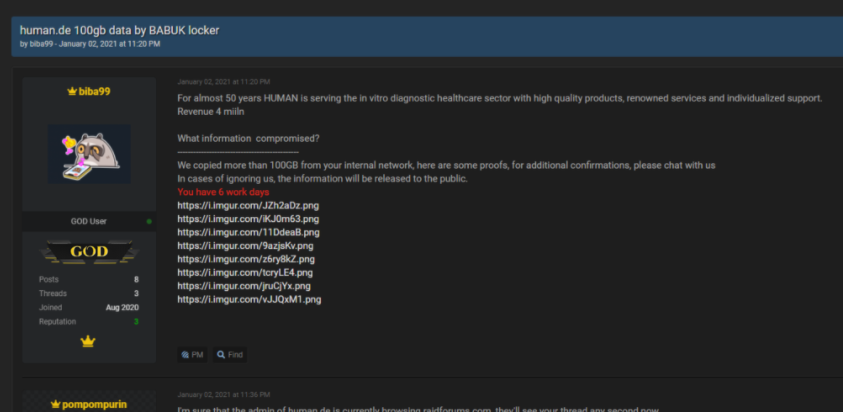
The first ransomware of 2021 was Babuk Locker. New ransomware called Babuk Locker, which targets corporate victims in human-induced attacks, has been detected. Babuk Locker is new ransomware launched in early 2021 and has since collected a small list of victims from around the world.

Security researcher Chuong Dong
According to security researcher Chuong Dong, who analyzed the new ransomware, Babuk Locker’s encoding is amateurish but includes secure encryption that prevents victims from recovering their files for free. “Despite the amateur coding practices used, the strong encryption scheme using the Elliptic curve Diffie-Hellman algorithm has so far proved effective in attacking many companies,” said Dong in the report. It is stated that there have been ransom demands ranging from 60 thousand to 85 thousand until now.
Checking Files Not to Encrypt
Once launched, threat actors can use command-line commands to control how the ransomware will encrypt network shares and whether they should be encrypted before the local file system. The commands that control this behaviour are below.
- lanfirst
- lansecond
- Nolan
Babuk Locker is currently using a hacker forum to leak its stolen data. Babuk Locker currently has five known victims from around the world.
- An elevator and escalator company.
- An office furniture manufacturer.
- A car part maker
- Medical test products manufacturer.
- An air conditioning and heating company in the USA.
One of the victims agreed to pay the $ 85,000 ransom. Babuk Locker representative recently announced that they will open a private leak site.
IOCS
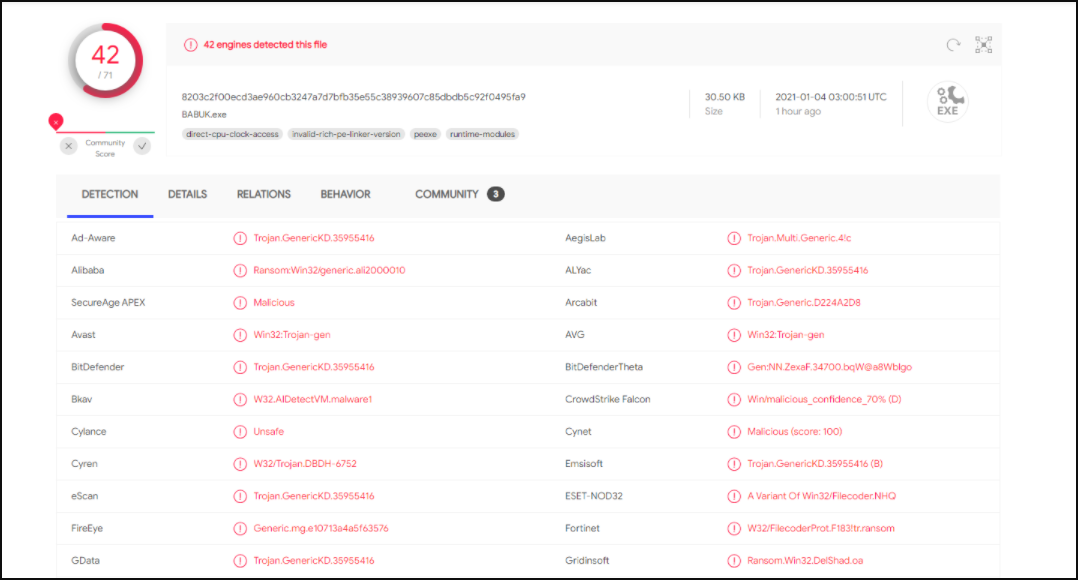
Babuk Ransomware comes in the form of a 32-bit .exe file. MD5 and SHA256 Hashes are found below. These hashes may change as Babuk Locker is updated.
MD5: e10713a4a5f635767dcd54d609bed977
SHA256: 8203c2f00ecd3ae960cb3247a7d7bfb35e55c38939607c85dbdb5c92f0495fa9
Sample: https://bazaar.abuse.ch/sample/8203c2f00ecd3ae960cb3247a7d7bfb35e55c38939607c85dbdb5c92f0495fa9/
References:
- threatpost.com
- http://chuongdong.com




