WinRM is a service that allows remote users to obtain a Powershell session from a system. This service uses the SOAP-based WS-Management protocol. WS-Management is designed for finding and changing the management information of a system. WinRM only allows users with administrative privileges to gain session. WinRM service communicates over the HTTP(S) protocol and uses TCP ports 5985 (HTTP) and 5986 (HTTPS) by default. WinRM service runs under the “Network Service” account and creates isolated processes for users to obtain a session. Therefore, another user cannot access the session that a user has obtained.
By default, the WinRM service is accessible to all remote servers on the same network. All systems with administrator credentials can access all servers with WinRM service active. Therefore, WinRM service should definitely be turned off on servers where WinRM service is not used actively. Incoming connections may be restricted on servers that require the WinRM service to be open. Client addresses that can access WinRM ports through Windows Firewall can be allowed for this process. Also, adjustments can be made on “admin groups” and “Remote Management Users” groups to determine the users that can obtain WinRM session.
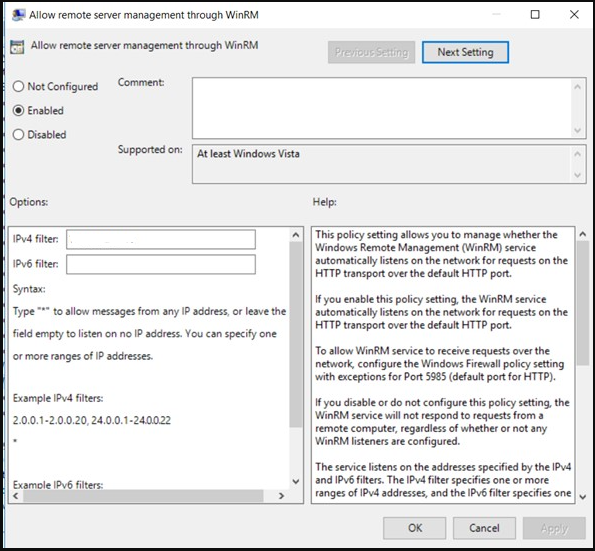
Allow remote server management through WinRM
As another restriction, the policy named “Allow remote server management through WinRM” can be activated. This policy ensures that in cases where the server has more than one network interface, the listening process will be done through which interfaces. Interface addresses where the listening process will be performed can be specified with the “IPv4 filter” and “IPv6 filter” options.
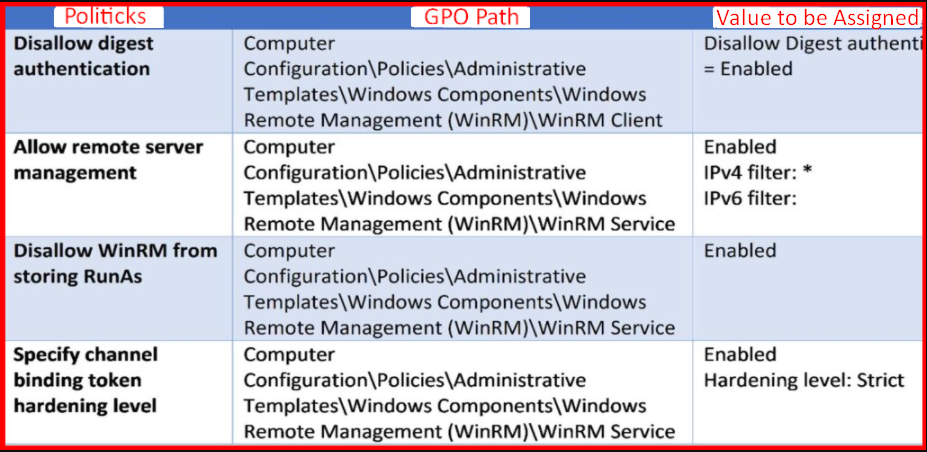
You can achieve WinRM tightening by applying the following policy settings over the Active Directory GPO.