We can define Centrify Privileged Access Management (PAM) as a solution that provides authorized access control for hybrid corporate network infrastructures, offering advanced monitoring and reporting with authentication and session recording features. Centrify PAM features with examples as follows.
IDENTITY BROKER SERVICE
It deduplicates all accounts and provides a centralized access layer. Simplifies user authentication, including AD, LDAP and Google cloud directory. It can be accessed by name account instead of complex accounts.
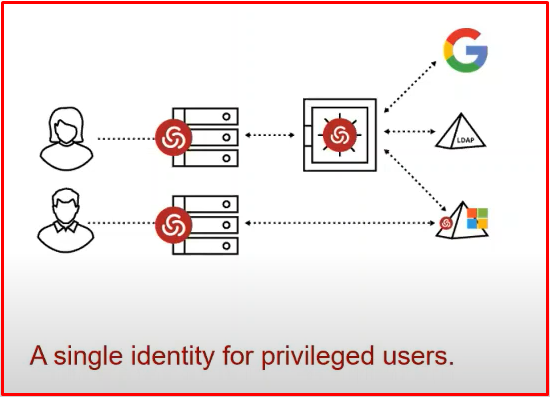
Active Directory-Bridging: With this feature, it can connect to Linux/Unix machines with the name user. You can log in and manage Linux, network and windows devices with a single user.
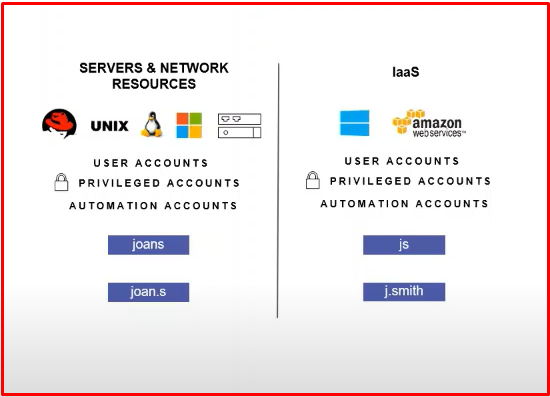
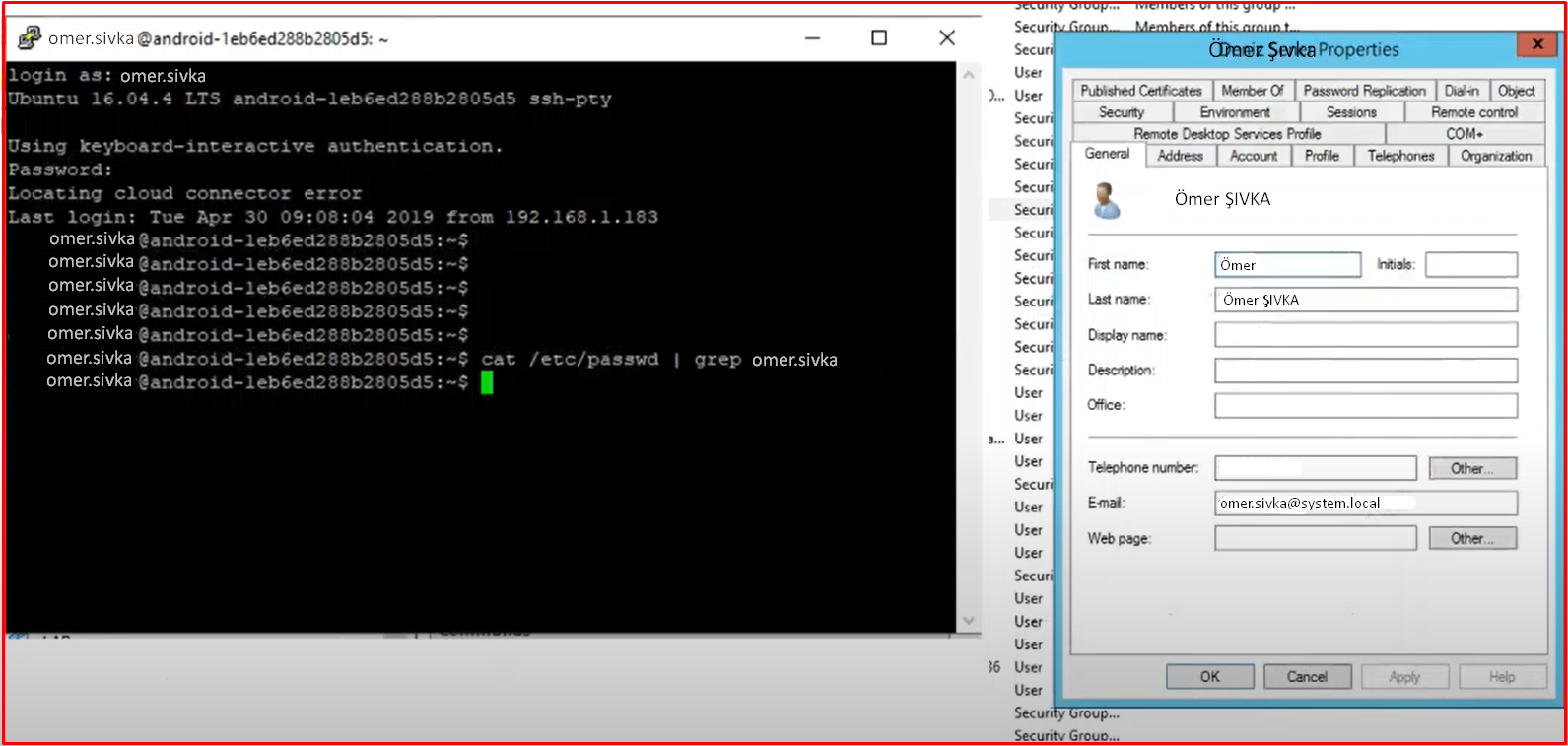
Linux Authentication: Authentication access management for Linux/Unix is also consolidated on Microsoft Active Directory, enabling customers to centralize windows and Linux-based IT structures. In other words, users can log in to a windows computer by typing their AD information in the same way as they log in to a Linux computer. Centrify is the first vendor to integrate Linux and Unix into AD which supports multiple identities for a single user. As can be seen in the example below, the Linux computer is logged in with the putty application with the name user.
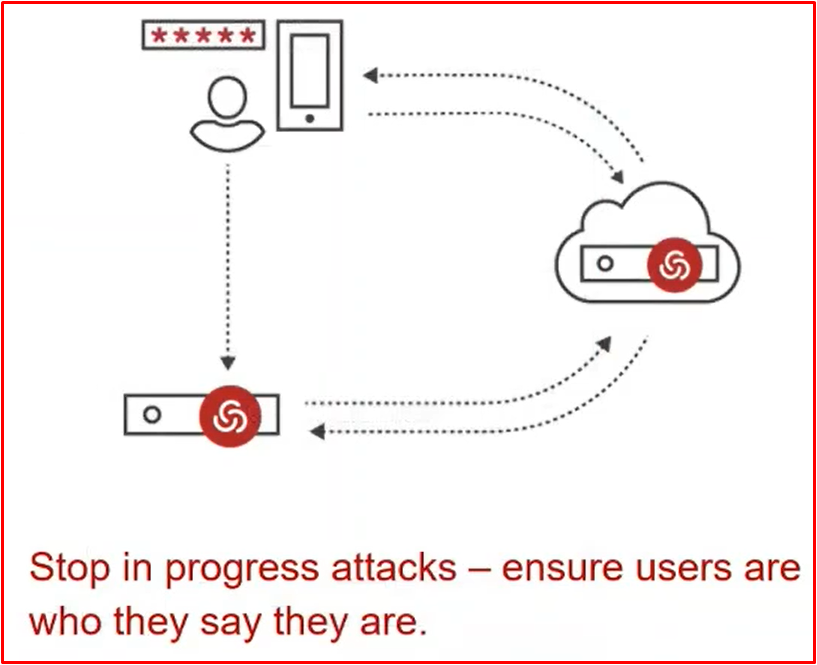
ADAPTİVE MFA FOR PRIVILEGED ACCESS
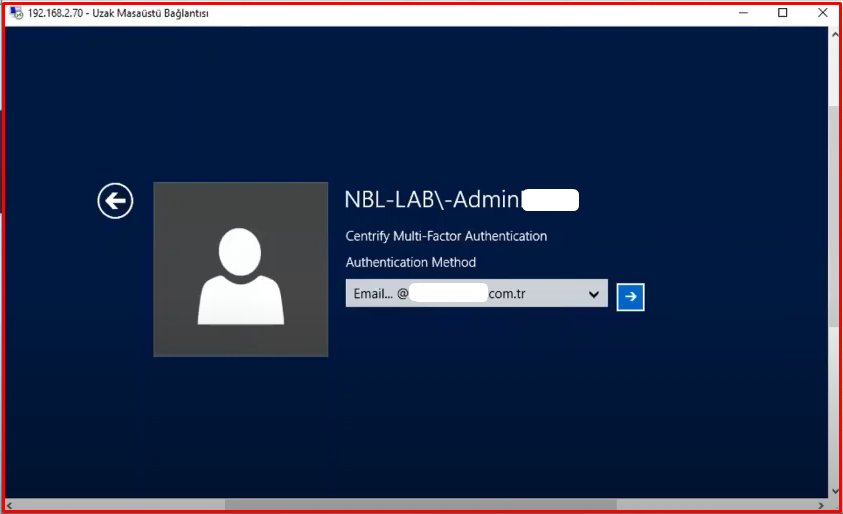
It offers a multi-factor authentication(MFA) feature. It is a feature that is one of the methods of protection from cyber hackers. It is known as multi-factor authentication. When the user will connect to the computer, after entering the password, you can additionally receive MFA authentication such as SMS/OTP/Mail etc. After entering the MFA code, you can log in to the computer. You can provide region-based authorization. We can also say apply MFA to computer connections from outside the company. In the company, we can say MFA application.
In the example below, when logging into a windows server, after typing the user name and password, a screen like a screenshot appears and asks us to choose the Authentication method. Whatever options we have presented to the user for Multi-Factor Authentication, the user chooses one of these options. By holding itself to a second verification, it provides direct and secure access. Thanks to Centrify’s Agent, it can receive these policies when a remote connection is made.
PRIVILEGE ELEVATION
It is the feature of preventing and seeing excessive authorizations. Role and user-based authorization is recommended. It is necessary to give command-based authority to the person who will use an application, instead of admin. Instead of local admin, only that program needs to be authorized. In Linux, you can authorize certain commands instead of root. For example, you can say the “rm” command can run on Linux. In Windows, you can say install certain programs. Thanks to Centrify PAM, the user is given admin authority for these specified features and is an unauthorized user for other cases.

For example, there is a screenshot of how privilege elevation is done on a windows-based server. Normally, when a standard user wants to run this “.bat” file with admin, it will say you are not authorized. You will need to have full privileges in “Run as Administrator“. For this reason, thanks to Centrify, we can run this process as admin by saying “Run with Privilege” only to have admin authority in this process.

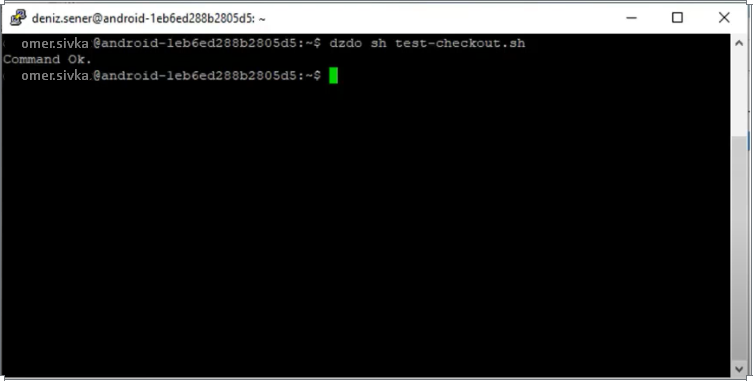
A screenshot for Linux in another interface is available below. Here, for example, if the user needs admin authority, we should have given “sudo” authority. When we gave “sudo” permission, all admin rights would have been given. Here, just like “sudo“, Centrify can make it run as admin by entering the “dzdo” parameter, as we authorize the “sh test-cheskount.sh” process.
SHARED ACCOUNT PASSWORD MANAGEMENT
It is the management of common accounts within the organization. By giving joint accounts to Centrify’s management, he can change his password at certain times. Here we are using Centrify’s web-based interface. The interface can also get or copy the account’s password. We can also restrict them. Here, too, you can only give the user login authorization or we can say that he cannot see the password.
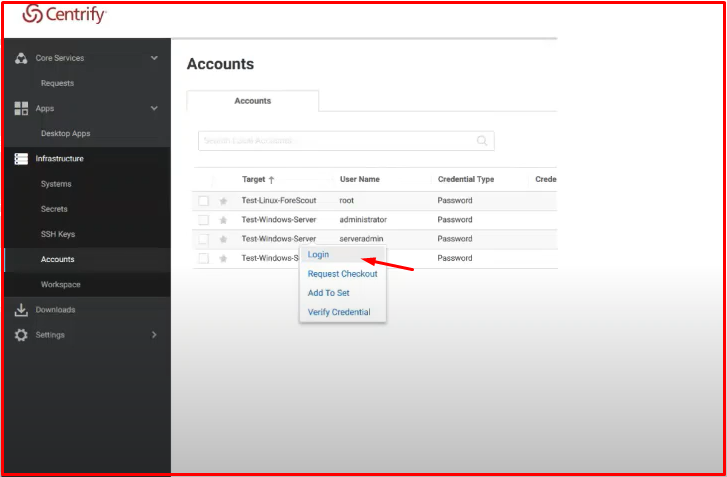
Here we use Centrify’s web-based interface. For example, in the screenshot, this user has permission to see his password. This user can either copy or see the password by right-clicking on the user and saying “Checkout“.

In another scenario, you cannot see the “Checkout” link in the same menu as it appears in the screenshot. He can see the “Request Checkout” menu. This means that the user can no longer see the password, but can log in to the server because he has “login” authority.
APP-TO-APP PASSWORD MANAGEMENT
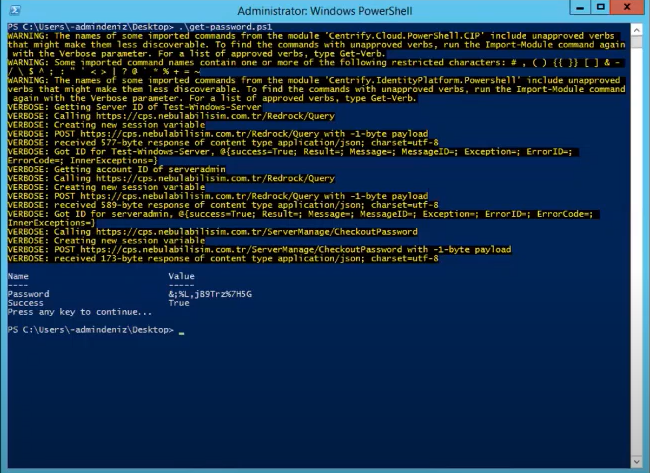
By eliminating the passwords embedded in scripts&batches or applications, instead of storing the password in this area, this application allows the scripts to use the current password via Centrify. Thus, you will not be attacked in any way. For example, there are system team scripts and there are database passwords in them. If someone opens this file, they can see the passwords. Thanks to Centrify’s API code, we can get the password by asking Centrify in scripts and applications.
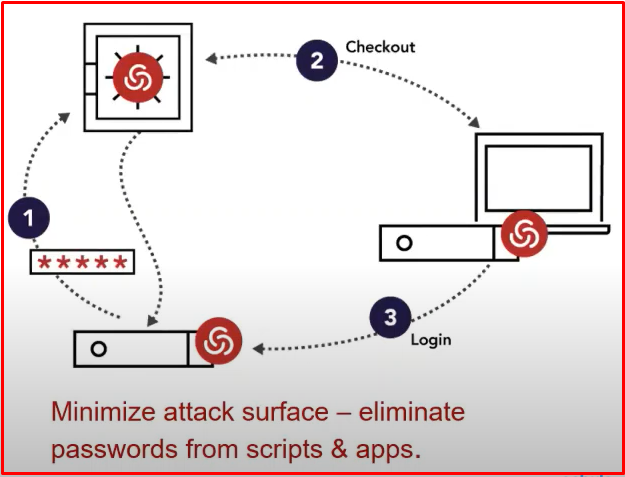
The example below has a PowerShell script. When we run the “get-password.ps1” script here, the script asks Centrify for its current password and gives it the current password. Then the script runs.
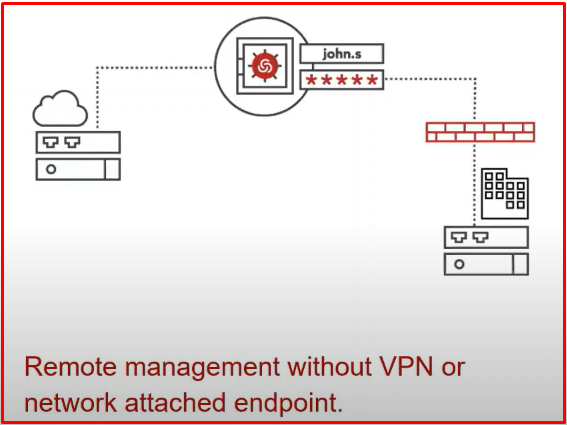
SECURE REMOTE ACCESS
With this feature, IT and external users can be connected via the web without VPN.
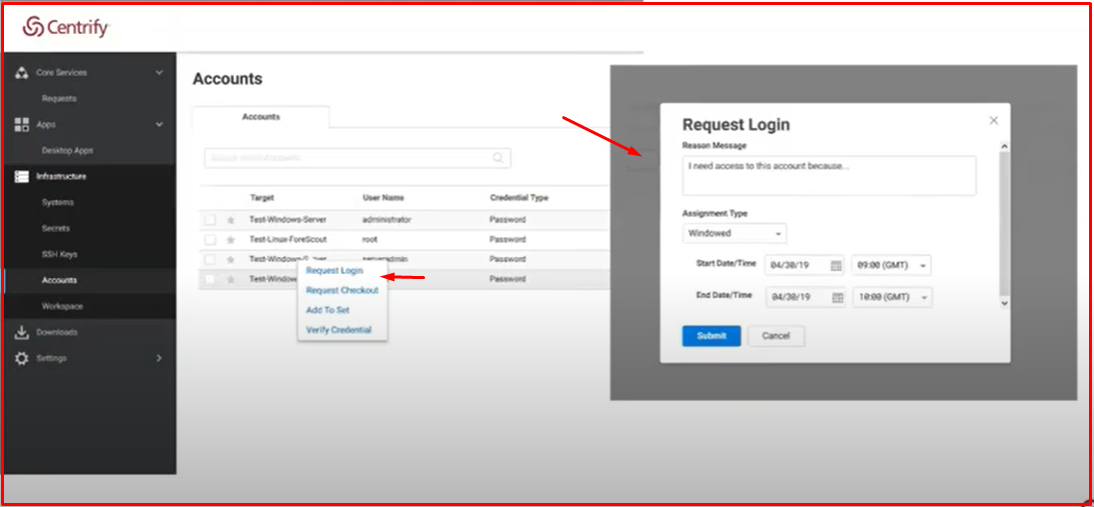
Access Request for Privileged Accounts: Centrify can provide access for external users, but it sends an access request from the administrator via e-mail to access the servers. The manager can also access it after giving approval.
As seen in the example, external users receive a “Request” request to connect to the server. After marking “Request Login“, the user will see a small screen like the one on the right. Then it says why it wants to connect. It enters whatever time interval it is in. Then it “Submits“.
After “submit“, an e-mail is sent to the responsible person as follows. After obtaining this information, it goes to Centrify by clicking on the confirmation screen via e-mail.
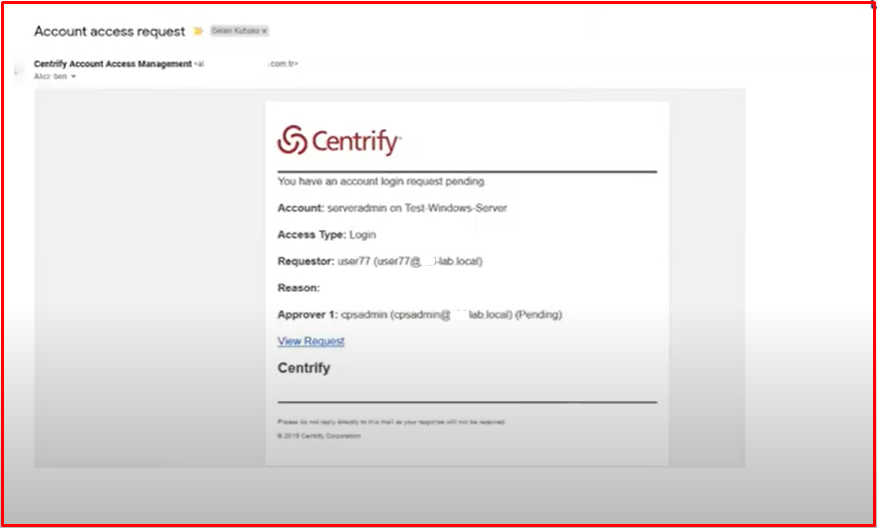
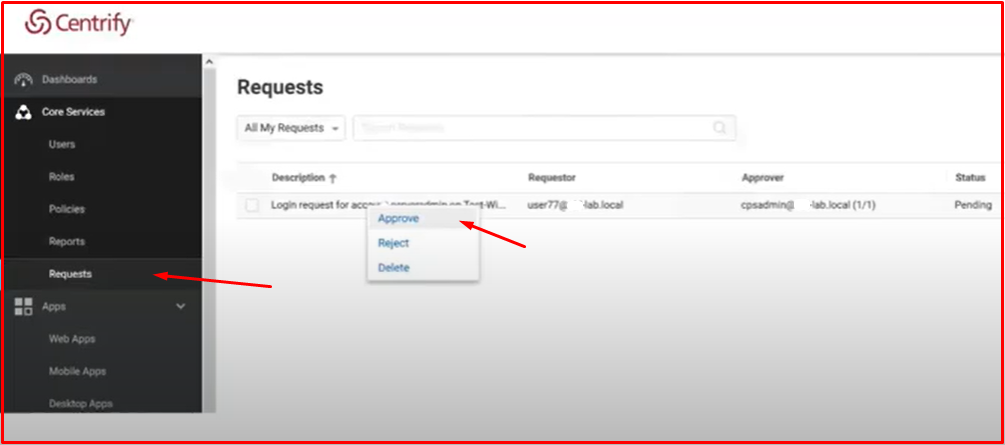
Or Centrify can come directly to the approval screen and give approval by marking “Approve“. If “Reject“, the user will be unable to connect to the server.
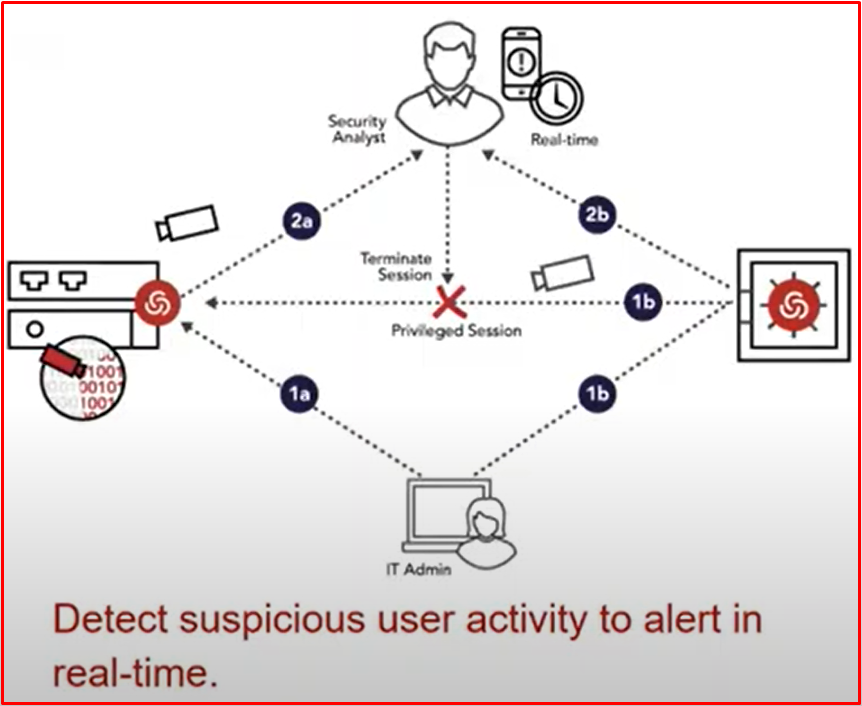
SESSION RECORDING & MONITORING
Thanks to this feature, it can provide real-time viewing of privileged sessions. And if a suspicious session occurs, you can watch that recording. We can track user transactions. If the user creates an unwanted action, we can log out. You can also watch historical recordings.
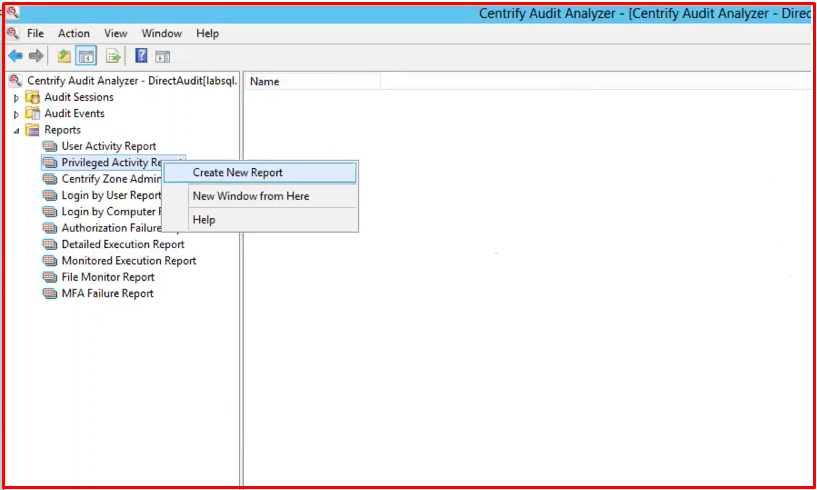
In the example below, you can monitor the session recording as follows. The relevant session record has been opened from Audit Analyzer. On the right is the screen recording of the relevant session. Metadata data appears on the left.

AUDITING AND REPORTING
It also gives good reports as a result of the information it collects in the “Reports” section. Centrify also collects session, MFA, metadata and login information. Since it collects this information, you can get reports with a single click. You can have this information checked by SIEM by sending this information to SIEM. You can create a report on your request on the following report screen. Apart from that, you can access many more reports via the reporting service of mssql.
Reference:




