The vulnerability, which was publicly disclosed on Twitter by security researcher Jonas Lykkegaard and has not yet been officially updated, has been tracked by Microsoft as CVE-2021-36934. “An elevation of privilege vulnerability exists due to permitted Access Control Lists (ACLs) in multiple system files, including the Security Accounts Manager (SAM) database,” Microsoft explained in a security document released on the evening of 20.07.2021. Using this vulnerability, attackers can install programs, view, modify or delete data, or create new accounts with full user rights. To exploit this vulnerability, an attacker must have the right to execute code on the target computer.
The zero-day vulnerability, as Microsoft announced, has been affecting versions of Windows since October 2018, starting with Windows 10, version 1809. Lykkegaard also revealed that he found that Windows 11 was also affected.
Solution Offers and CVE / CWE
Since no update has been released for this vulnerability yet, you can follow the steps below to temporarily prevent exploitation of the vulnerability.
- Restrict access to %windir%\system32\config.
Open Command Prompt or Windows PowerShell as administrator. Run the command below.
“icacls %windir%\system32\config\*.* /inheritance:e”
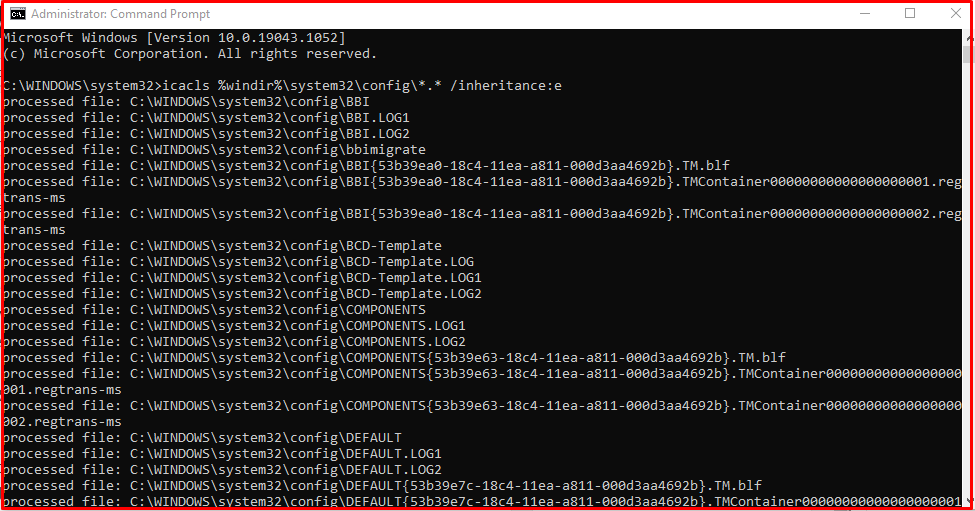
- Delete the Volume Shadow Copy Service (VSS) shadow copies.
Delete all existing System Restore points and Shadow volumes before restricting access to “%windir%\system32\config“. If you want, you can create a new System Restore point.
CVE/CWE: CVE-2021-36934.
Reference:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934
Note: When the update of the CVE-2021-36934 vulnerability is available on the Microsoft side, update your system from the Microsoft site.




