Thanks to Restricted Admin Mode, a new security feature that comes with Windows 8.1 and Server 2012 R2, we are protected from attacks that allow the theft of administrator passwords in the memory of an operating system that we know as “pass the hash”. Do not forget that it poses a great risk not only for malicious people but also for other administrators and users who share the remote desktop server you are connected to. Any user vulnerability in common management machines can cause seriously bad consequences.
Usually, companies connect to end-user computers with administrator accounts (eg user support team). It will be extremely easy for the attackers to capture the administrator password according to the memory (ram) or the connection method you use. In the table below, passwords are stored explicitly on memory in many authentications and connection methods used in active directory domain environments that are used by default.

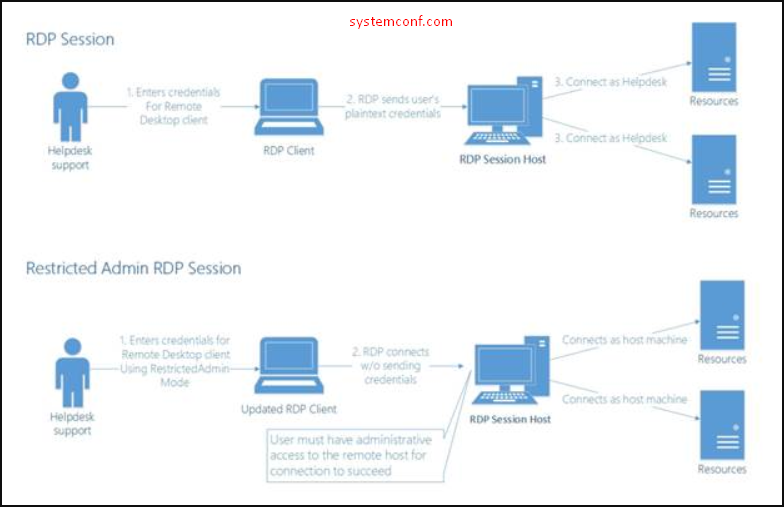
How Does Restricted Admin Mode for Remote Desktop Connection Protect?
Since the administrator in the normal connection method does not transfer his password to the RDP session, the administrator password cannot be stolen from this server or another server to which it connects through this server. However, if you want to connect to another resource as admin, because the admin password is not transferred to the machine where RDP is applied, you will try to access the resources with the machine account of the remote machine you RDP. Therefore, you should use this feature for appropriate scenarios.
- When the support team connects to the computers of the company employees, for example, if they say let me connect to a file server and pull the relevant file, it does not happen, because you go to the file server from the employee’s computer with the machine account of the working computer. The solution to this will first be required by copying that file to the company employee’s computer with the administrator right or creating a common area for this and similar installation files that machine accounts can also access.
- If you want to set up a sample machine for servers that system administrators connect to for management purposes and connect to all other servers through this machine, this will not solve our job either. For this scenario, we will have to use a different solution. We call this solution PAW(Privileged Access Workstation) for short.
Privileged Access Workstation(PAW) Model
You can use the PAW feature only for administrator accounts that will be connected to remote systems. For example, users who have domain users authority to connect to your company’s common terminal server cannot use it. Anyway, our aim will be to protect manager accounts.
For a secure connection, we need to change a setting on both the client that you will connect to, the administrator computer, and the remote servers or end-user computers you will connect to. We activate the following setting on the computers of the admins. You can make this setting with a group policy.
As below, in Group Policy, we only edit policies for admins and make settings.
At first, we open “Start> Windows Administrative Tools> Group Policy Management“.

Then we right-click “Admin Manager Group Policy Object” and press “Edit ..”.

We click on “Computer Configuration\Policies\Administrative Templates\System\Credentials Delegation” respectively. We open the “Restrict delegation of credentials to remote servers” option under it. We click on the “Enabled” option and press the “OK” button.

We connect to the remote server with a command like the one below.
mstsc.exe / RestrictedAdmin

Note: If you are proceeding with the GPO, all connections for this client will already work like this, so if there is no relevant setting on the target server, it is normal for you to have a connection problem with another server on the internet. Therefore, if you want to use it on a link basis, you can use the parameter as above for such links instead of proceeding with the GPO.
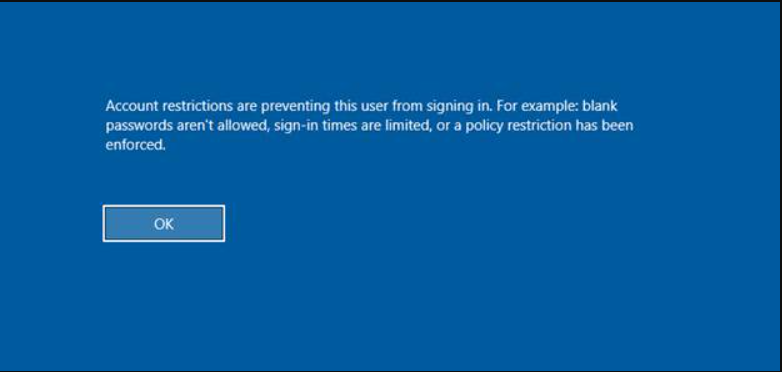
Note: If you make the necessary settings but you get a warning like the following on the system you are connected to, the main reason is that this feature is turned off by default after Windows updates 2973351 and 2975625 are installed. First of all, we need to open this in target systems.
“Account restrictions are preventing this user from signing in. For example: blank passwords aren’t allowed, sign-in times are limited, or a policy restriction has been enforced.”
In this case, it will be sufficient to create the following registry key on the target server. We open “HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\ Lsa” in the registry. We create a new DWORD value. We write its name “DisableRestrictedAdmin“. We enter the value as “0“.
After doing that, you can connect without any problems.

Benefits and Cons of Restricted Admin Mode Feature
The most important advantage is that it provides protection against the pass the hash attacks since no password information is kept on the remote system. However, if you do not hold tight to other security measures in your environment, you may open up at some point. For example, if you do a normal RDP session, first of all, your RDP client will perform the network logon process with the password you define. It goes to the remote machine and verifies you. If the verification is successful, your password is securely transmitted to the remote server as a hash. With this information on the server, it realizes the interactive logon process.
How does the process work when I RDP a remote server with Restricted Admin Mode turned on?
In this case, the RDP client sends a request directly to the remote server for the interactive logon process. However, the RDP client does not send plain text or any password to the remote server in any way. In other words, if a person receives the hash data of the administrator password directly because there is no pre-verification, he can infiltrate that system through the RDP port.
Since SMB/RPC is open between client systems and server systems, a person can connect to the servers with the hash in their hand. However, in companies where security is important, these ports are closed between server systems and client systems. However, if the RDP port is open, which is open in this scenario, a malicious person can make a pass-the-hash attack over the RDP protocol with only the hash value without necessarily a username and password. For this reason, be aware that this feature may cause such a vulnerability when using it.
Note: The simplest advice here is actually to switch to a scenario such as an ip boundary or PAW within RDP ports.




