In the previous section, we explained Carbon Black EDR (Endpoint Detection and Response) and the “Detect” section. Lastly, we stayed in the “Watchlist” tab in this section. In the second part, we will explain the features of other tabs. We continue from the “Process Search” tab.
Process Search
When a potentially threatening event is recognized in Process Search, processes with Indicators of Compromise (IOCs) of all systems and endpoints can be searched. Basic process searches can be performed using search strings and predefined search criteria. A written Watchlist is checked and activated here. In other words, you can check whether the Watchlist you wrote is working or not here.

Binary Search
Carbon Black Response sensors start monitoring their binaries as soon as they are executed by a process. You can perform a binary search to discover the metadata of a binary.

Go Live
Opens a command line page for direct access to content on endpoints running informational sensors. It allows you to communicate directly with the endpoint. Below are a few sample commands to run on the Go Live command line. When we run it on a Linux machine, only “execfg” comes to the command.
execfg ifconfig execfg ls execfg ps execfg rm "filename"

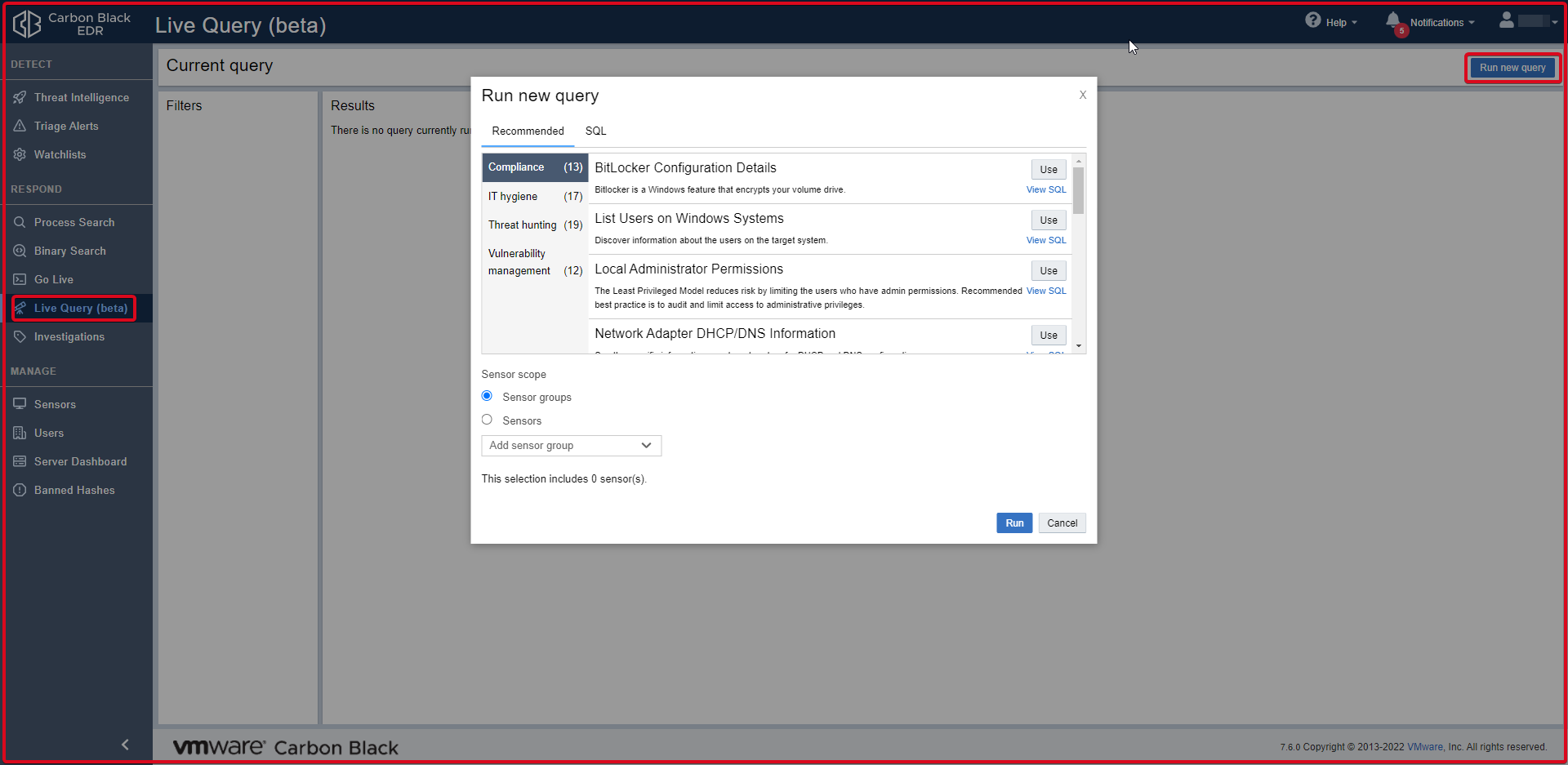
Live Query
You can use ready-made queries in this section. You can see and use the queries here by clicking the “Run new query” button.
Investigations
Investigations host process events that share a common focus. It can contain details and notes. It enables data to be grouped for reporting, compliance or retention purposes. It is one of the methods that can be used to initiate an investigation after a suspicious transaction is found.

Sensors
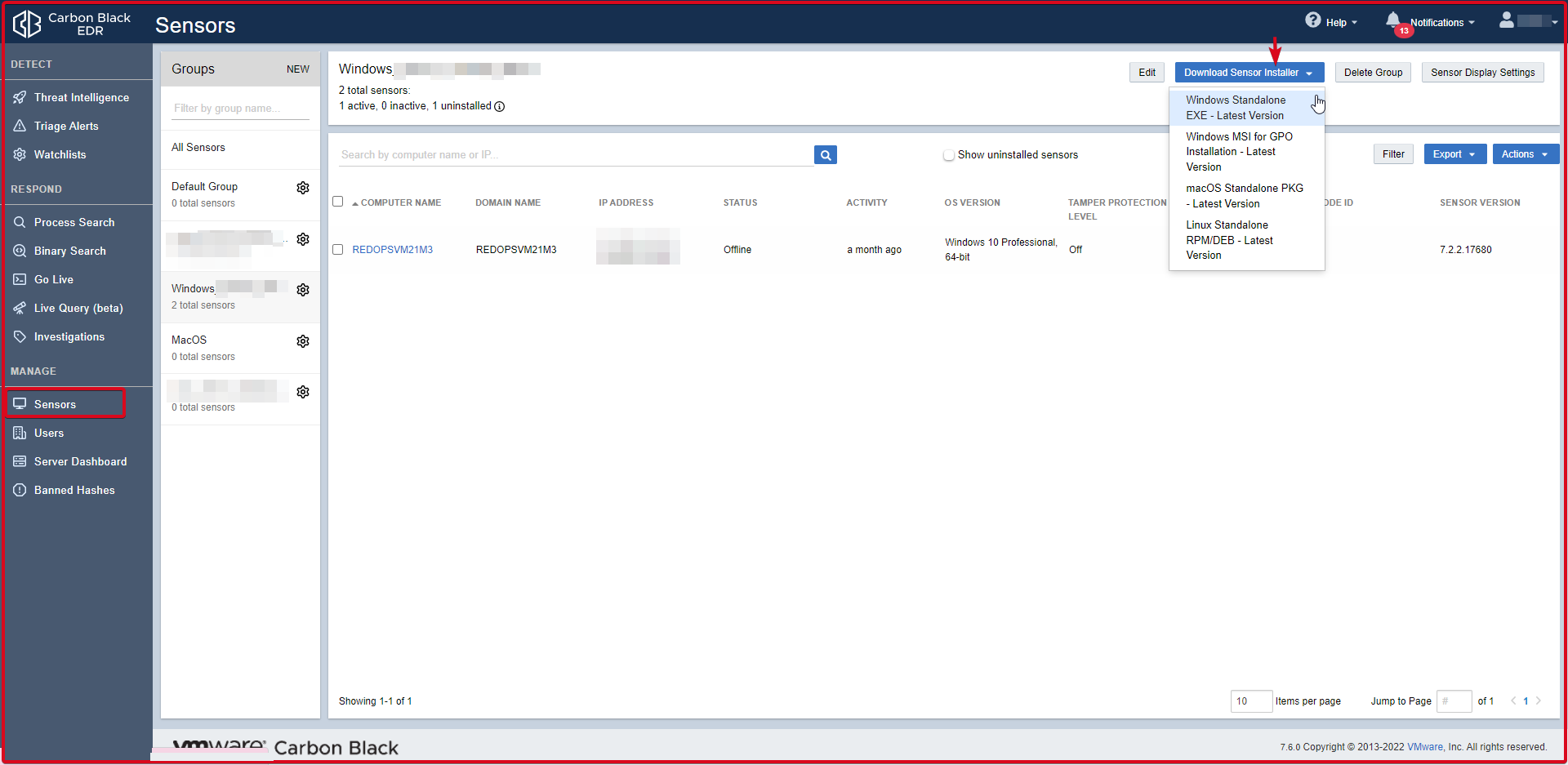
Agents are installed on computers in a distributed network. They collect event data on machines where agents are installed and forward them to the Carbon Black server for indexing. If we want to download an agent to install on the relevant operating system on the Sensor page, click the “Download Sensor Installer” button. Then you can download the sensor for which operating system you want to download by clicking on it. You can see some information about the REDOPSVM21M3 sensor that comes as seen on the screen below. The connection port between the Sensor(Agent) and the Carbon Black EDR server is 443.
Users
Tabs on the Users page allow CB Response administrators to add and configure new users who can log into Carbon Black Response, view user activity, and create and manage user teams.

Server Dashboard
The Server Dashboard displays server statistics such as sensor statistics, license information, and server presence.

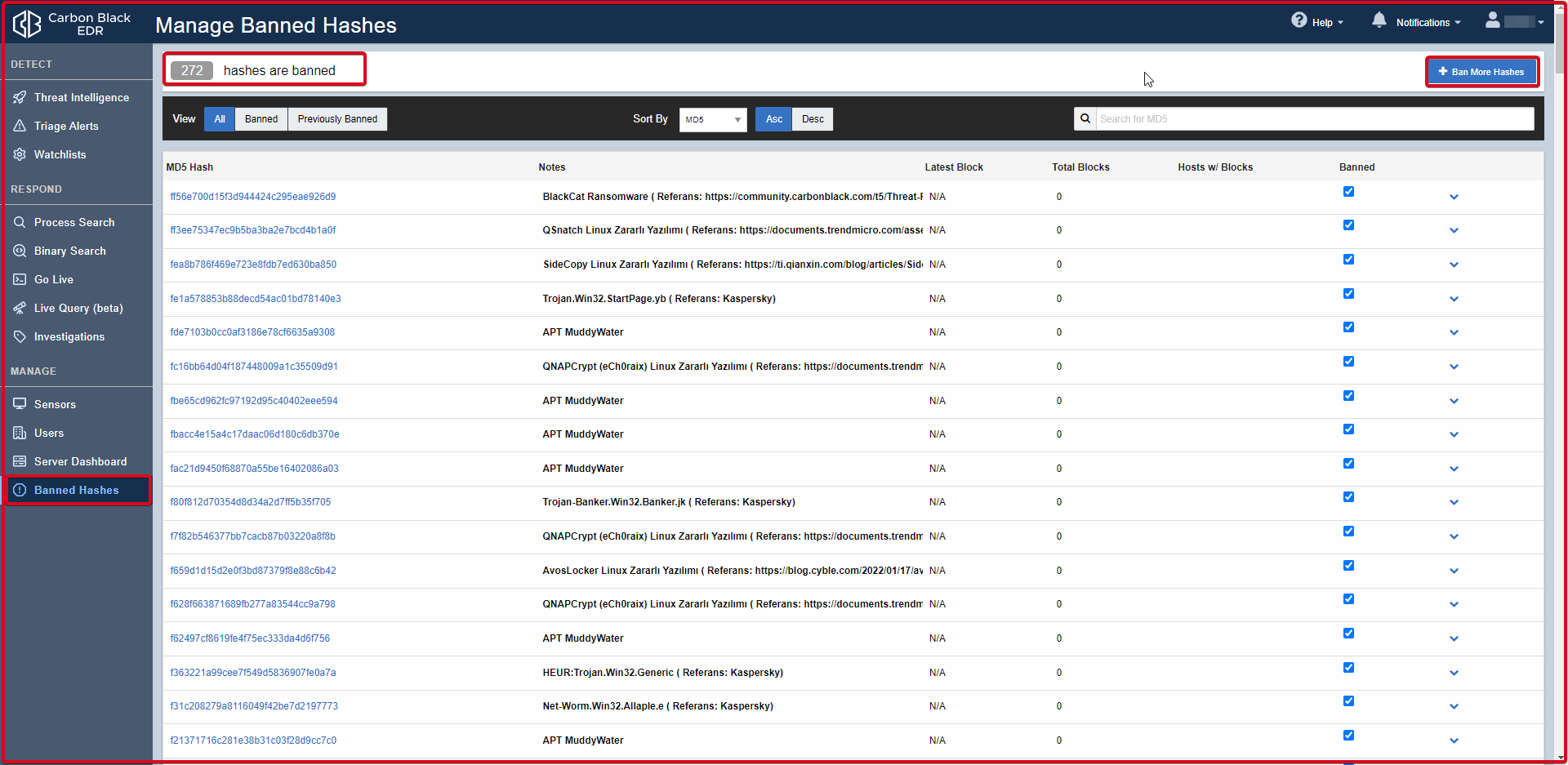
Banned Hashes
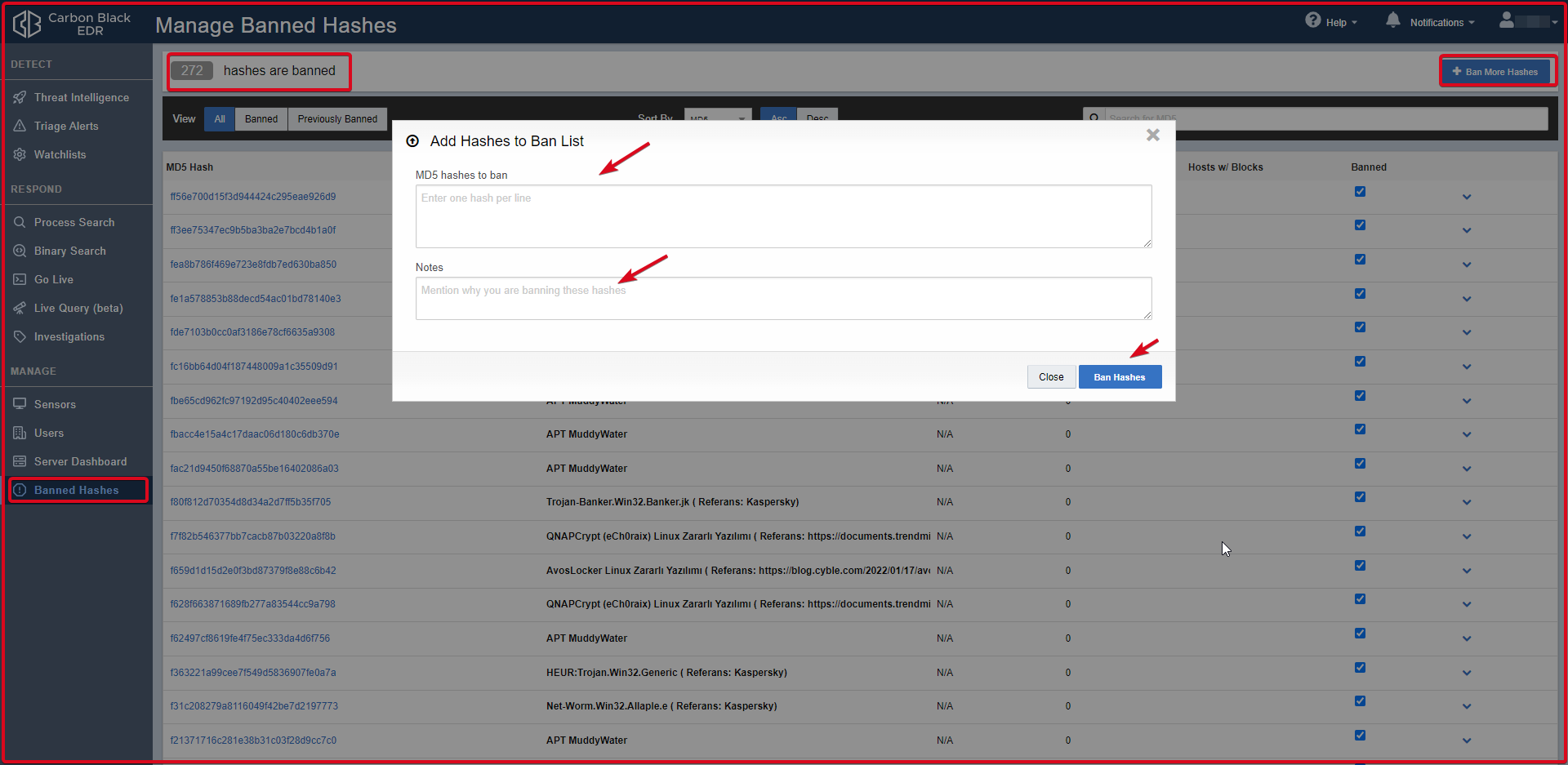
Here we can enter MD5 hashes of applications received from intelligence services or found manually. Enables banned hashes to prevent running on hosts managed by the Carbon Black Response sensor.
Click on the “Ban More Hashes” button in the upper right to enter the MD5 hashes of the applications received from the intelligence services or found manually. On the “Add Hashes to Ban List” page, enter the MD5 hash of the application you want to block. You can add notes in the “Notes” tab. Finally, confirm by clicking the “Ban Hashes” button.