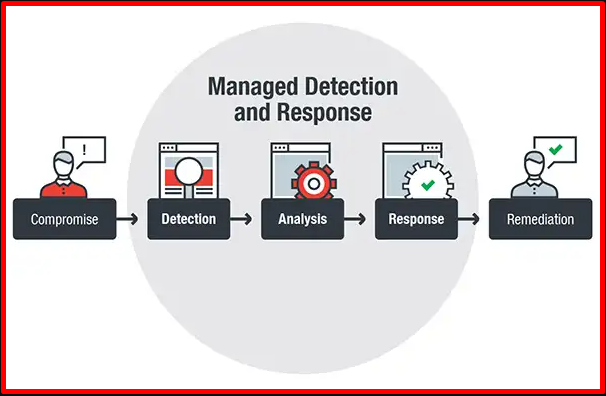
The most basic characteristic of the services offered by MDR (Managed Detection and Response), apart from classical attacks, is to detect advanced attacks in detail and to intervene at the source of the attack. EDR software is used for advanced detection and intervention processes to be provided by MDR. MDR is actually a service where threat detection, threat detection response and remediation processes are determined and managed. MDR can analyze all retroactive traffic. It uses a network-based solution. As the MDR service scope, the cyber threat intelligence of the relevant institution against cyber attacks can be broadly defined to be used in all processes. MDR benefits reduce the impact of successful attacks. Provides 24/7 visibility. It provides continuity by researching the threats that may target the organization and presenting results and reports.
EDR (Endpoint Detection and Response)
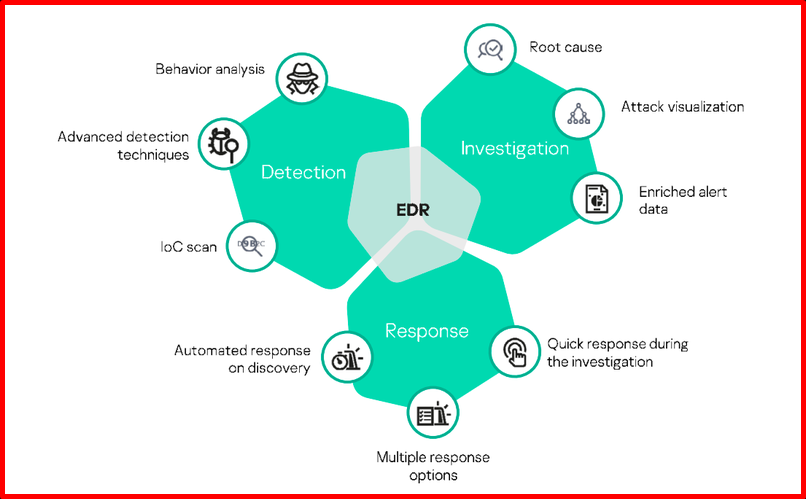
They are security products developed to protect endpoints and ensure the security of entry points in the infrastructure. Thanks to EDR systems, it is possible to respond to endpoint threats quickly and appropriately. EDR tools monitor endpoint and network events and record them in a central database where further analysis, detection, investigation, reporting and alerting occurs. EDR tools provide comprehensive visibility across all endpoints in the corporate network, enabling automation of tasks to discover, scale, investigate and neutralize advanced threats. It has become very important for internal security by facilitating early identification of internal threats or external attacks thanks to continuous monitoring and discovery. EDR data collection timing, scope, or threat intelligence providers differ in their ability to integrate policy.
Not all EDR tools work the same. For example, some EDR tools perform further analysis on endpoints, while another EDR tool performs data analysis through the management console. But all EDR tools perform the same basic functions for the same purpose. You can see a comparison of the most used is in the industry at https://www.esecurityplanet.com/products/edr-solutions/.
EDR Usage Advantages
- It enables the detection and analysis of exploit-based attacks.
- It can detect hard-to-detect threats like PowerShell exploits, memory attacks, file-less.
- It can work in integration with various security products.
- It allows observing the lateral movements of the malware trying to hide on the endpoints.
- It reduces incident detection time by using Behavior Monitoring technologies.
- Thanks to behaviour analysis, it prevents damage to the endpoints and the network.
- It provides protection of other endpoint products in the network by detecting unknown files and applications and providing their testing in virtual environments.
- It enables the monitoring of the actions taking place on the endpoints and the instant viewing of their analysis.
- It provides the opportunity to detect important information in forensic monitoring processes. (such as ip, URL, domain, DNS, file name, file path)
EPP (Endpoint Protection Platform)
EPP is a security solution designed to detect and block system-level device-level threats. EPP encompasses anti-malware capabilities designed to protect against signature-based attacks. When a file is included in the network, the EPP tool scans the file to see if the file’s signature matches any malicious threats in the database. EPP provides an integrated suite of edge protection technologies, such as antivirus, data encryption, intrusion prevention, and data loss prevention, that detect and stop various threats at the endpoint. Since EPP works on a signature basis, it is ineffective against advanced attacks.
EDR and EPP have similar goals but are designed to accomplish different purposes. EPP detects potentially malicious activity by identifying malicious files. It is designed to provide device-level protection by providing tools for incident investigation and response. EPP acts as the first line of defence by filtering out attacks that can be detected by the organization’s deployed security solutions. EDR acts as a second layer of protection, allowing security analysts to hunt threats and detect more subtle threats to the endpoint. Effective endpoint defence helps an organization’s security team to use a solution that integrates the capabilities of both EDR and EPP to protect against cyber threats.

NDR(Network Detection Response)
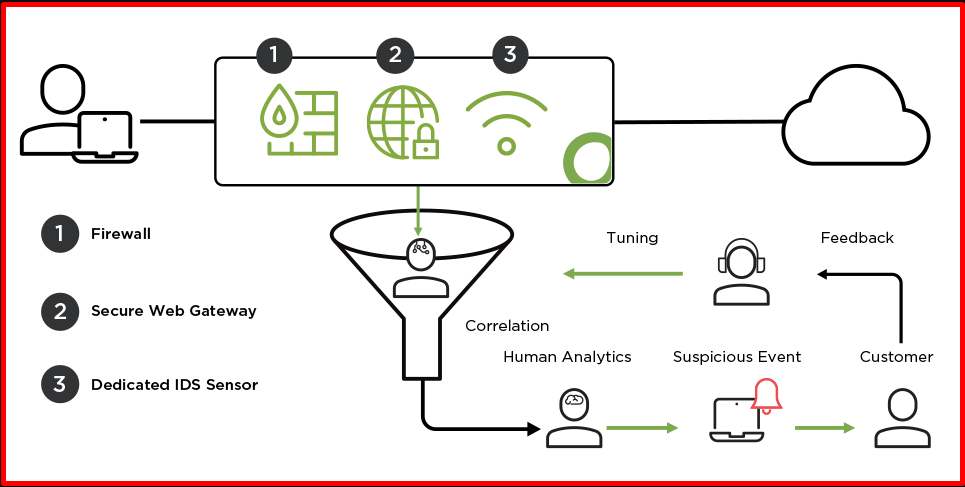
NDR is a security service that enables the organization to monitor network traffic and detect cyber threats to the network and react to attacks in the results of attacks that may occur by cyber attackers. Cyber attacks can cause serious damage to the internet infrastructure. The NDR service is used to monitor the network infrastructure and respond to attacks. NDR is a security solution that organizations use to detect and prevent malicious activity, identify root cause, conduct post-incident investigations and forensic analysis to facilitate mitigation. NDR solutions can protect against non-malware threats such as insider attacks, credential abuse, privilege escalation, flanking movement, and data theft. The main difference from NDR EDR is that a malware can exploit EDR at the BIOS level and thus fail to reflect its goals to EDR. However, as soon as it interacts with any other system via the network, it can be seen by network tools.
XDR (Extended Detection And Response)
XDR has a wider range of features than EDR. It uses the latest and most up-to-date technologies to provide greater visibility, collect and correlate threat information, while using analytics and automation to help detect attacks today and in the future. XDR tries to correlate data by collecting data on various AP points such as system servers, email, cloud and endpoints. The system analyzes the associated data, giving visibility and context. Due to the increase in the number of security products, management has become difficult at a single point. It is a cloud-based security product as a solution. XDR aims to manage and intervene through a single platform by processing data from security products.
XDR(Extended Detection And Response) Advantages
- It can provide enhanced protection, detection and response.
- It automatically associates and acknowledges alerts, reducing the need to track down false positives.
- Less costly to detect and respond to cyber threats in the most effective way.
- Detection and response of targeted attacks.
- It works in harmony with multiple security products.
- It looks at intelligence along with threat intelligence sources.





