A vulnerability in sudo, a critical and ubiquitous open-source utility used in Linux and Unix operating systems, could allow unprivileged local users to gain root privileges (without authentication) on a vulnerable host.

Openness only allows privilege escalation, not remote code execution. This vulnerability can be exploited by attackers who aim to compromise Linux systems and manage to gain access. For example, brute force attacks.
Update Sudo
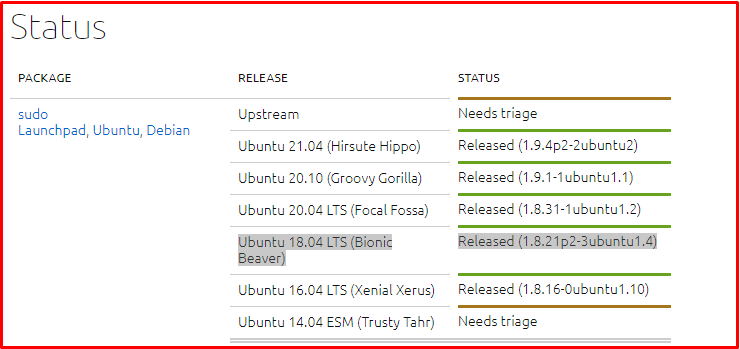
You can fix the problem by updating your system to the latest package versions. Vendor supported patched versions were provided by Ubuntu, RedHat, Debian, Fedora, Gentoo, and others.
Sample Ubuntu Sudo Update
As an example, we have looked at the sudo version in our ubuntu system and the version of our ubuntu system below and updated it.
omer@ubuntu:~$ sudo -V omer@ubuntu:~$ lsb_release -a omer@ubuntu:~$ sudo apt-get update
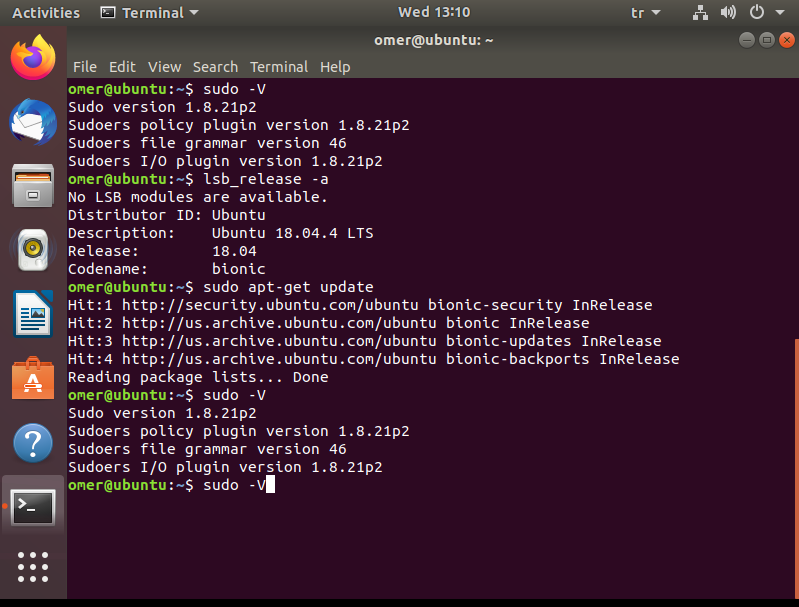
Ubuntu system and sudo version
You can see the versions depending on the version of our Ubuntu system and the sudo version in the picture below.