With the restriction of portable media on the computer, the prevention of the transmission of information, the increase of risks on the systems of portable media that may contain malicious software, the prevention or restricted permission status of these portable media has become very common.
This is, of course, possible with the best DLP systems. Recently, Antivirus software has started to do this job very well. This is possible if you say I want to do it on Windows.
The subject of our article, we will perform the steps of Allowing or Prohibiting the Use of Desired Flash Memory with GPO on Windows Server 2019. First of all, let’s get to know our environment, we have a user computer that is a member of our systemconf.local domain, which is the Windows 10 Pro operating system that we will use in tests.
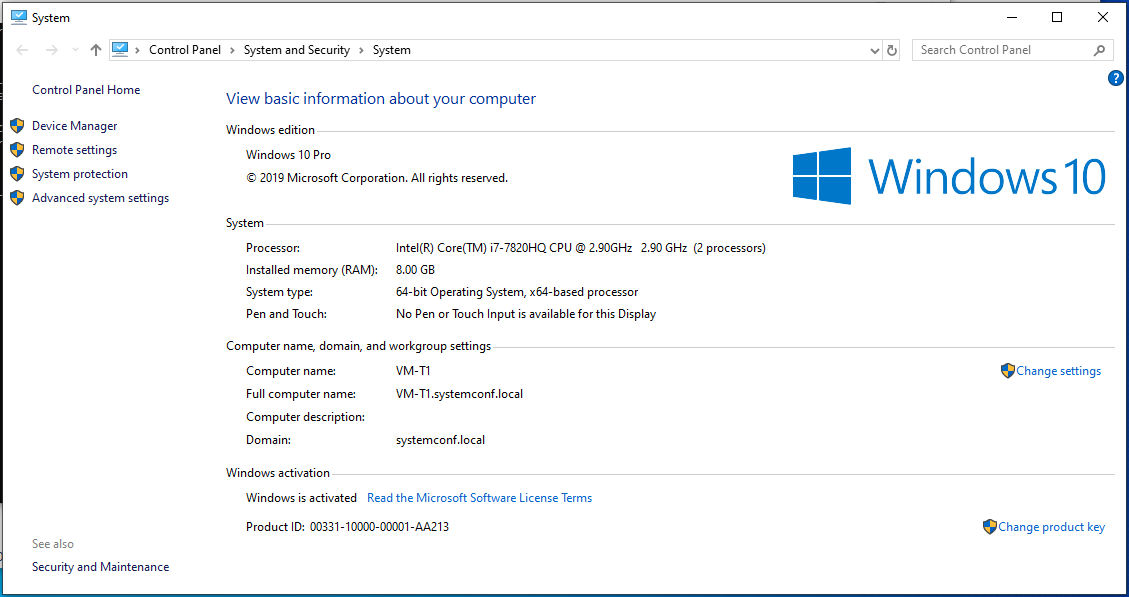
We have a working Flash memory connected to our user computer.
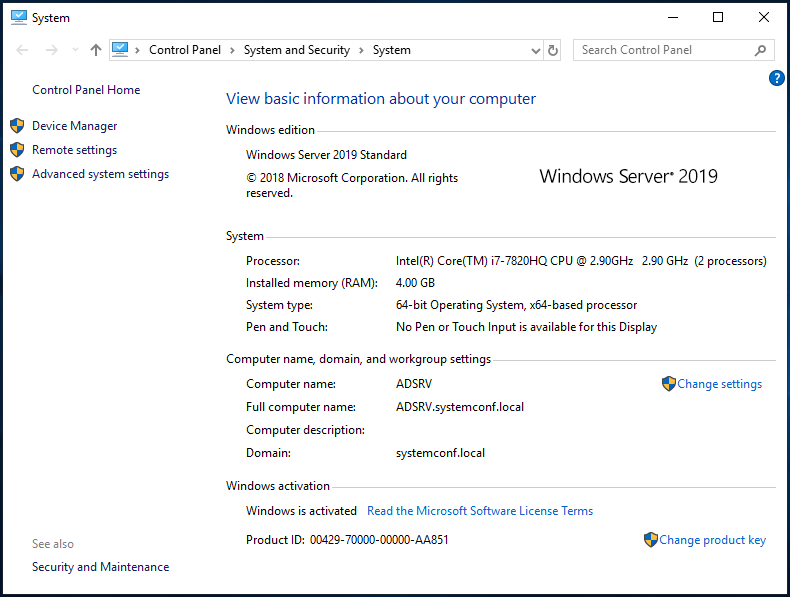
We have a DC server with the Windows Server 2019 operating system where we will press our settings through the GPO and have a domain named systemconf.lokal installed.
There is an organization unit called USB BLOCKING TEST, which includes the user and computer item that we will test on AD.
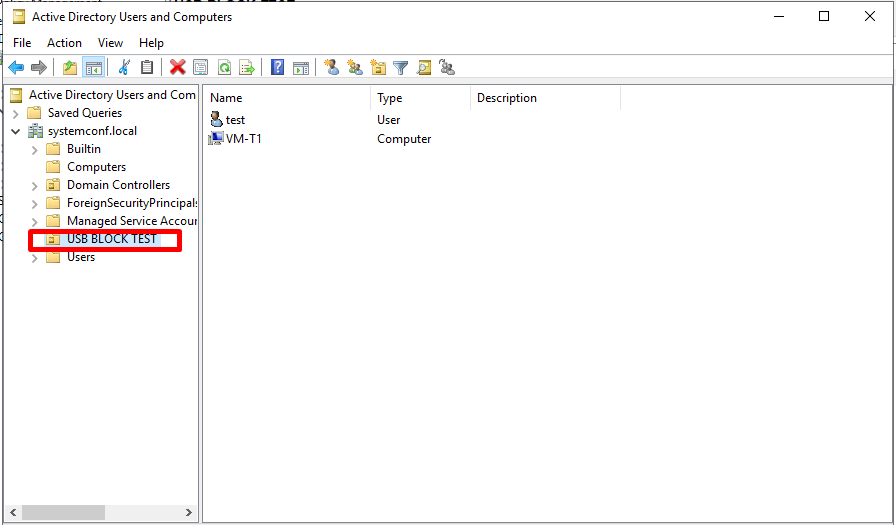
Now that our environment is ready, we open our “Group Policy Management” console to manage the screen on which we can allow or block the desired Flash Memory.

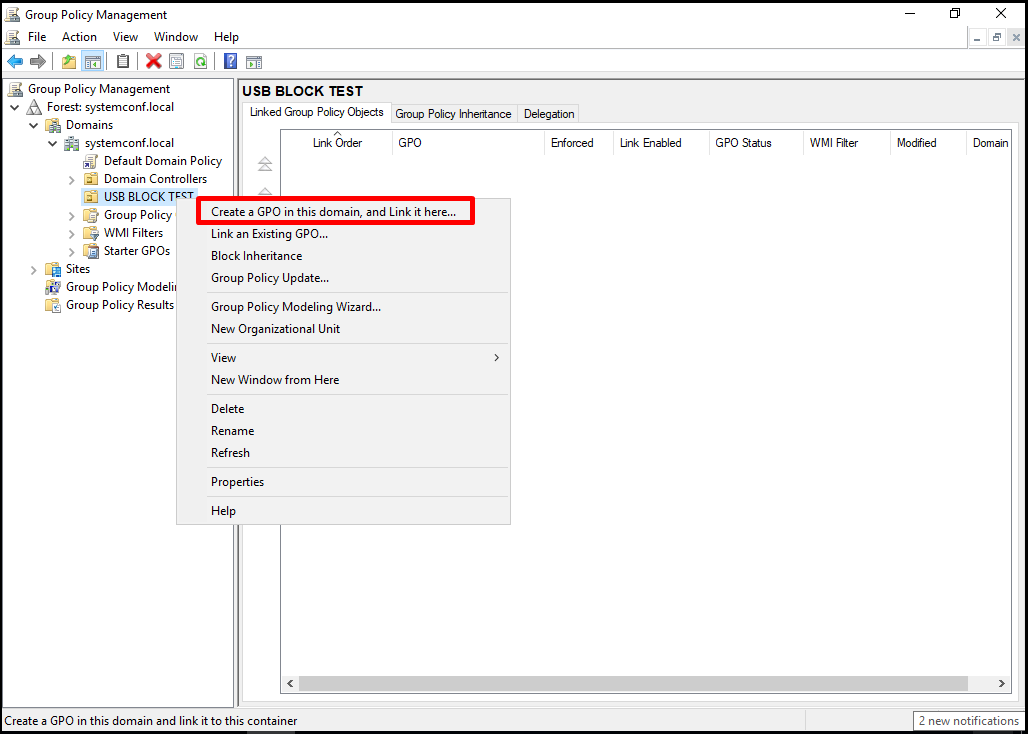
Let’s click on the “Create a GPO in this domain, and Link it here…” drop-down menu to create a GPO that will work depending on the organization unit from the menu that opens by right-clicking on the Organization Unit that we will use for testing.
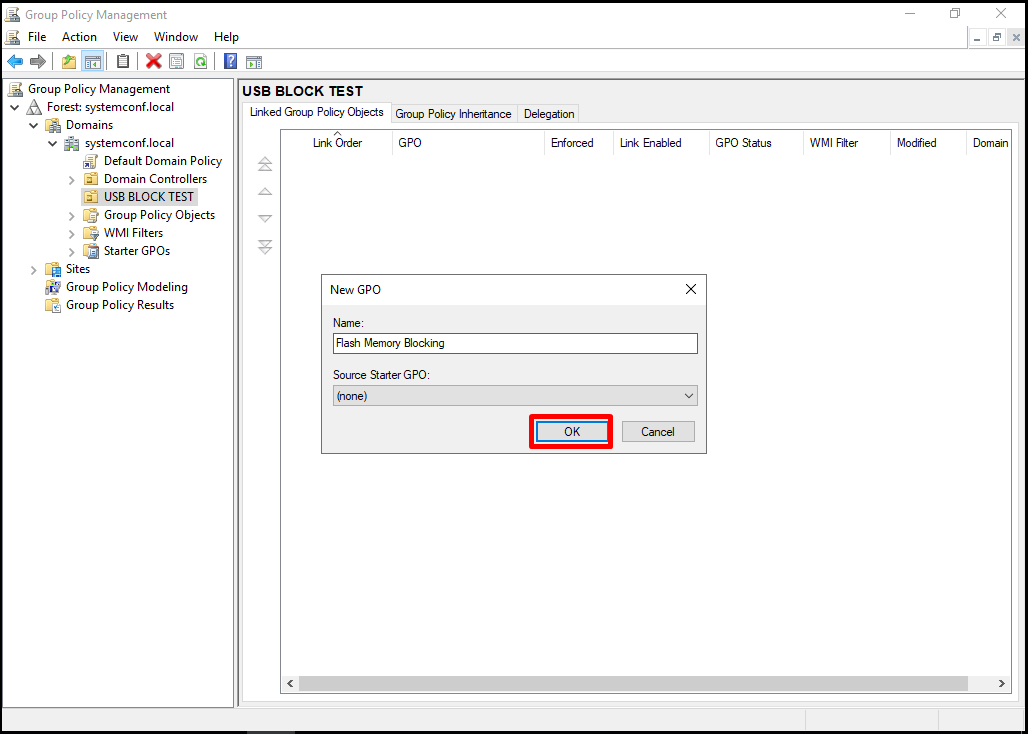
Let’s give a name for the policy to be created and click the “OK” button.
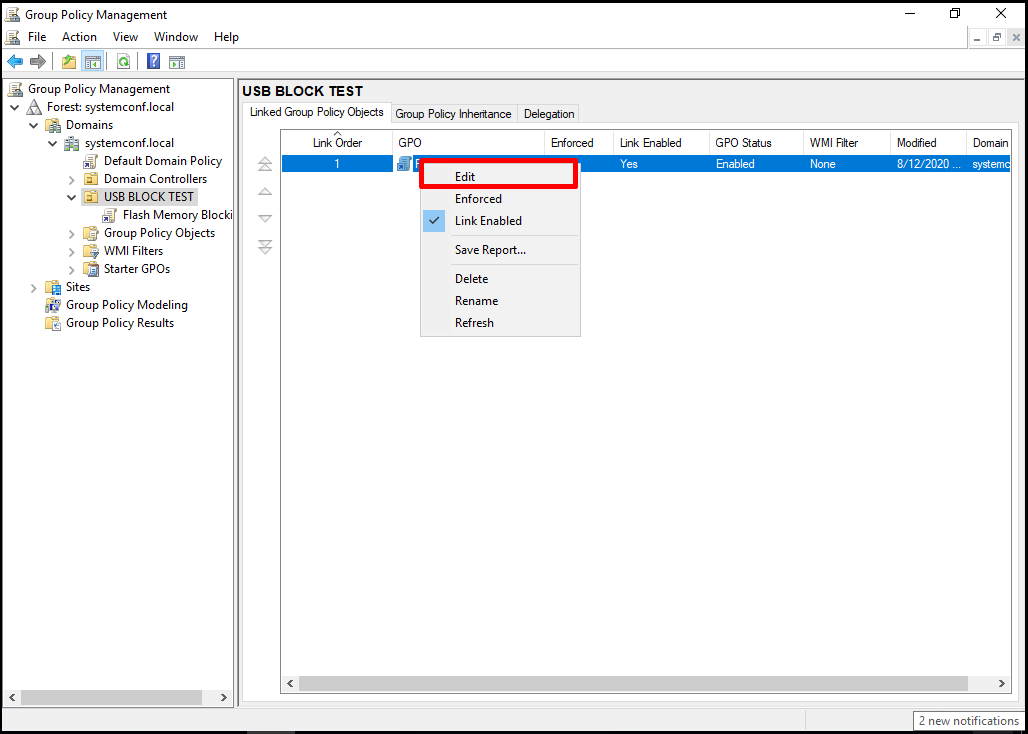
The policy has been created, now we can make the necessary settings on the policies. For this process, let’s right-click on policy and click on the “Edit” drop-down menu.
Let’s go to “Computer Configuration-> Policies -> Administrative Templates Policy-> System-> Device Installation-> Device Installation Restrictions” tab and see our principles. In our scenario, we will proceed by first blocking all Flash memories and then allowing the Flash drives we want to exclude. On the screen that opens, let’s open the principle of “Prevent installation of devices not described by other policy setting“, which is used to prevent the loading of all memories except the ones that are tracked in a different rule.
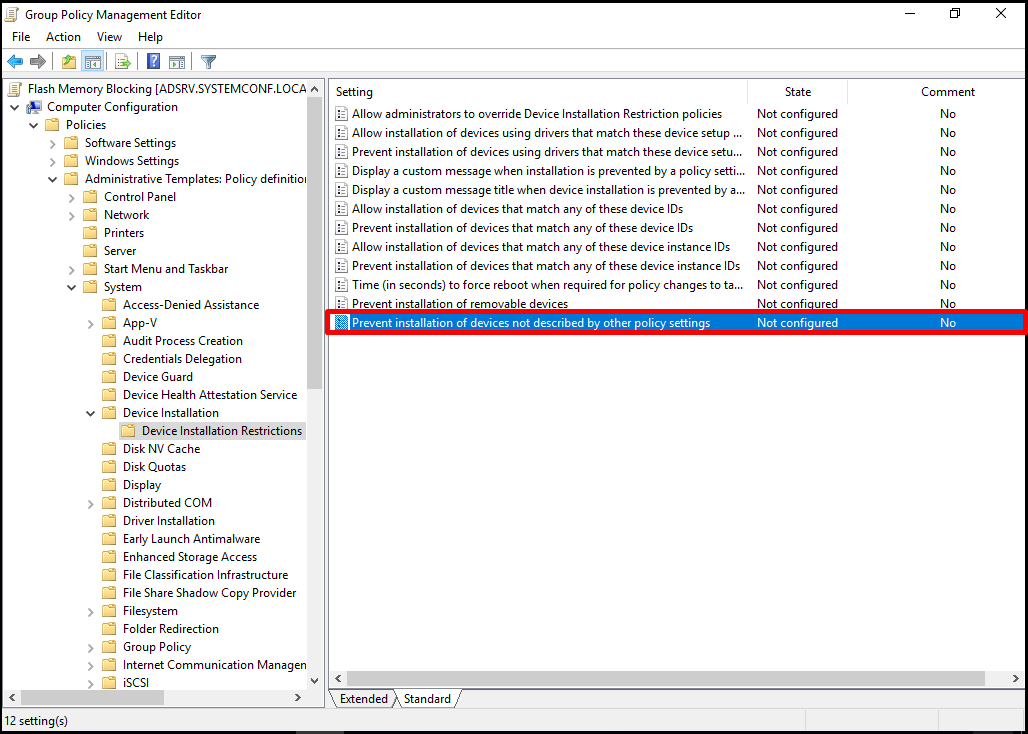
With Enabled, we can activate our policy and turn it off by clicking the “OK” button.
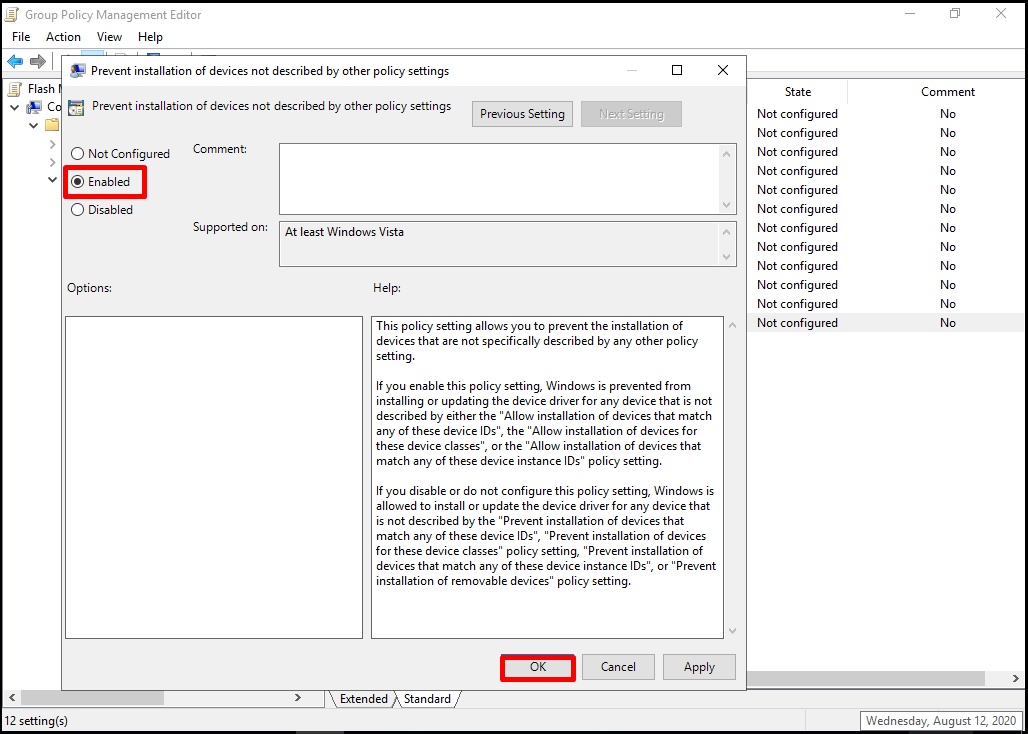
It seems that our policy has become “Enabled”.
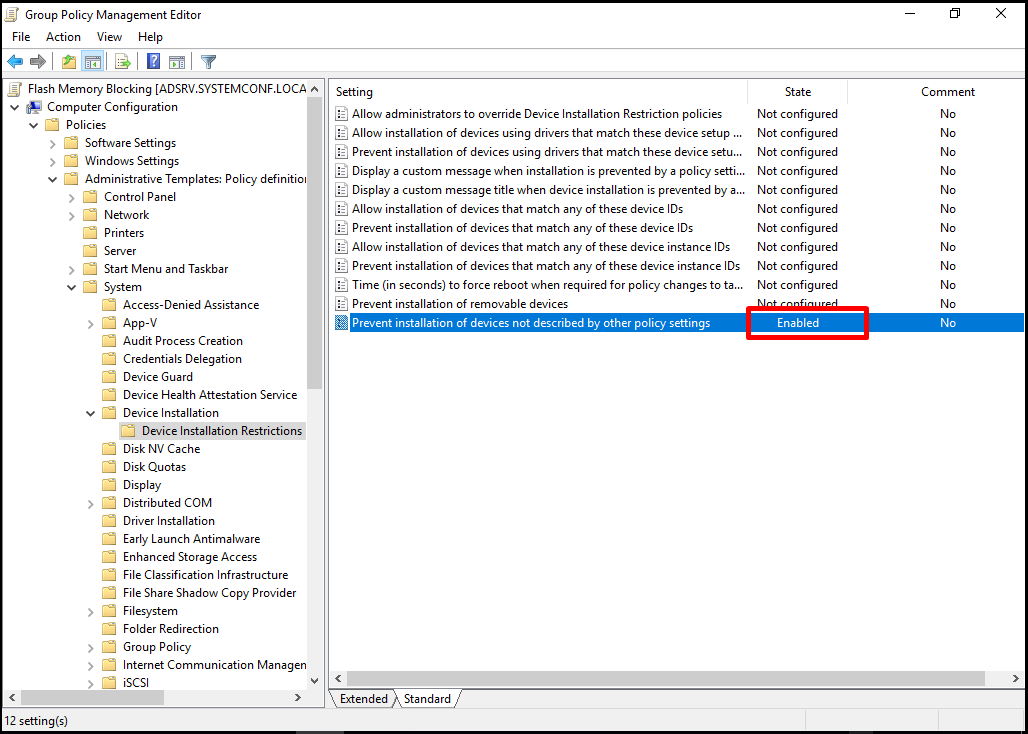
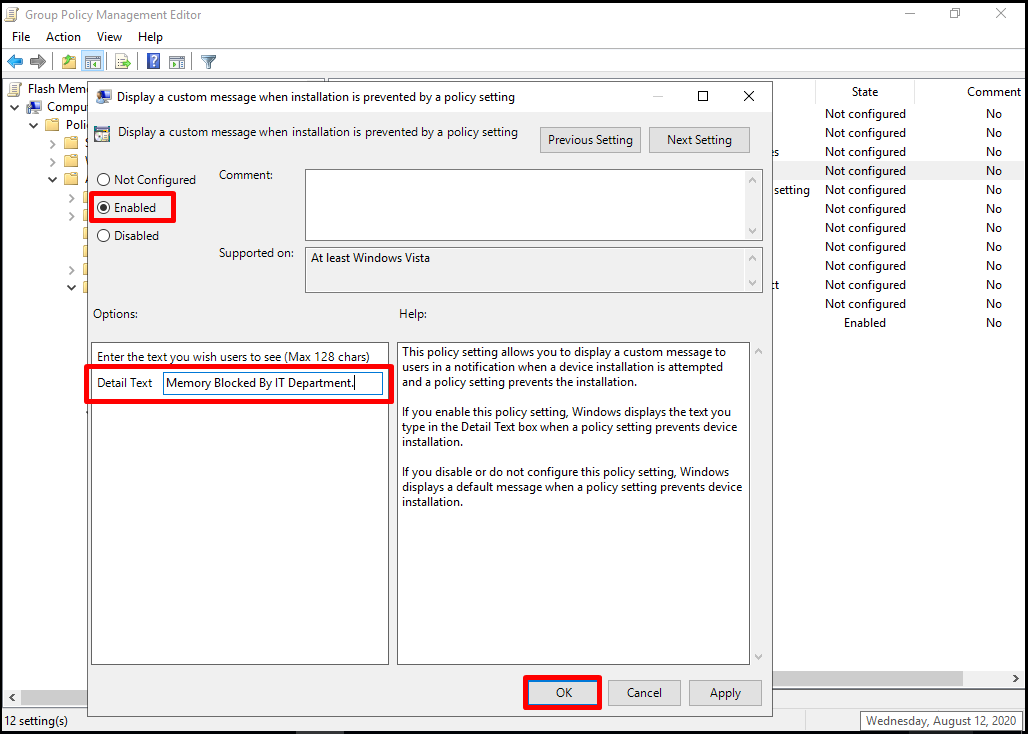
In case of blocked flash memory, we can activate a message feature to inform the user of the situation. We can activate the header and content information of the message. For this process, let’s open our “Display a custom message when installation is prevented by a policy setting” policy.
Let’s enter the content of the message that will appear as a pop-up in the notification area or the user will appear on the screen that opens. After entering the message in the relevant Text field, we can turn our policy to “Enabled” and close this screen with “OK“.
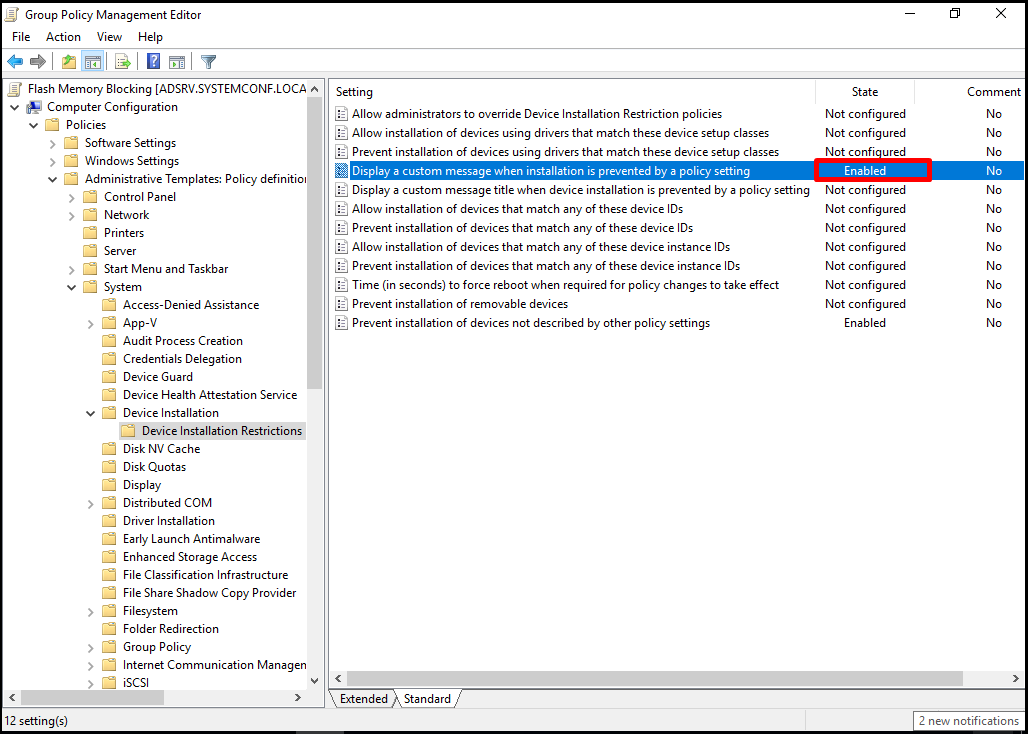
It seems that our policy has become “Enabled“.
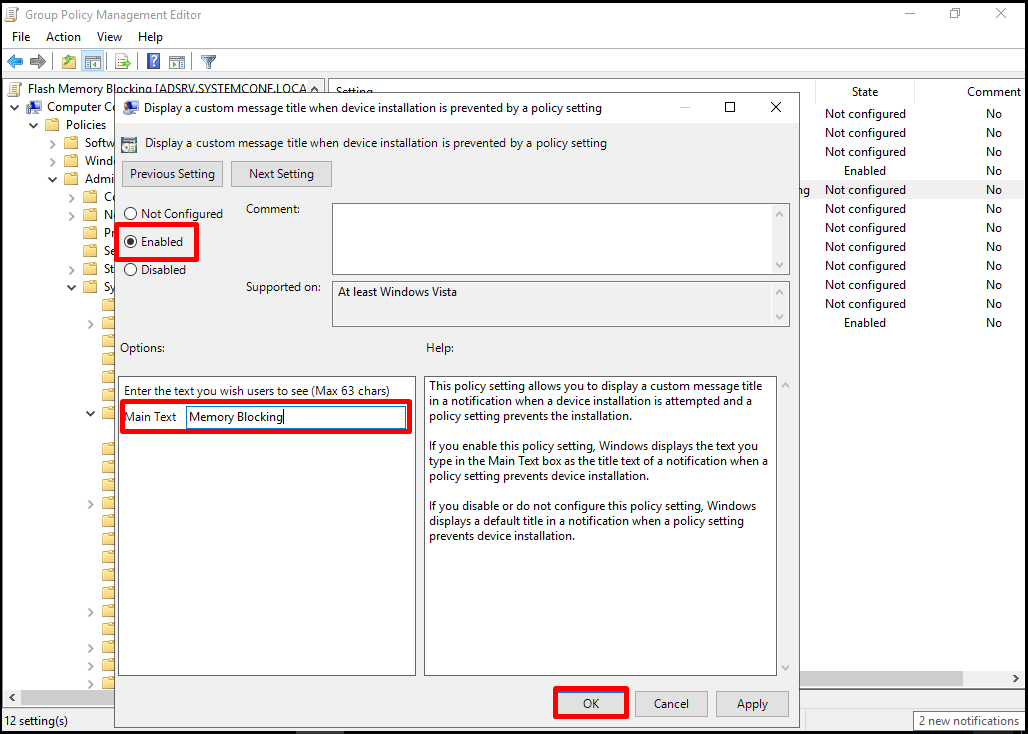
Let’s open our “Display a custom message title when device installation is prevented a policy setting” policy to determine the title of the message screen to be given to users.

Let’s enter the header information in the relevant field, enable our policy, and close this screen with the “OK” button.
It seems that our principle has become effective.
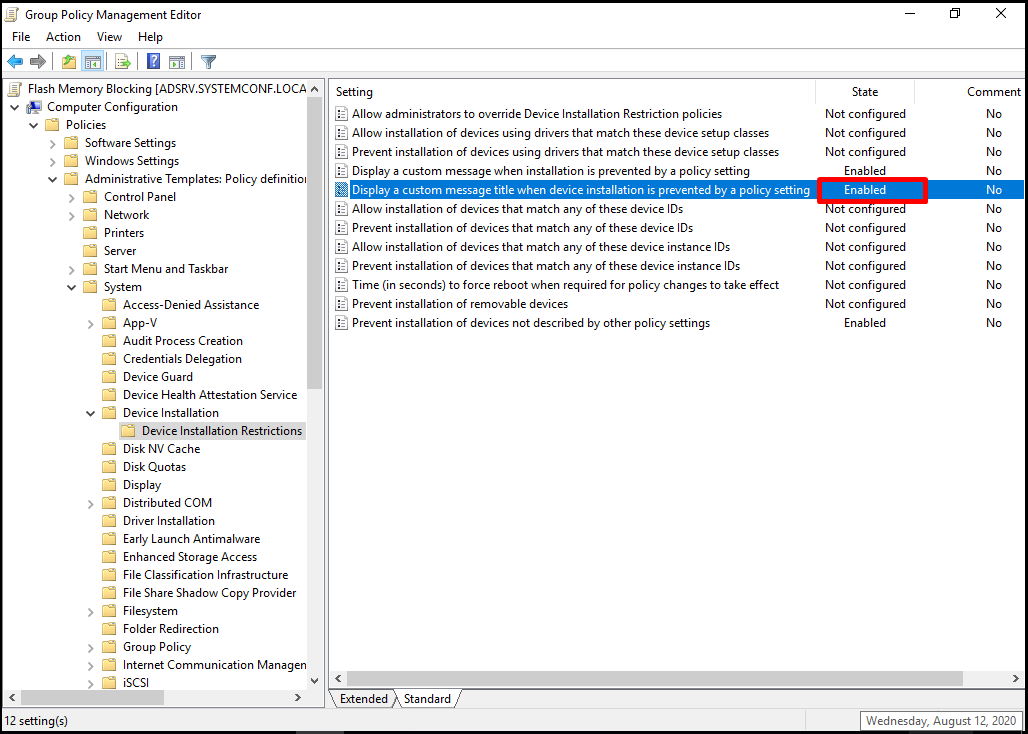
In the sections up to now, we have made the process of blocking all flash memories that do not have definition information in a contrary principle. After this blocking, we determined the title and content of the pop-up or notification message that will inform our users.
Our users will automatically receive these settings during the GPO distribution process. In the case of restarting the computer, this setting will be automatically retrieved through the GPO. However, in order to speed up the process, we will open the command line on the computer and run the “gpupdate /force” command to get the settings instantly.
gpupdate /force
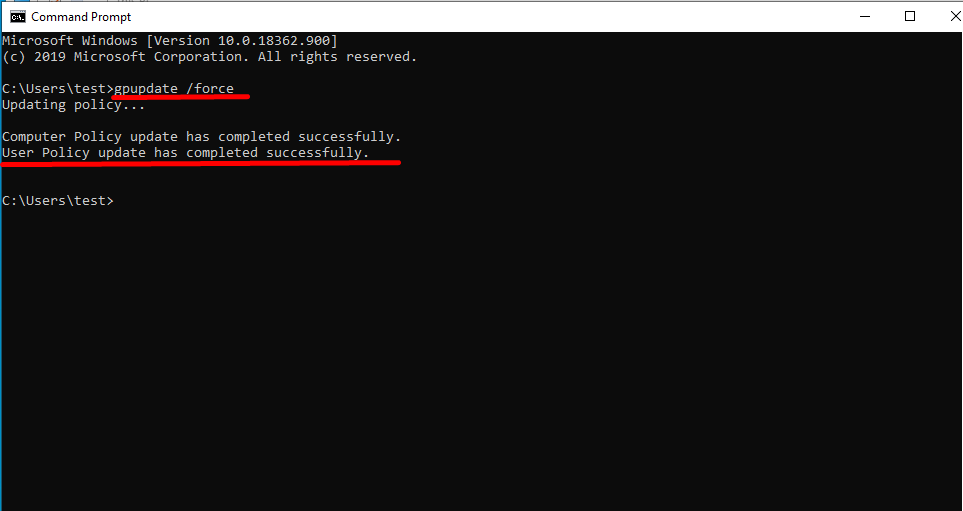
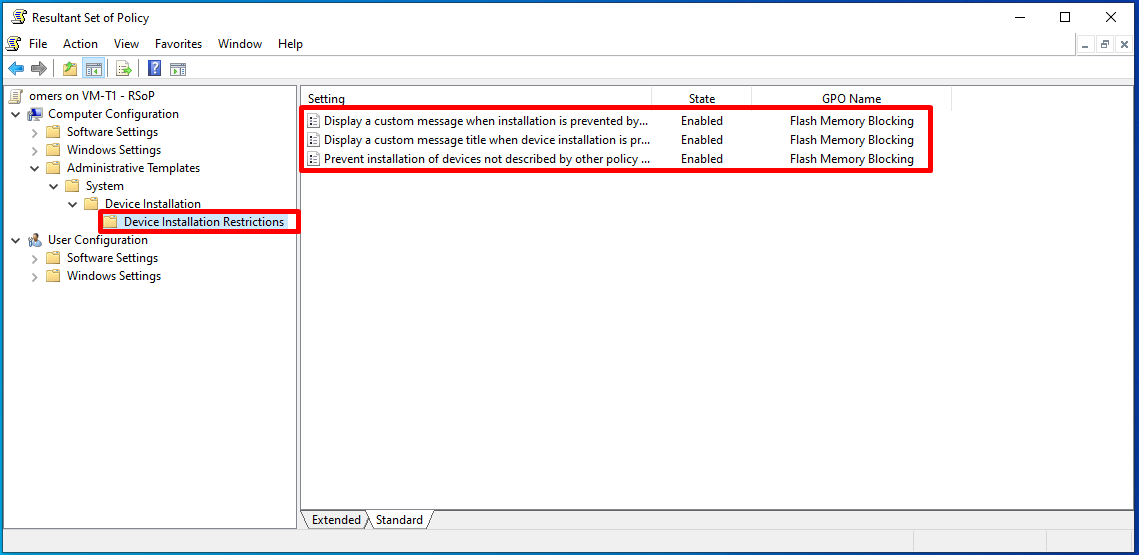
After the relevant process, to see if the user has these settings, we open the console that shows us the policy settings by typing “rsop.msc” in the start menu on the user.

The policies received by the user are checked on this screen.
Let’s go to “Computer Configuration-> Administrative Templates-> System -> Device Installation-> Device Installation Restrictions” on the screen that opens. When we come under the related headings, we can see that the user receives the policies we have configured.