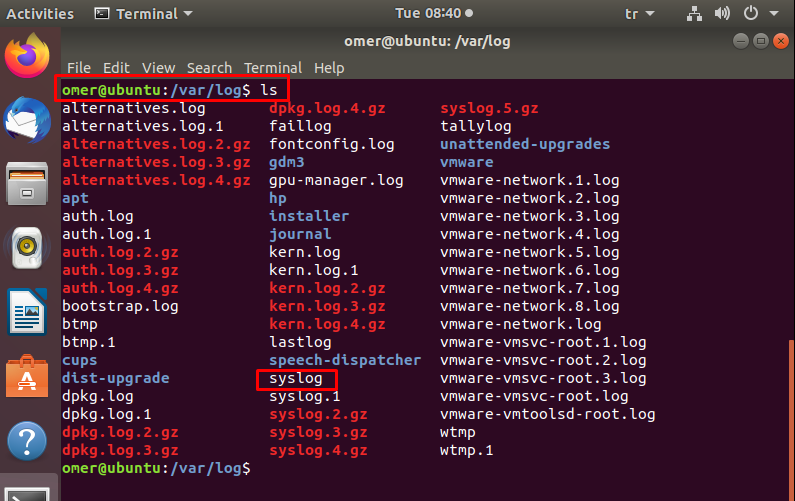
-
/var/ log/messages – /var/log/syslog
This Log file contains general system activity Logs. It is used to store informational and non-critical system messages. On Debian-based systems, the /var/log/syslog directory serves the same purpose.
In these logs, you can track non-kernel boot errors, application-related service errors and messages recorded during system startup. It is the first log file required for Linux administrators to check if there is a problem. For example some problems with the sound card, you can take a look at the messages stored in this log file to check if something went wrong during the system startup process.
nano /var/ log/messages nano /var/log/syslog
-
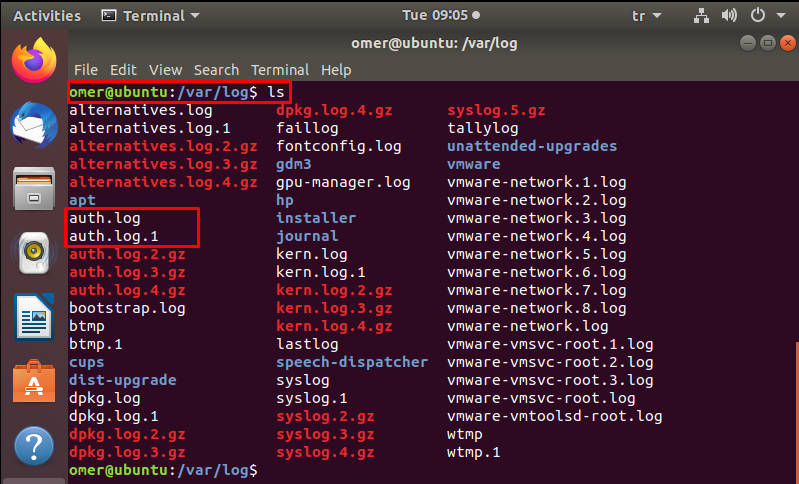
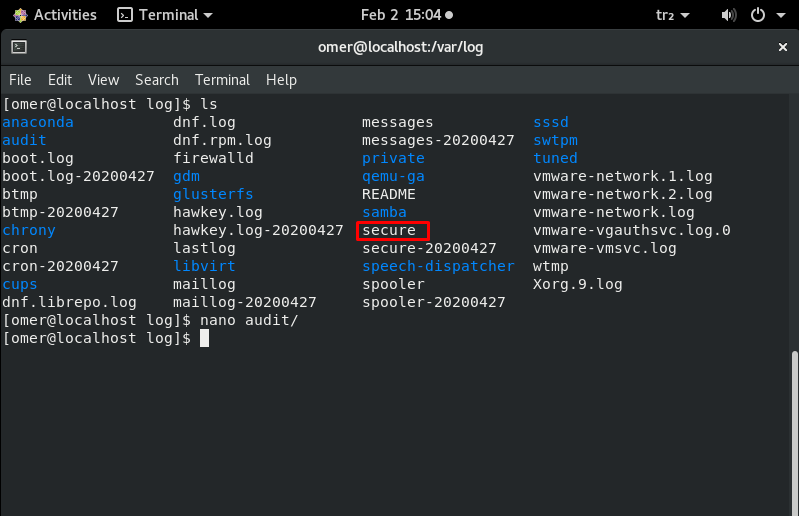
/var/log/auth.log – /var/log/secure
All events related to authentication on Debian and Ubuntu server are recorded here. If you are looking for an event with the user authorization mechanism, you can find it in this log file. The /var/log/secure directory also serves the same purpose in RedHat and CentOS-based systems.
If there is a security breach on your server, you can find it in this log file. Look out for a suspicious javascript file where it shouldn’t be. If there is a suspicious situation, quickly find this log file and check the following items.
- Unsuccessful login attempts.
- Brute force attacks and other vulnerabilities related to user authorization mechanisms.
- Basically to monitor the use of authentication systems.
- All security-related messages, including authentication errors.
- Also, sudo logins, SSH logins and other errors logged in system security services background.
nano /var/log/auth.log nano /var/log/secure
-
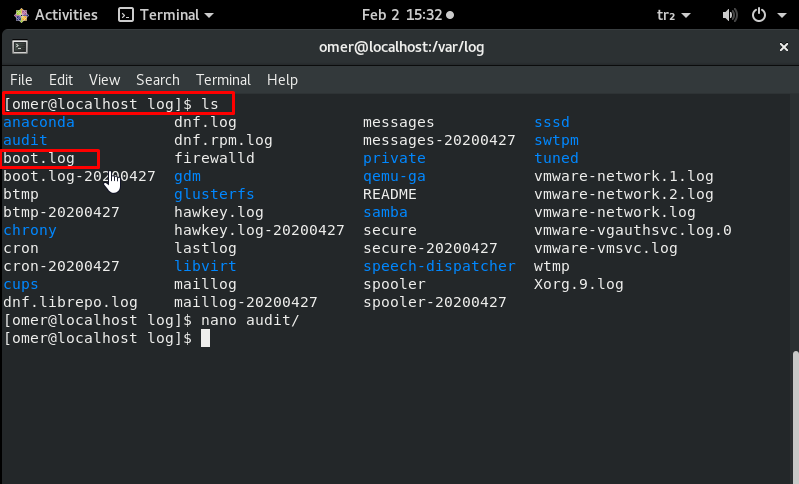
/var/log/boot.log
The system startup script /var/log/boot.log sends all boot messages to this log file. This is the boot store of relevant information and messages saved during the system startup process.
You can analyze this log file to investigate problems with the improper shutdown, unplanned restarts, or boot failure.
nano /var/log/boot.log nano /var/log/bootstrap.log
-
/var/log/dmesg
nano /var/log/dmesg
This log file contains Kernel ring buffer messages. Information about hardware devices and drivers is recorded here. As the kernel detects physical hardware devices associated with the server during the boot process, it captures device status, hardware errors, and other common messages.
This log file is mostly useful for dedicated server clients. If particular hardware is not working properly or not detected, you can refer to this log file to troubleshoot the problem.
-
/var/log/kern.log
It is a very important log file because it contains information recorded by the kernel. Used to troubleshoot kernel-related errors and warnings. Kernel logs can be helpful in troubleshooting a specially crafted kernel. It can also be useful for debugging hardware and connectivity issues.
nano /var/log/kern.log
-
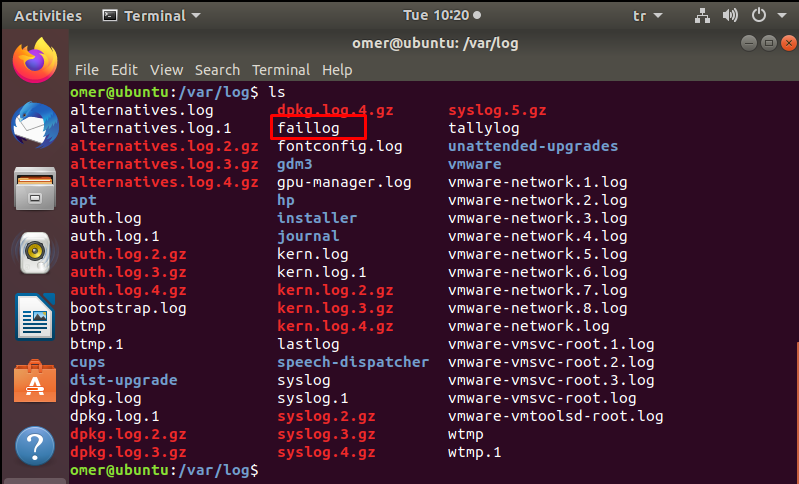
/var/log/faillog
This file contains information about failed login attempts. It is a useful log file to find any security breach attempts including Username/Password Hacking and Brute-Force Attack.
nano /var/log/faillog
-
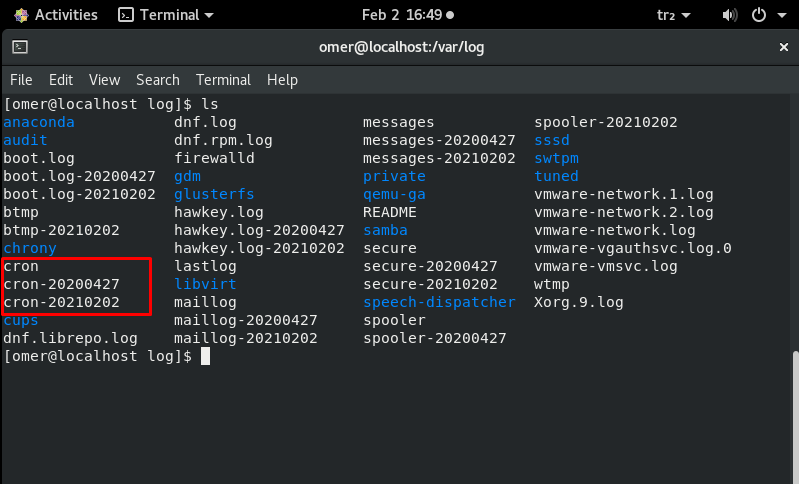
/var/log/cron
This log file records information about cron jobs. Whenever a cron job runs, this log file records all relevant information, including successful execution and error messages in case of failure. If you are having trouble with your scheduled cron, you should have a look at this log file.
nano /var/log/cron
-
/var/log/yum.log
It contains the information recorded in the log when a new package is loaded using the yum command. Installation of system components and software packages is monitored. You can check the messages recorded here to see if a package was installed correctly.
It helps you troubleshoot problems with software installations.
nano /var/log/yum.log
-
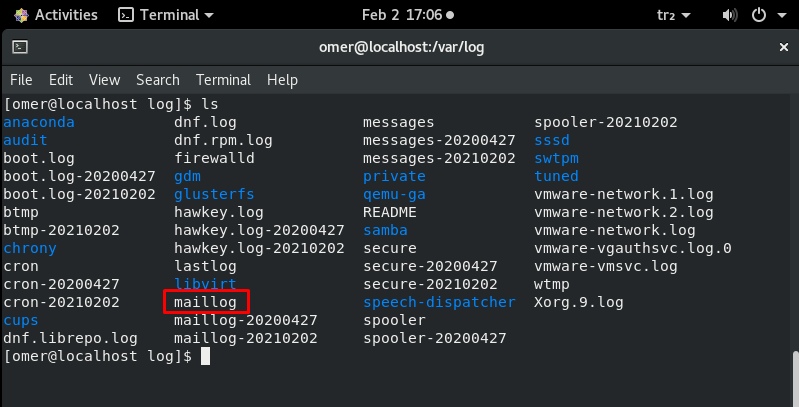
/var/log/maillog – /var/log/mail.log
All mail server related logs are stored here. You can get information about Postfix, smtpd, MailScanner, SpamAssassin or other email related services running on the mail server. From this log file, you can track all e-mails sent or received in a certain period. You can investigate issues with unsuccessful mail delivery. You can learn about possible spam-sending attempts blocked by the mail server. You can trace the origin of an incoming e-mail by examining this log file.
nano /var/log/maillog nano /var/log/mail.log
-
var/log/httpd/
This directory contains the logs recorded by the Apache server. Apache server log information is stored in two different log files, error_log and access_log.
You can access messages related to httpd errors such as error_log, memory issues and other system-related errors. This is where the Apache server writes events and error logs encountered while processing httpd requests. If something goes wrong with the Apache web server, check this log for diagnostic information. Besides the error log file, Apache also maintains a separate list of the access_log file.
All-access requests received over HTTP are stored in the access_log file.
It helps you monitor every page and every file served by Apache.
Logs the IP address and user ID of all clients that make connection requests to the server. It stores information about the status of access requests.
nano var/log/httpd/
-
/var/log/mysqld.log – /var/log/mysql.log
MySQL log file. All debug, error and success messages about [mysqld] and [mysqld_safe] are recorded in this file. RedHat, CentOS and Fedora store MySQL logs under /var/log/mysqld.log and Debian and Ubuntu under /var/log/mysql.log.
You can use this log to identify problems when starting, running, or stopping MySQL. You can get information about customer connections to the MySQL data directory. You can also set the ‘long_query_time‘ parameter to log information about query locks and slow running queries.
nano /var/log/mysqld.log nano /var/log/mysql.log




