It is stated that the reason behind the recent increase in BEC attacks is the use of Google services by attackers. Due to Covid-19, businesses looking for a reliable and easy method of returning from a traditional office system to digitalization began to use Google services (Forms, Firebase and Docs) frequently. Attackers who were aware of this situation and evaluated the situation started to use Google services for phishing and BEC attacks.
What is BEC (Business E-mail Compromise) Attack?
BEC is a form of fraud targeting companies that make wire transfers and have suppliers abroad. Corporate or public email accounts of executives or senior employees dealing with financing or bank transfer payments are compromised through keyloggers or phishing attacks. In 2016, BEC attacks caused an average of $ 140,000 in damage to companies around the world.
Formerly called Email Man Scam, BEC attackers rely on social engineering tactics to deceive employees and managers. Usually, they impersonate the CEO or any manager authorized to make a wire transfer. Also, fraudsters carefully investigate and closely monitor potential target victims and organizations.
Examples of BEC Attacks
Impersonating a Manager
Attackers pretend to be a manager working in a company’s IT department. Due to the quota issue, they send a fake link so that they cannot receive important emails and they can receive those emails.
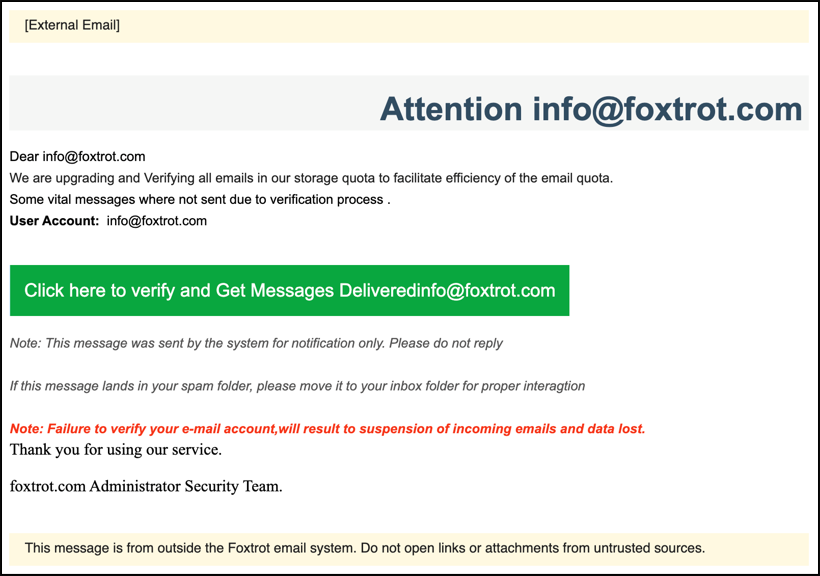
It is directed to a Google Firebase form with the link in the email. Since Firebase form links are Https links, they will not be subject to any security obstacles.
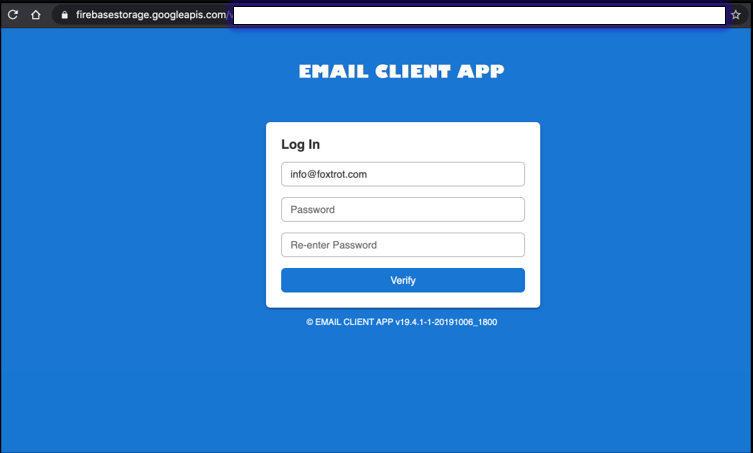
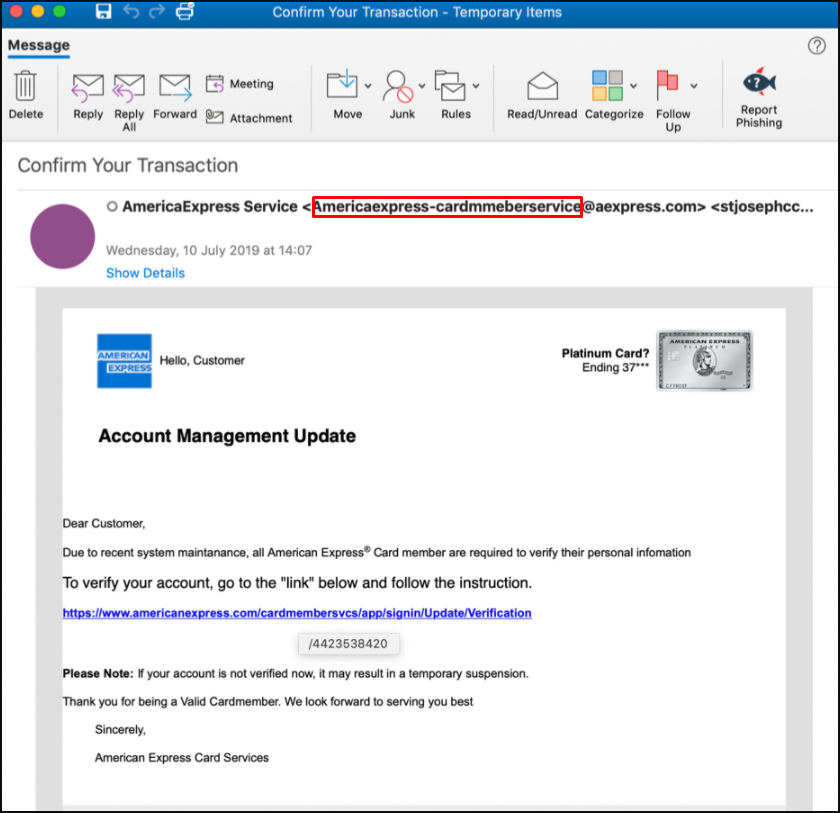
American Express Logo
In a phishing campaign, Google Forms and American Express logos were used to enable targeted people to enter critical information.
Google form
As a result of the link in the incoming e-mail, a Google form like the one below is opened, thus identifying people who can be used for such a scenario. This is a widely used exploration technique.

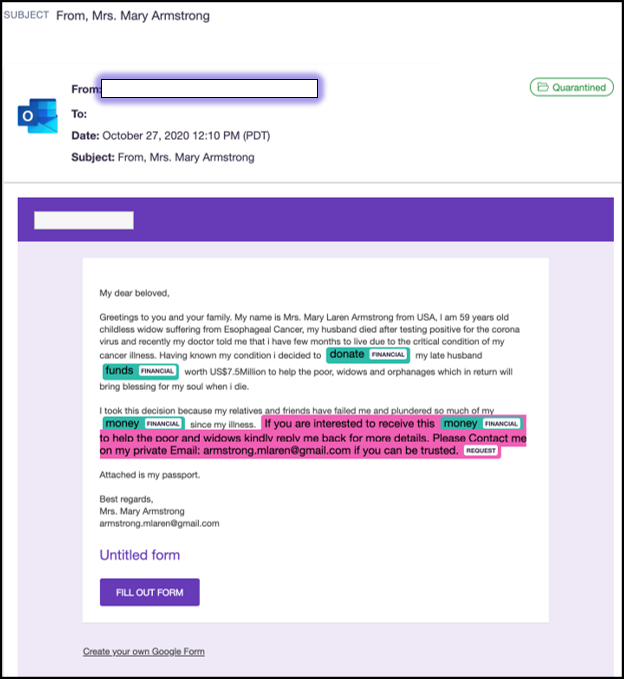
Heritage
A fake email was used stating that she could inherit her wealth and that she was a childless widow:
Fake Office 365
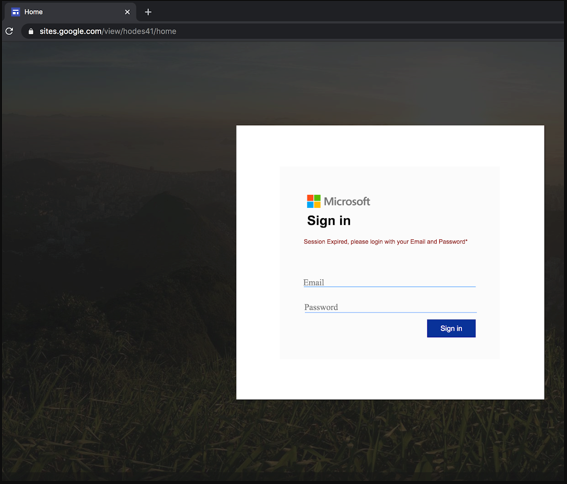
This time, the attackers are using Google services to obtain their Microsoft Teams credentials. Using the scenario that an organization comes from the IT team, the attackers are directed to a page similar to Microsoft Teams with the link in the e-mail. From there, they are redirected to a fake phishing site similar to the Office 365 login portal. The method used below is a legitimate-looking phishing site hosted on Google Sites, a website building tool from Google.
Statement by Google
In a statement made by a Google spokesperson, it is stated that “they are aware of these attack methods and they are trying to take measures to prevent them. It was also explained in the statement that these attacks could be reported as abuse by users.
Effective Preventions Against BEC(Business Email Compromise) Attacks
- Create the DMARC record for your company domain, which conveys the domain’s verification, reporting and compliance to prevent fraudulently and spam emails. Enable two-factor authentication (2FA) on your email accounts. Raise the awareness of your other employees against hackers who will impersonate your employees on vacation
- Enable the use of secure password manager applications.
- Minimize the number of people your company processes and approves wire transfers. Make a list of this authorized personnel available to other employees.
- Make sure that requests for account usage require multi-factor authentication and approval. Verify the new or different payment for your company from at least two different people. Create a maximum amount that can be withdrawn for bank transfers.
- You need to put your cybersecurity protocols on paper. It is important to have a specific cybersecurity policy, from what the employees will or cannot do, to the crisis plan that the company will follow during the cyber attack.
- The sender’s name, email address, usage language within the email address, and unreasonable emails (For example, why would a childless widow mentioned above want to send me millions of dollars?).
- Adopt a comprehensive anti-phishing program that includes a phishing simulation program and a reporting tool to strengthen the cybersecurity understanding and skills of all your employees. Identify real-world phishing scenarios and add them to your phishing, and train your employees on these.
- Hackers often carry out phishing scams or BEC attacks on your employees. Companies need to have software to detect and warn malware against this situation.




