IEEE 802.1X standard; It is a port-based network access control that allows authentication and authorization of devices plugged into a LAN port with point-to-point connections. It is used to authenticate port-based users on the network and to apply ‘network access policies‘ to any user or group. If authentication and authorization are unsuccessful, that port is closed to access, thereby protecting the local network infrastructure. User authentication; The MAC address is provided by the switch port or an external authorization policy. NAC is user-oriented, network-based access control that determines, controls and authorizes who enters the network with what right. The 802.1X protocol is used for secure authentication in both wired and wireless networks.
Authentication of 802.1x Protocol
Authentication is done for three purposes (AAA) with the 802.1X protocol.
Authentication: Giving users the right to access the system, program and network.
Authorization: It is the authentication of the device or user in the use of a server, switch, router.
Accounting: It is the process to monitor what a user does, user movements, user data connections and user system records.
The 802.1X protocol must be understood together with the EAP and PPP protocols. PPP (Point to Point Protocol) is a protocol used in many different places, from a dial-up connection to cable modem authentication over a DSL connection to authentication of 2 layer tunnel protocol. It is used as an improved transmission protocol standard, which is a general framework identification system without the need for IP on the transmission layer during the user authentication process of PPP 802.1X.
EAP(Extensible Authentication Protocol) works inside PPP’s authentication protocol. It offers different authentication methods. It provides a generalized framework for different authentication servers, RAS, RADIUS, together with EAP. With EAP, the interoperability and compatibility of authentication methods become simple.
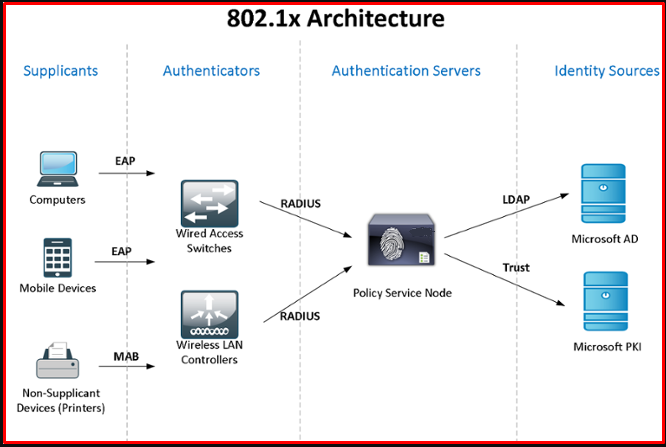
How 802.1x Protocol Works
There are three key elements in the 802.1x architecture. These; The client or person to be authenticated is the access point and Authentication server located between the Client and the authentication server.
The controller (authenticator) device, located between the client (the user who wants to authenticate) and the server (Authentication Server) where the authentication is made, requests the client to identify itself by sending an EAP-Request/Identity package in case of connection. The client responds with the EAP-Response/Identity packet identifying its identity. And this packet is encapsulated and sent to the server. The server throws an invitation to the controller, such as an encrypted token system. The controller opens this packet and sends it to the client in EAPOL (EAP over LAN). The client responds to the invitation through the controller. If the client has the required user definition and rights, the validating message sent by the server results in the controller granting the client access to the LAN.




