When a connection is made to a system or service, the target system sends a response to this connection request. This message gives some clues about that service/application. During penetration tests, this information is tried to be obtained from the operating system of the target system or the services on it.
With Banner Grabbing, version information of services such as HTTP, FTP, Telnet, SSH, SMTP, SNMP etc. can be obtained. This information can be used for purposes such as abuse in later stages. Banner Grabbing can be performed with various methods. You can see these methods below.
Banner Grabbing with Netcat
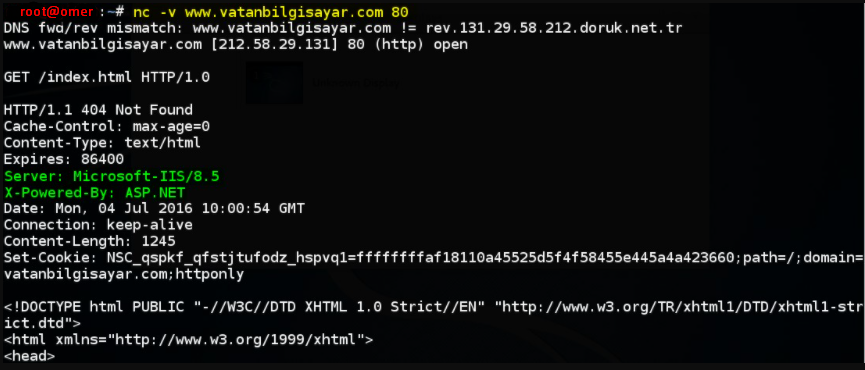
You can get information about HTTP service provided with Netcat tool as follows.
root@omer:~# nc -v www.vatanbilgisayar.com 80
Banner Grabbing with Telnet
You can get information about the HTTP service provided with the Telnet tool as follows. For this purpose, methods such as GET / HEAD can be given.
root@omer:~# telnet www.haberturk.com 80

FTP service
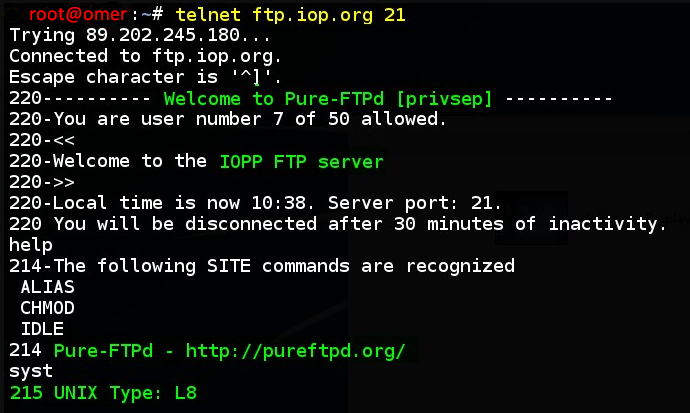
You can obtain information about the FTP service in a similar way with the Telnet tool.
root@omer:~# telnet ftp.iop.org 21
HTTP Banner Grabbing with Nikto
You can get information about the HTTP service provided with the Nikto tool as follows.
root@omer:~# nikto -h www.ulusoy.com.tr

Banner Grabbing with Nmap
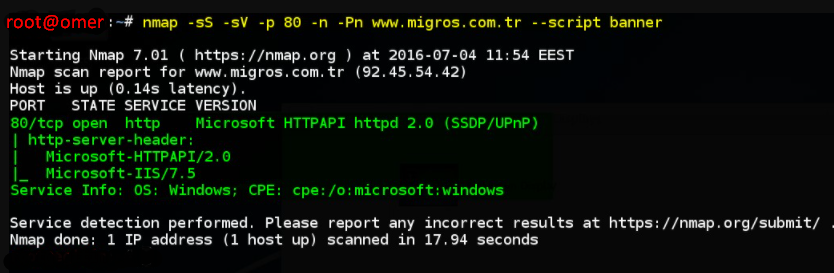
You can get information about the HTTP service provided with the “banner” script of the Nmap tool as follows.
root@omer:~# nmap -sS -sV -p 80 -n -Pn www.migros.com.tr --script banner
HTTP Banner Grabbing with cURL
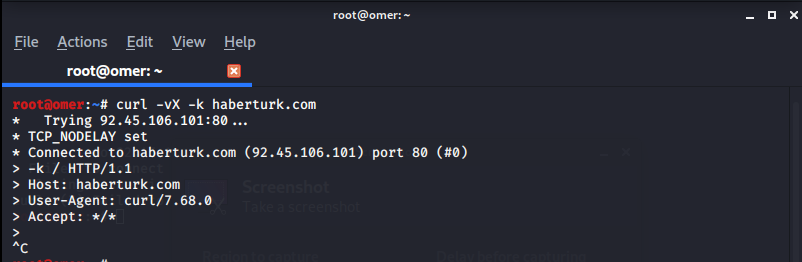
You can get information about the HTTP service provided with the cURL tool as follows.
root@omer:~# curl -vX -k haberturk.com
Banner Grabbing with Metasploit
You can get information about the SSH service provided with the Metasploit ssh_version module as follows.
msf > use scanner/ssh/ssh_version msf auxiliary(ssh_version) > show options msf auxiliary(ssh_version) > set RHOSTS 100.100.200.7 msf auxiliary(ssh_version) > run





