Sysmon is a tool developed by Microsoft that allows recording the activities on the device it is on. It provides detailed information for activities such as the formation of processes and network connections, allowing abnormal situations to be detected. You can find detailed information about Sysmon from this link. You can access it from Microsoft’s site for installation and configuration.
Mimikatz
It is a tool that allows obtaining passwords from memory in Windows systems. You can download it from the link below.
https://github.com/gentilkiwi/mimikatz
We will talk about 3 different ways to detect mimikatz in the system using Sysmon. These;
Watching Mimikatz Files
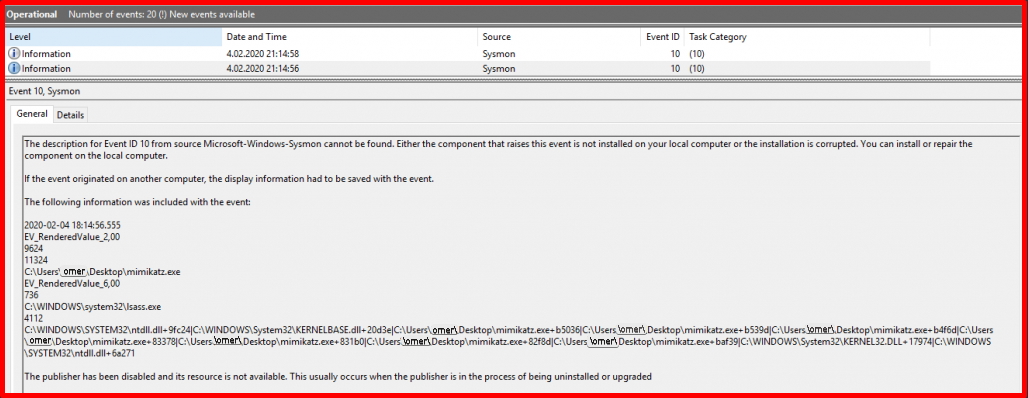
Monitoring the files named “mimikatz” created in the system is an option for detection. But since the file name can be easily changed, it is quite easy to circumvent. Care should be taken in this regard. You can apply the following rule for Sysmon Configuration. Looking at the output, it is understood that the “mimikatz.exe” file has been extracted from the compressed file.
<FileCreate onmatch="include">
<TargetFilename condition="contains">mimikatz</TargetFilename>
</FileCreate>
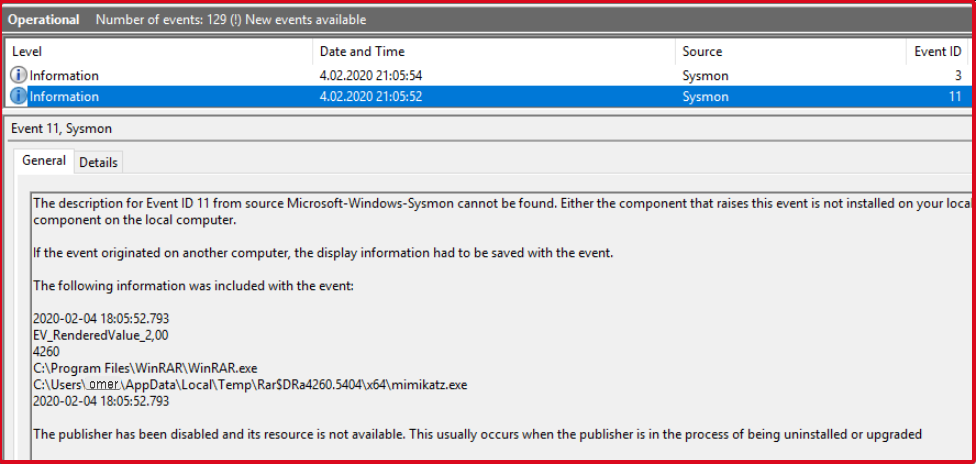
Monitoring Hash Values
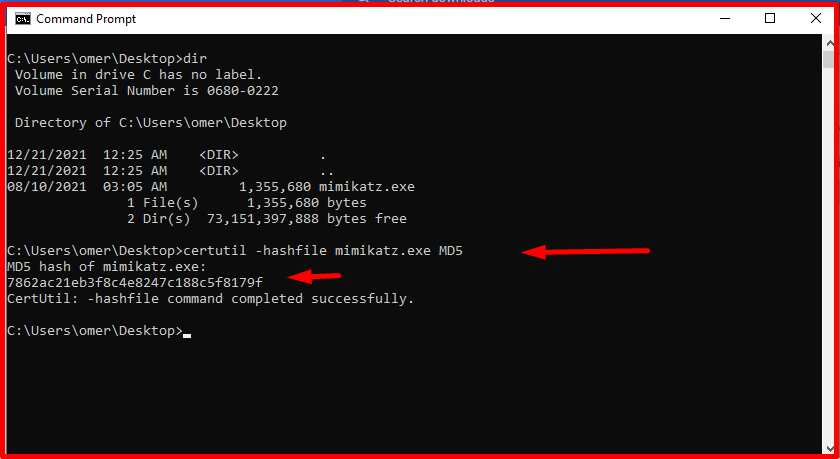
When a process with hash values belonging to Mimikatz is started, Sysmon can be made to generate a warning. Since the hash value will be renewed with a small change to the file, this method is also not very healthy. Looking at the hash value of “mimikatz.exe” shows that it is “7862ac21eb3f8c4e8247c188c5f8179f”.
C:\Users\omer\Desktop>certutil -hashfile mimikatz.exe MD5
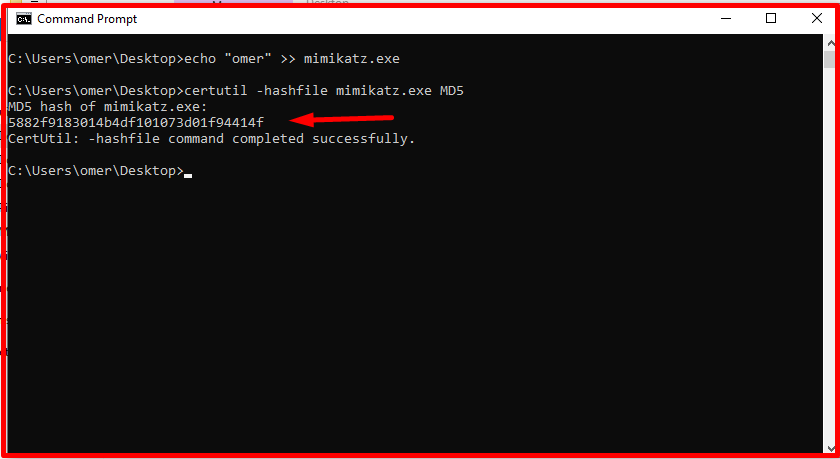
When a small addition is made to the file, its content will change and the hash value will also change. The screenshot showing that the hash value of “mimikatz.exe” has changed is as follows.
echo "omer" >> mimikatz.exe certutil -hashfile mimikatz.exe MD5
Below is the configuration required to run the file with the hash value “7862ac21eb3f8c4e8247c188c5f8179f“.
<ProcessCreate onmatch="include">
<Hashes condition="contains">7862ac21eb3f8c4e8247c188c5f8179f</Hashes>
</ProcessCreate>

Monitoring the “lsass.exe” Process
Mimikatz uses lsass.exe to obtain passwords. With the monitoring of “lsass.exe“, the processes that call it are also recorded. Thus, all suspicious processes that call lsass.exe, not just mimikatz, are recorded. For more effective results, processes that call “lsass.exe” for legal activities can be excluded.
<ProcessAccess onmatch="include">
<TargetImage condition="contains">lsass.exe</TargetImage>
</ProcessAccess>